
Security News
Research
Data Theft Repackaged: A Case Study in Malicious Wrapper Packages on npm
The Socket Research Team breaks down a malicious wrapper package that uses obfuscation to harvest credentials and exfiltrate sensitive data.
FastAdmin is an easy-to-use Admin Dashboard App for FastAPI/Flask/Django inspired by Django Admin.
FastAdmin is an easy-to-use Admin Dashboard App for FastAPI/Django/Flask inspired by Django Admin.
FastAdmin was built with relations in mind and admiration for the excellent and popular Django Admin. It's engraved in its design that you may configure your admin dashboard for FastAPI/Django/Flask easiest way.
FastAdmin is designed to be minimalistic, functional and yet familiar.
If you have any questions that are beyond the scope of the documentation, Please feel free to email us.
Follow the steps below to setup FastAdmin:
Install the package using pip:
Note: For zsh and macos use: pip install fastadmin[fastapi,django]
pip install fastadmin[fastapi,django] # for fastapi with django orm
pip install fastadmin[fastapi,tortoise-orm] # for fastapi with tortoise orm
pip install fastadmin[fastapi,pony] # for fastapi with pony orm
pip install fastadmin[fastapi,sqlalchemy] # for fastapi with sqlalchemy orm
pip install fastadmin[django] # for django with django orm
pip install fastadmin[django,pony] # for django with pony orm
pip install fastadmin[flask,sqlalchemy] # for flask with sqlalchemy
Install the package using poetry:
poetry add 'fastadmin[fastapi,django]' # for fastapi with django orm
poetry add 'fastadmin[fastapi,tortoise-orm]' # for fastapi with tortoise orm
poetry add 'fastadmin[fastapi,pony]' # for fastapi with pony orm
poetry add 'fastadmin[fastapi,sqlalchemy]' # for fastapi with sqlalchemy orm
poetry add 'fastadmin[django]' # for django with django orm
poetry add 'fastadmin[django,pony]' # for django with pony orm
poetry add 'fastadmin[flask,sqlalchemy]' # for flask with sqlalchemy
Configure required settings using virtual environment variables:
Note: You can add these variables to .env and use python-dotenv to load them. See all settings here
export ADMIN_USER_MODEL=User
export ADMIN_USER_MODEL_USERNAME_FIELD=username
export ADMIN_SECRET_KEY=secret_key
Setup FastAdmin for a framework
from fastapi import FastAPI
from fastadmin import fastapi_app as admin_app
app = FastAPI()
app.mount("/admin", admin_app)
from django.urls import path
from fastadmin import get_django_admin_urls as get_admin_urls
from fastadmin.settings import settings
urlpatterns = [
path(f"{settings.ADMIN_PREFIX}/", get_admin_urls()),
]
from flask import Flask
from fastadmin import flask_app as admin_app
app = Flask(__name__)
app.register_blueprint(admin_app, url_prefix="/admin")
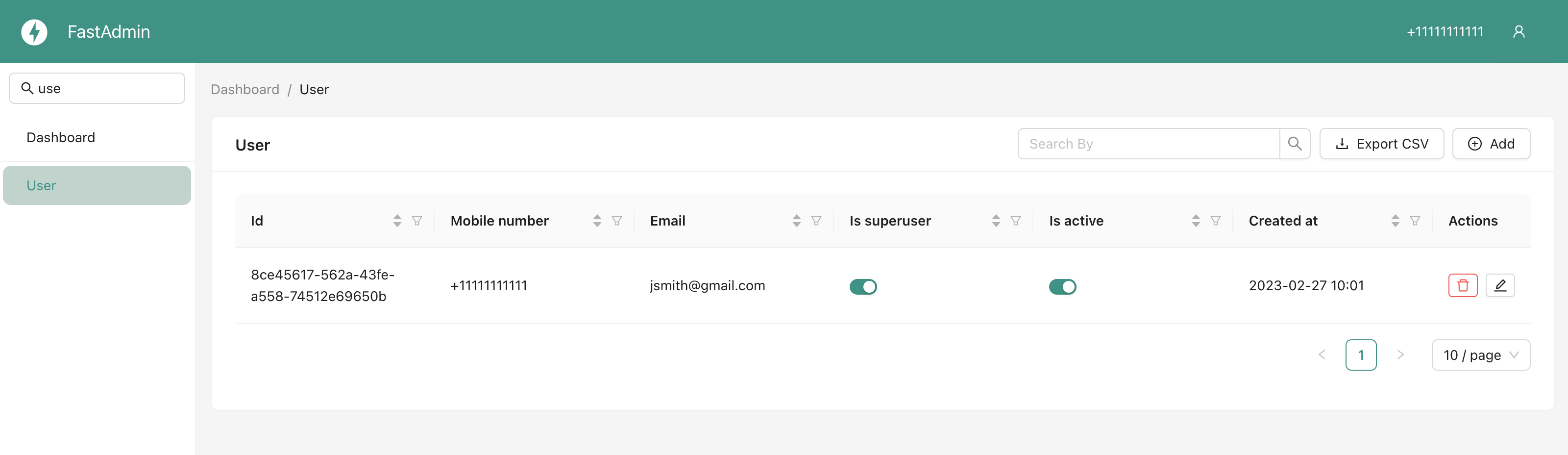
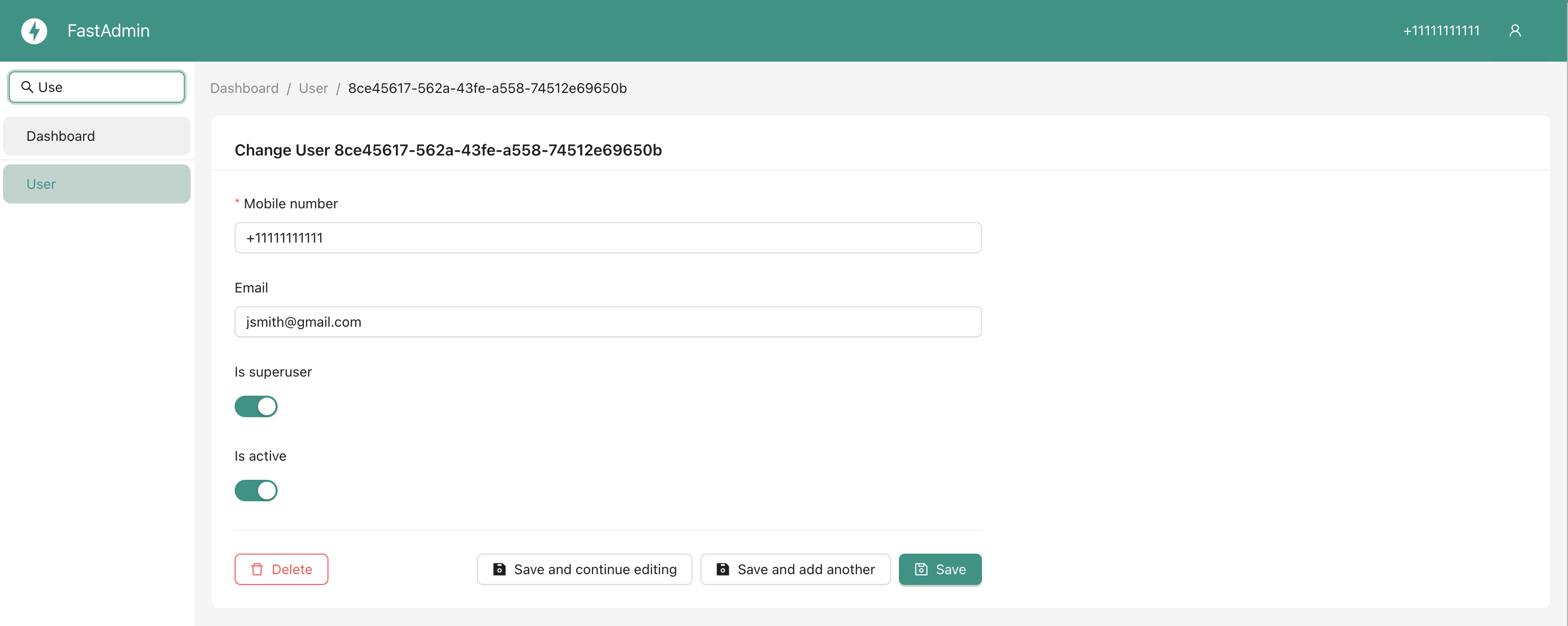
Register ORM models
from uuid import UUID
import bcrypt
from tortoise import fields
from tortoise.models import Model
from fastadmin import TortoiseModelAdmin, register
class User(Model):
username = fields.CharField(max_length=255, unique=True)
hash_password = fields.CharField(max_length=255)
is_superuser = fields.BooleanField(default=False)
is_active = fields.BooleanField(default=False)
def __str__(self):
return self.username
@register(User)
class UserAdmin(TortoiseModelAdmin):
exclude = ("hash_password",)
list_display = ("id", "username", "is_superuser", "is_active")
list_display_links = ("id", "username")
list_filter = ("id", "username", "is_superuser", "is_active")
search_fields = ("username",)
async def authenticate(self, username: str, password: str) -> UUID | int | None:
user = await User.filter(username=username, is_superuser=True).first()
if not user:
return None
if not bcrypt.checkpw(password.encode(), user.hash_password.encode()):
return None
return user.id
from django.db import models
from fastadmin import DjangoModelAdmin, register
class User(models.Model):
username = models.CharField(max_length=255, unique=True)
hash_password = models.CharField(max_length=255)
is_superuser = models.BooleanField(default=False)
is_active = models.BooleanField(default=False)
def __str__(self):
return self.username
@register(User)
class UserAdmin(DjangoModelAdmin):
exclude = ("hash_password",)
list_display = ("id", "username", "is_superuser", "is_active")
list_display_links = ("id", "username")
list_filter = ("id", "username", "is_superuser", "is_active")
search_fields = ("username",)
def authenticate(self, username, password):
obj = User.objects.filter(username=username, is_superuser=True).first()
if not obj:
return None
if not obj.check_password(password):
return None
return obj.id
import bcrypt
from sqlalchemy import Boolean, Integer, String, select
from sqlalchemy.ext.asyncio import async_sessionmaker, create_async_engine
from sqlalchemy.orm import DeclarativeBase, Mapped, mapped_column
from fastadmin import SqlAlchemyModelAdmin, register
sqlalchemy_engine = create_async_engine(
"sqlite+aiosqlite:///:memory:",
echo=True,
)
sqlalchemy_sessionmaker = async_sessionmaker(sqlalchemy_engine, expire_on_commit=False)
class Base(DeclarativeBase):
pass
class User(Base):
__tablename__ = "user"
id: Mapped[int] = mapped_column(Integer, primary_key=True, nullable=False)
username: Mapped[str] = mapped_column(String(length=255), nullable=False)
hash_password: Mapped[str] = mapped_column(String(length=255), nullable=False)
is_superuser: Mapped[bool] = mapped_column(Boolean, default=False, nullable=False)
is_active: Mapped[bool] = mapped_column(Boolean, default=False, nullable=False)
def __str__(self):
return self.username
@register(User, sqlalchemy_sessionmaker=sqlalchemy_sessionmaker)
class UserAdmin(SqlAlchemyModelAdmin):
exclude = ("hash_password",)
list_display = ("id", "username", "is_superuser", "is_active")
list_display_links = ("id", "username")
list_filter = ("id", "username", "is_superuser", "is_active")
search_fields = ("username",)
async def authenticate(self, username, password):
sessionmaker = self.get_sessionmaker()
async with sessionmaker() as session:
query = select(User).filter_by(username=username, password=password, is_superuser=True)
result = await session.scalars(query)
user = result.first()
if not user:
return None
if not bcrypt.checkpw(password.encode(), user.hash_password.encode()):
return None
return user.id
import bcrypt
from pony.orm import Database, PrimaryKey, Required, db_session
from fastadmin import PonyORMModelAdmin, register
db = Database()
db.bind(provider="sqlite", filename=":memory:", create_db=True)
class User(db.Entity): # type: ignore [name-defined]
_table_ = "user"
id = PrimaryKey(int, auto=True)
username = Required(str)
hash_password = Required(str)
is_superuser = Required(bool, default=False)
is_active = Required(bool, default=False)
def __str__(self):
return self.username
@register(User)
class UserAdmin(PonyORMModelAdmin):
exclude = ("hash_password",)
list_display = ("id", "username", "is_superuser", "is_active")
list_display_links = ("id", "username")
list_filter = ("id", "username", "is_superuser", "is_active")
search_fields = ("username",)
@db_session
def authenticate(self, username, password):
user = next((f for f in self.model_cls.select(username=username, password=password, is_superuser=True)), None)
if not user:
return None
if not bcrypt.checkpw(password.encode(), user.hash_password.encode()):
return None
return user.id
See full documentation here.
This project is licensed under the MIT License - see the LICENSE file for details.
FAQs
FastAdmin is an easy-to-use Admin Dashboard App for FastAPI/Flask/Django inspired by Django Admin.
We found that fastadmin demonstrated a healthy version release cadence and project activity because the last version was released less than a year ago. It has 1 open source maintainer collaborating on the project.
Did you know?

Socket for GitHub automatically highlights issues in each pull request and monitors the health of all your open source dependencies. Discover the contents of your packages and block harmful activity before you install or update your dependencies.

Security News
Research
The Socket Research Team breaks down a malicious wrapper package that uses obfuscation to harvest credentials and exfiltrate sensitive data.

Research
Security News
Attackers used a malicious npm package typosquatting a popular ESLint plugin to steal sensitive data, execute commands, and exploit developer systems.

Security News
The Ultralytics' PyPI Package was compromised four times in one weekend through GitHub Actions cache poisoning and failure to rotate previously compromised API tokens.