
Security News
Research
Data Theft Repackaged: A Case Study in Malicious Wrapper Packages on npm
The Socket Research Team breaks down a malicious wrapper package that uses obfuscation to harvest credentials and exfiltrate sensitive data.

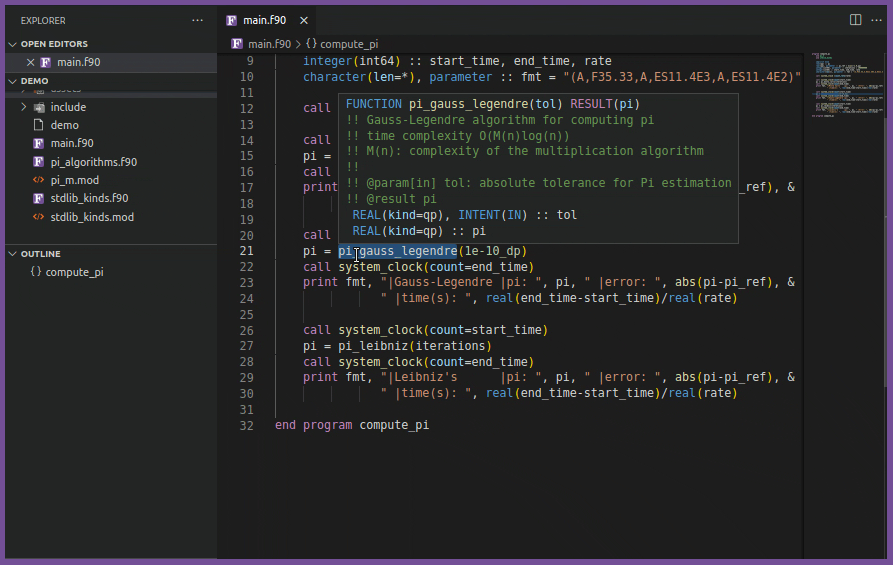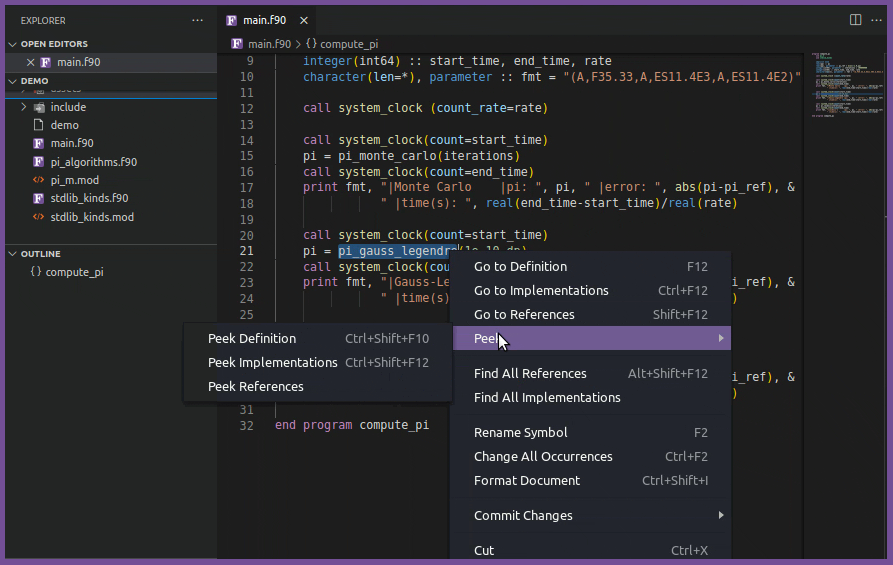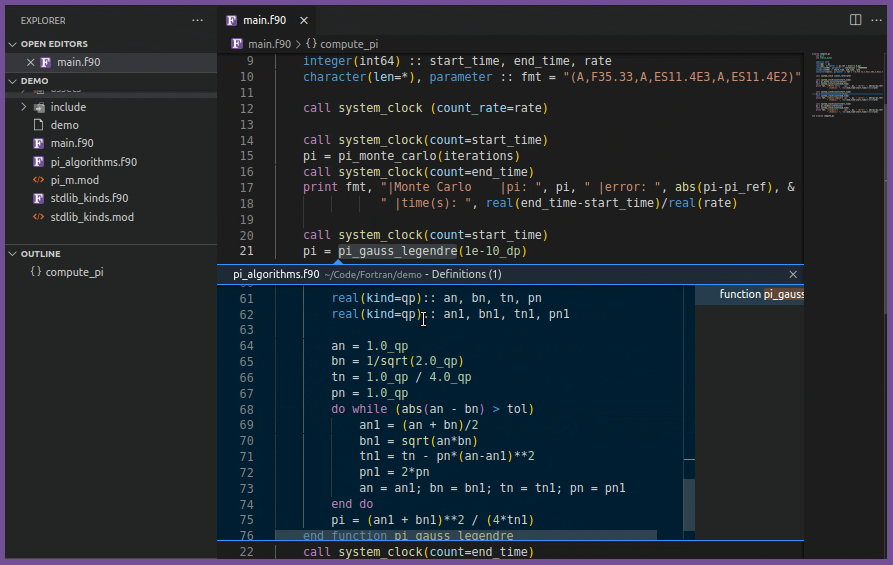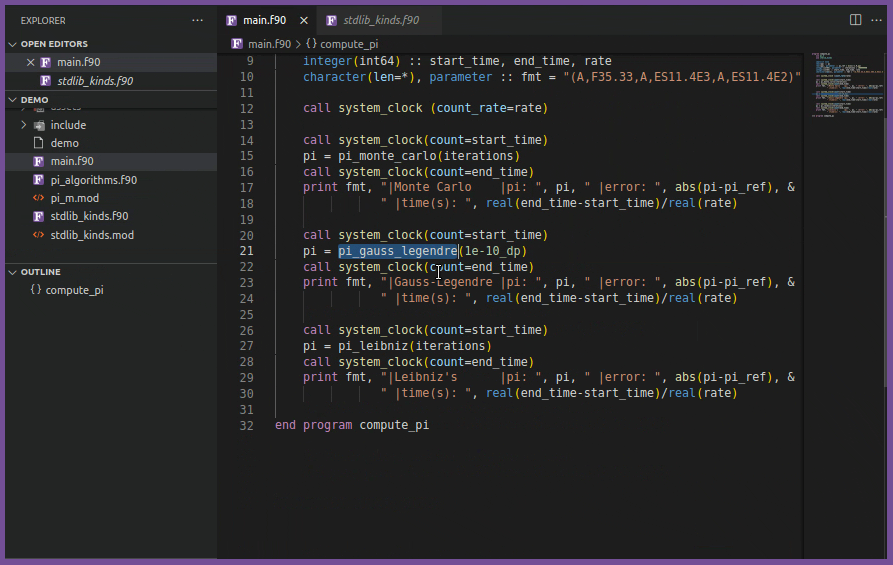
fortls is an implementation of the Language Server Protocol
(LSP) for Fortran using Python (3.7+).
All code editors that support LSP can integrate with fortls see the section
Editor Integration in the documentation.
Some supported code editors include:
Visual Studio Code,
Atom,
Sublime Text,
(Neo)Vim,
and Emacs.
ISO_FORTRAN_ENV GCC 11.2.0ISO_C_BINDING GCC 11.2.0IEEE_EXCEPTIONS, IEEE_ARITHMETIC, IEEE_FEATURES GCC 11.2.0OMP_LIB, OMP_LIB_KINDS v5.0OPENACC, OPENACC_KINDS v3.1TYPE/CLASS definition
(only if visible in project)USE statementCONTAINS, IMPLICIT, IMPORT)The full documentation for fortls can be found at
fortls.fortran-lang.org.
pip install fortls
conda install -c conda-forge fortls
for more information about the Anaconda installation see
It is NOT recommended having fortls and fortran-language-server
simultaneously installed, since they use the same executable name. If you are having trouble
getting fortls to work try uninstalling fortran-language-server and reinstalling fortls.
With pip
pip uninstall fortran-language-server
pip install fortls --upgrade
or with Anaconda
conda uninstall fortran-language-server
conda install -c conda-forge fortls
fortls can be configured through both the command line e.g.
fortls --hover_signature or through a Configuration json file.
The two interfaces are identical and a full list of the available options can
be found in the Documentation
or through fortls -h
An example for a Configuration file is given below
{
"incremental_sync": true,
"lowercase_intrinsics": true,
"hover_signature": true,
"use_signature_help": true,
"excl_paths": ["tests/**", "tools/**"],
"excl_suffixes": ["_skip.f90"],
"include_dirs": ["include/**"],
"pp_suffixes": [".F90", ".h"],
"pp_defs": { "HAVE_HDF5": "", "MPI_Comm": "integer" }
}
| Request | Description |
|---|---|
workspace/symbol | Get workspace-wide symbols |
textDocument/documentSymbol | Get document symbols e.g. functions, subroutines, etc. |
textDocument/completion | Suggested tab-completion when typing |
textDocument/signatureHelp | Get signature information at a given cursor position |
textDocument/definition | GoTo definition/Peek definition |
textDocument/references | Find all/Peek references |
textDocument/documentHighlight | Same as textDocument/references |
textDocument/hover | Show messages and signatures upon hover |
textDocument/implementation | GoTo implementation/Peek implementation |
textDocument/rename | Rename a symbol across the workspace |
textDocument/didOpen | Document synchronisation upon opening |
textDocument/didSave | Document synchronisation upon saving |
textDocument/didClose | Document synchronisation upon closing |
textDocument/didChange | Document synchronisation upon changes to the document |
textDocument/codeAction | Experimental Generate code |
fortls has reached a point where it is feature complete and stable enough to be used in many modern Fortran projects without any issues.
It does however still have fundamental limitations,
namely its ability to understand all Fortran syntax and semantics that has been used throughout the 65+ years of the language. The good news is that we have a plan to address this issue!
We are excited to announce that we are working on creating a new Fortran Language Server based on the actively developed LFortran compiler 🎉. The new Language Server will be able to understand all Fortran syntax, be faster, and give more accurate autocompletion, hover and diagnostic information. That means we plan on investing any future funding on creating our new language server and ultimately creating a better user experience for everyone.
fortls?Not to worry, fortls will continue to be here. We will keep fortls in active maintenance mode with bug fixes and new features from volunteer contributors, but otherwise we will be focusing our efforts into making the new language server using LFortran's parser a reality.
fortls vs fortran-language-serverThis project was originally based on fortran-language-server LSP implementation, but the two projects have since diverged.
fortls (this project) is now developed independently of the upstream hansec/fortran-language-server project and contains numerous new features and bug fixes
the original fortran-language-server does not.
For a complete and detailed list of the differences between the two Language Servers see the Documentation section: Unique fortls features (not in fortran-language-server)
The name of executable for this project has been chosen to remain fortls
to allow for integration with pre-existing plugins and workflows, but it could
change in the future.
This project would not have been possible without the original work of @hansec
in fortran-language-server
You can support Fortran-lang as a whole by donating at Fortran-lang - NumFOCUS.
When filing bugs please provide example code to reproduce the observed issue.
To report a security vulnerability please follow the instructions in our Security page.
This project is made available under the MIT License.
FAQs
fortls - Fortran Language Server
We found that fortls demonstrated a healthy version release cadence and project activity because the last version was released less than a year ago. It has 2 open source maintainers collaborating on the project.
Did you know?

Socket for GitHub automatically highlights issues in each pull request and monitors the health of all your open source dependencies. Discover the contents of your packages and block harmful activity before you install or update your dependencies.

Security News
Research
The Socket Research Team breaks down a malicious wrapper package that uses obfuscation to harvest credentials and exfiltrate sensitive data.

Research
Security News
Attackers used a malicious npm package typosquatting a popular ESLint plugin to steal sensitive data, execute commands, and exploit developer systems.

Security News
The Ultralytics' PyPI Package was compromised four times in one weekend through GitHub Actions cache poisoning and failure to rotate previously compromised API tokens.