
Security News
Research
Data Theft Repackaged: A Case Study in Malicious Wrapper Packages on npm
The Socket Research Team breaks down a malicious wrapper package that uses obfuscation to harvest credentials and exfiltrate sensitive data.
An ipywidget for vtkRenderWindow (formerly ipyvtk-simple)
This is an early prototype of creating a Jupyter interface to VTK. This toolkit
is a proof of concept and a more polished tool will be available as
ipyvtk in the future.
The code here was implemented from the work done by Andras Lasso under an MIT License (see the source).
The goal is to enable this widget to work with any server side
vtkRenderWindow
This render window could be from VTK Python,
ParaView, or PyVista.
Please note that vtk is not listed as a requirement for this package to
simplify its installation in virtual environments where VTK may be built from
source or bundled with ParaView and we do not want to install the wheels from
PyPI.
For use with PyVista, simply install with pip or conda:
pip install ipyvtklink
or
conda install -c conda-forge ipyvtklink
A Docker image is prebuilt and hosted in the ipyvtklink repository's packages.
To run in Docker:
docker pull ghcr.io/kitware/ipyvtklink:latest
docker run -p 8888:8888 ghcr.io/kitware/ipyvtklink:latest
and open the vtk.ipynb notebook.
Additionally, this can be used with ParaView. An example is given in
paraview.ipynb which can be run via:
docker pull ghcr.io/kitware/ipyvtklink-paraview:latest
docker run -p 8878:8878 ghcr.io/kitware/ipyvtklink-paraview:latest
You may have to build jupyter lab extensions for this to work in Lab. This is known to work well in Notebook.
PyVista has fully implemented downstream support for ipyvtklink. See PyVista's Documentation
See the pyvista.ipynb for an original proof of concept.
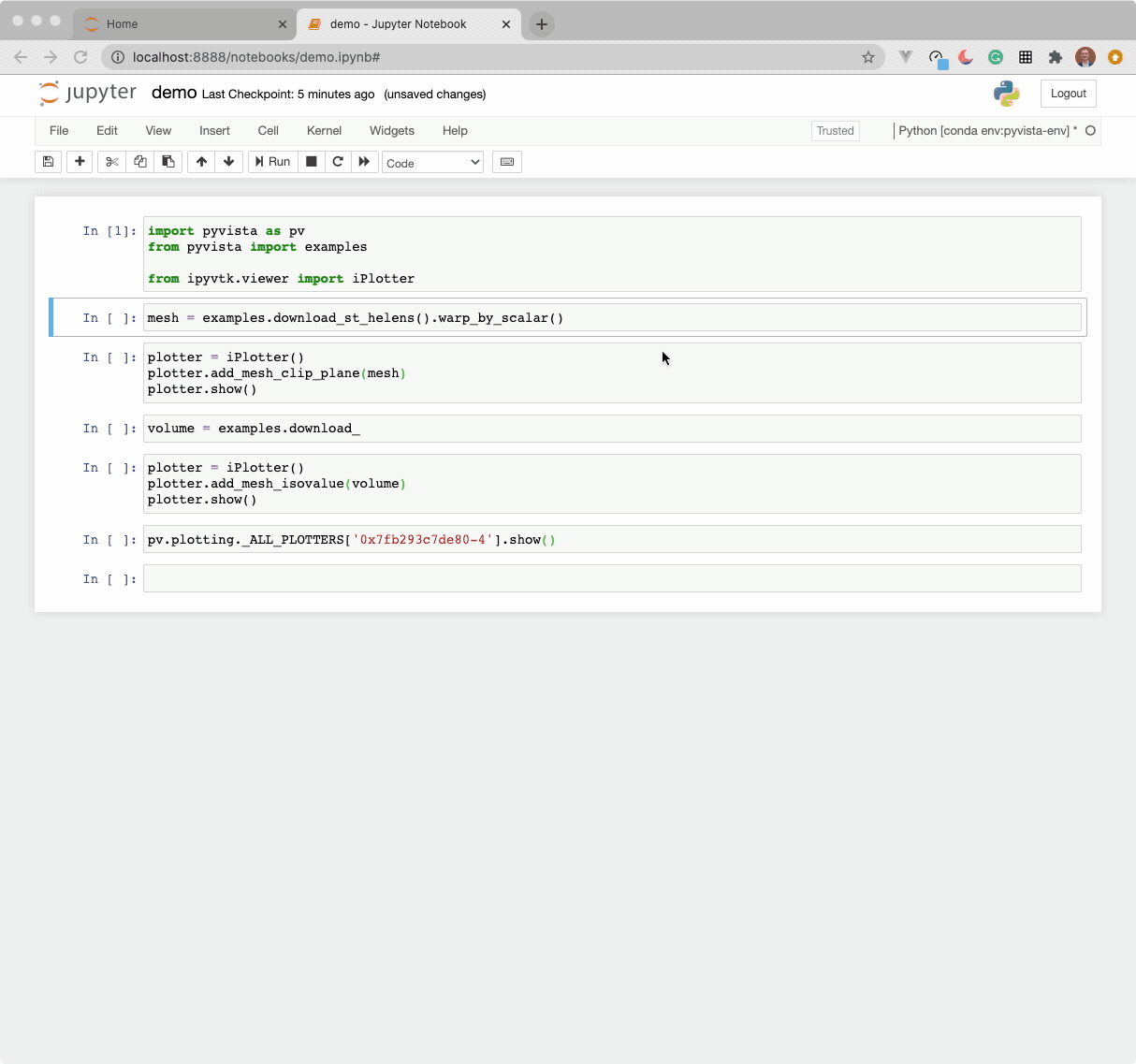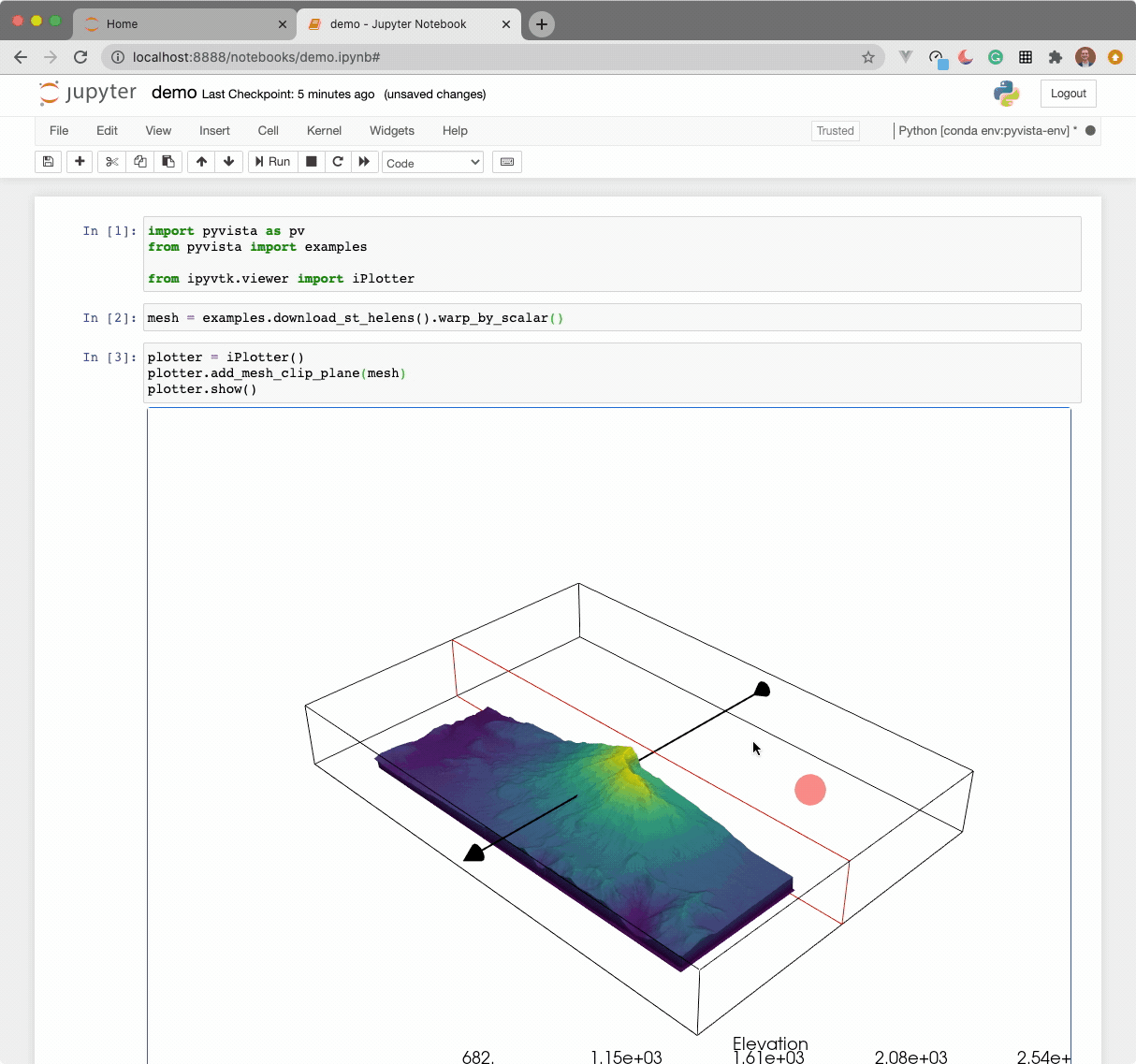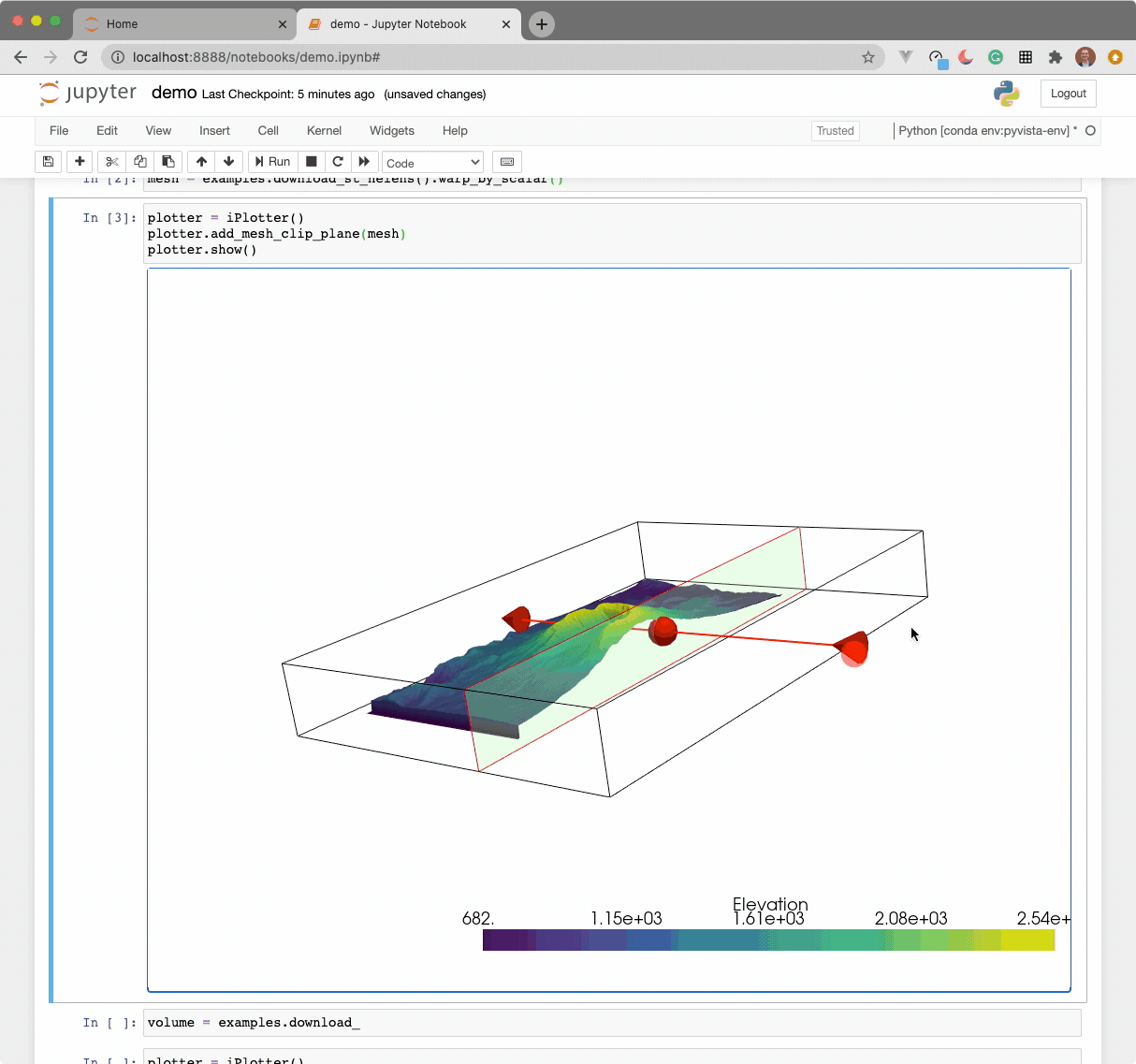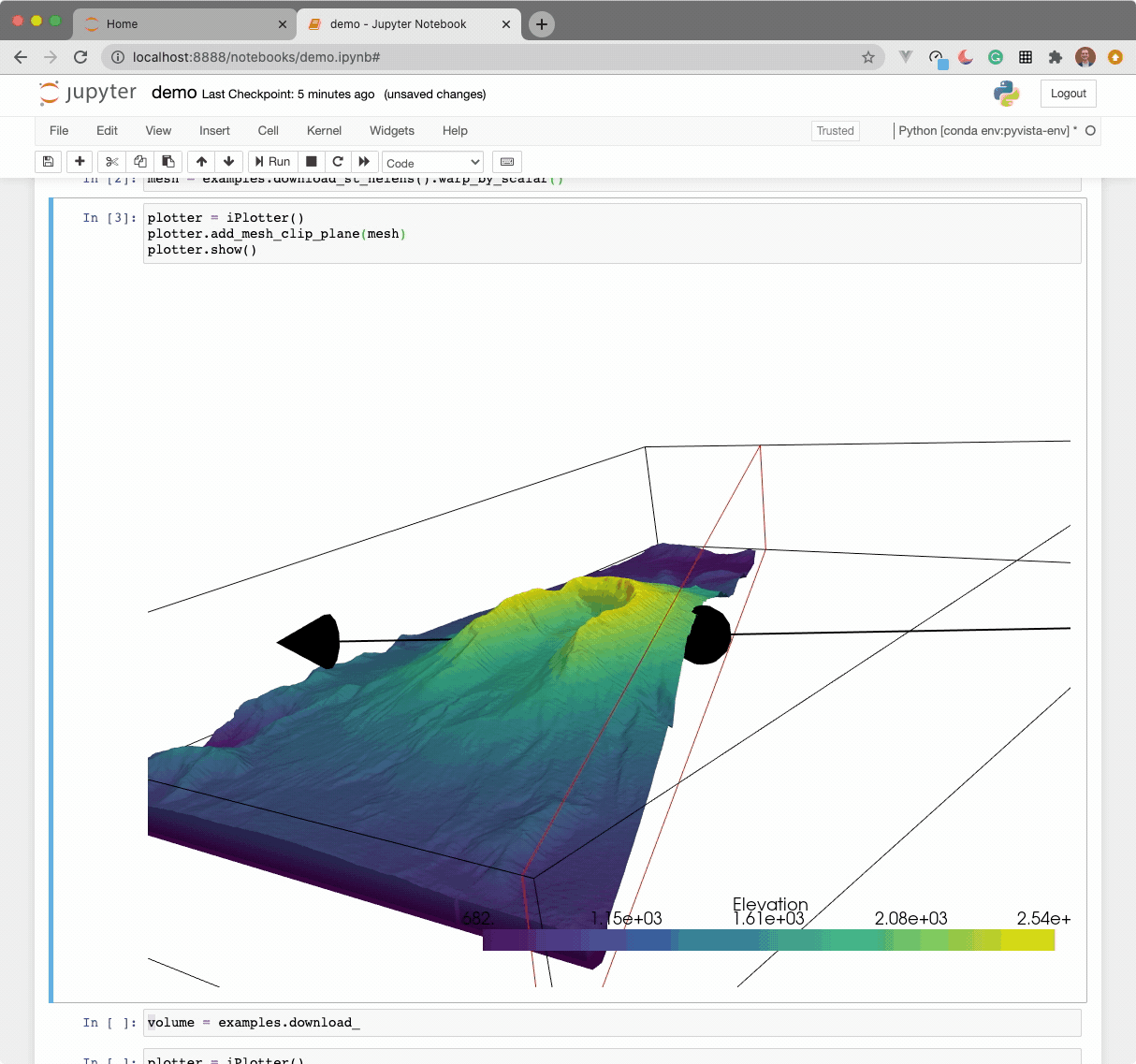
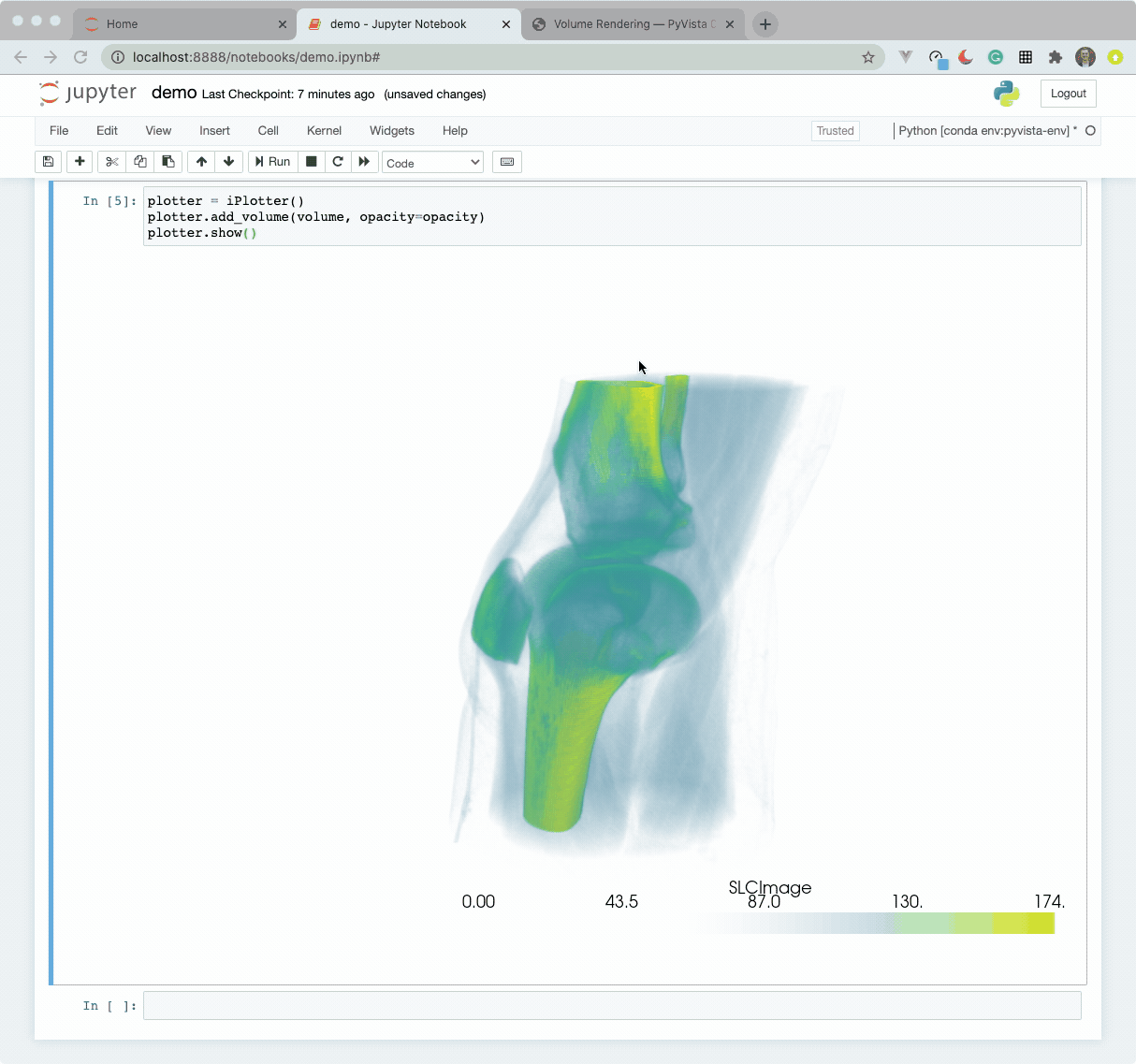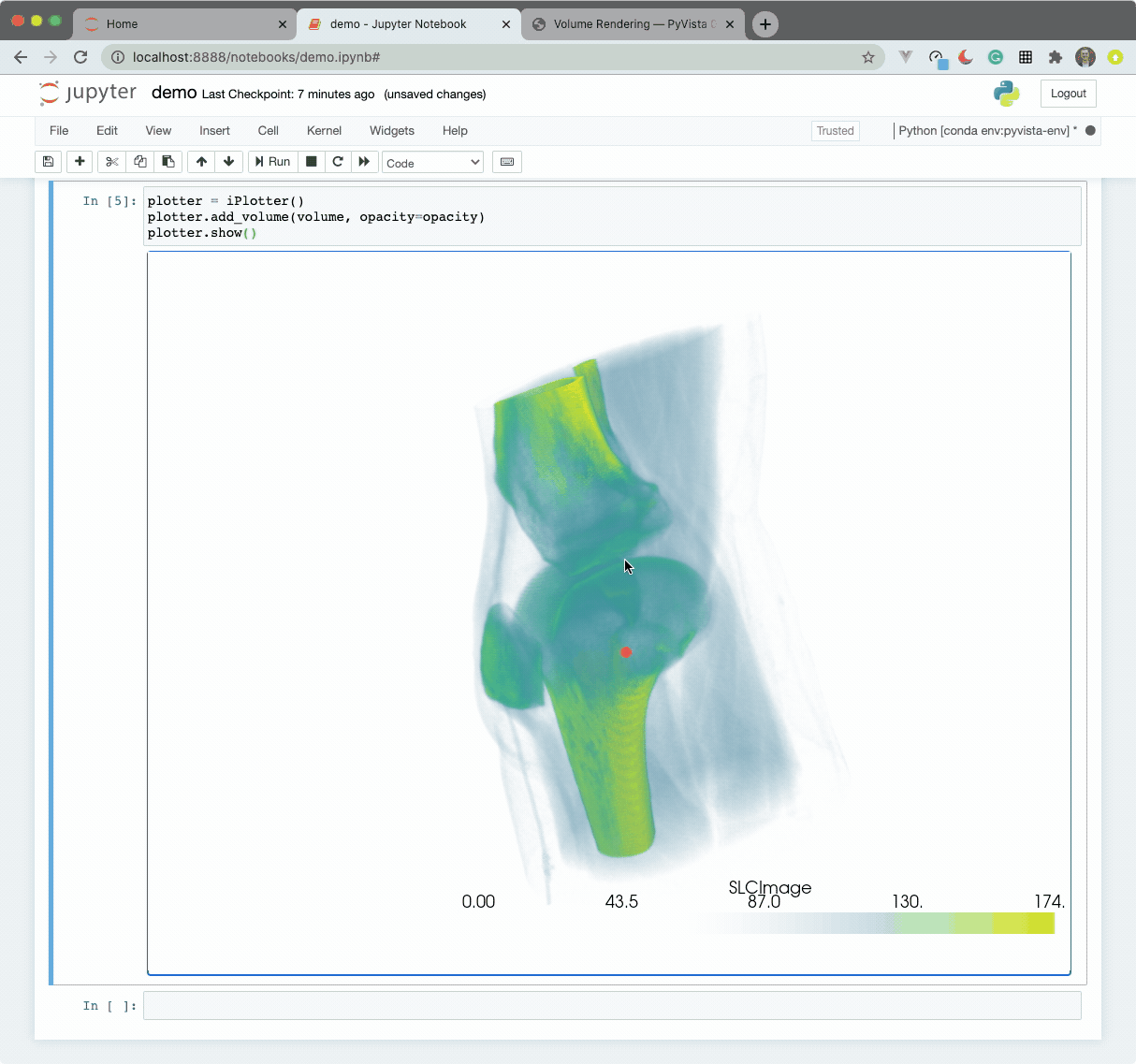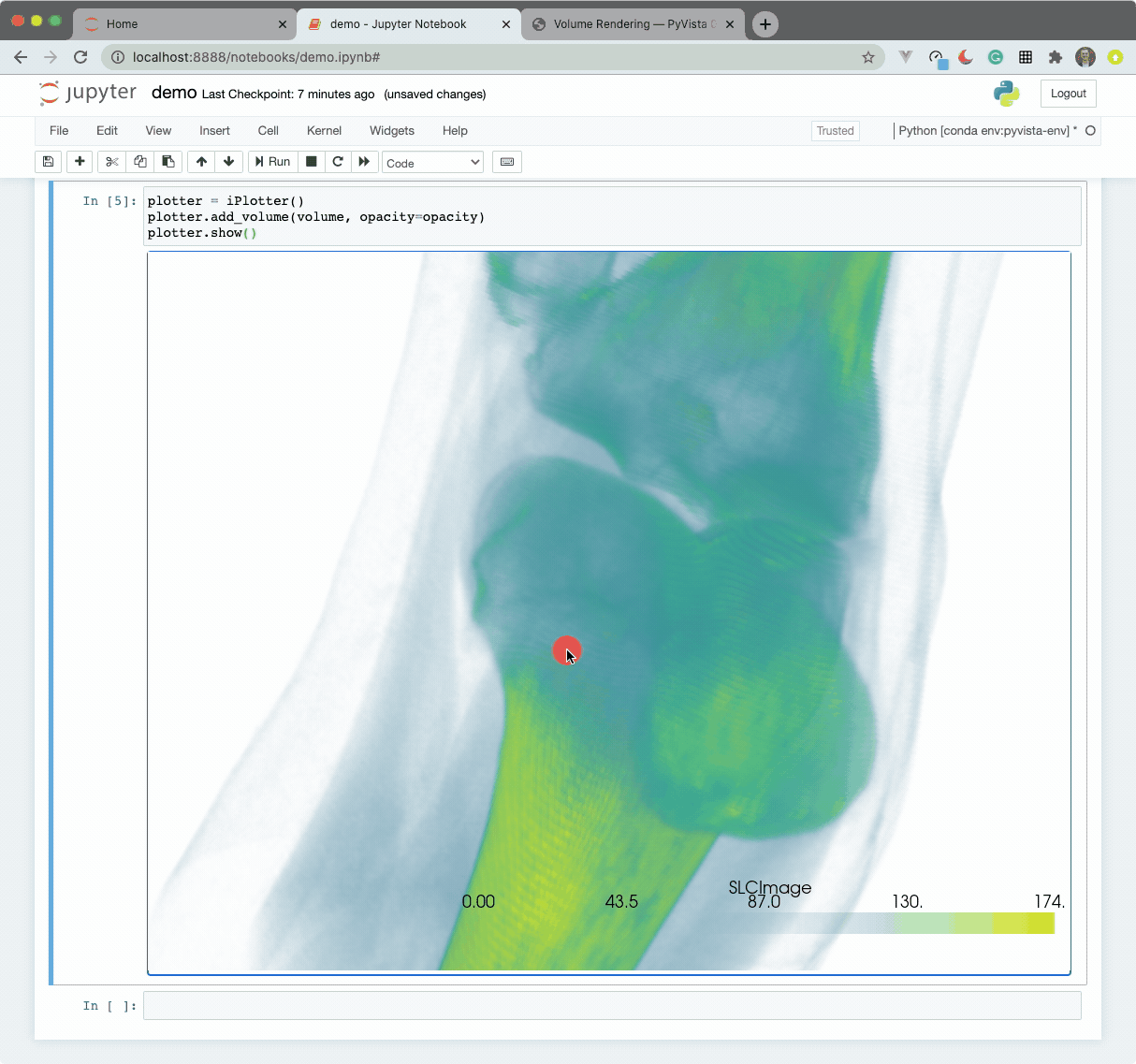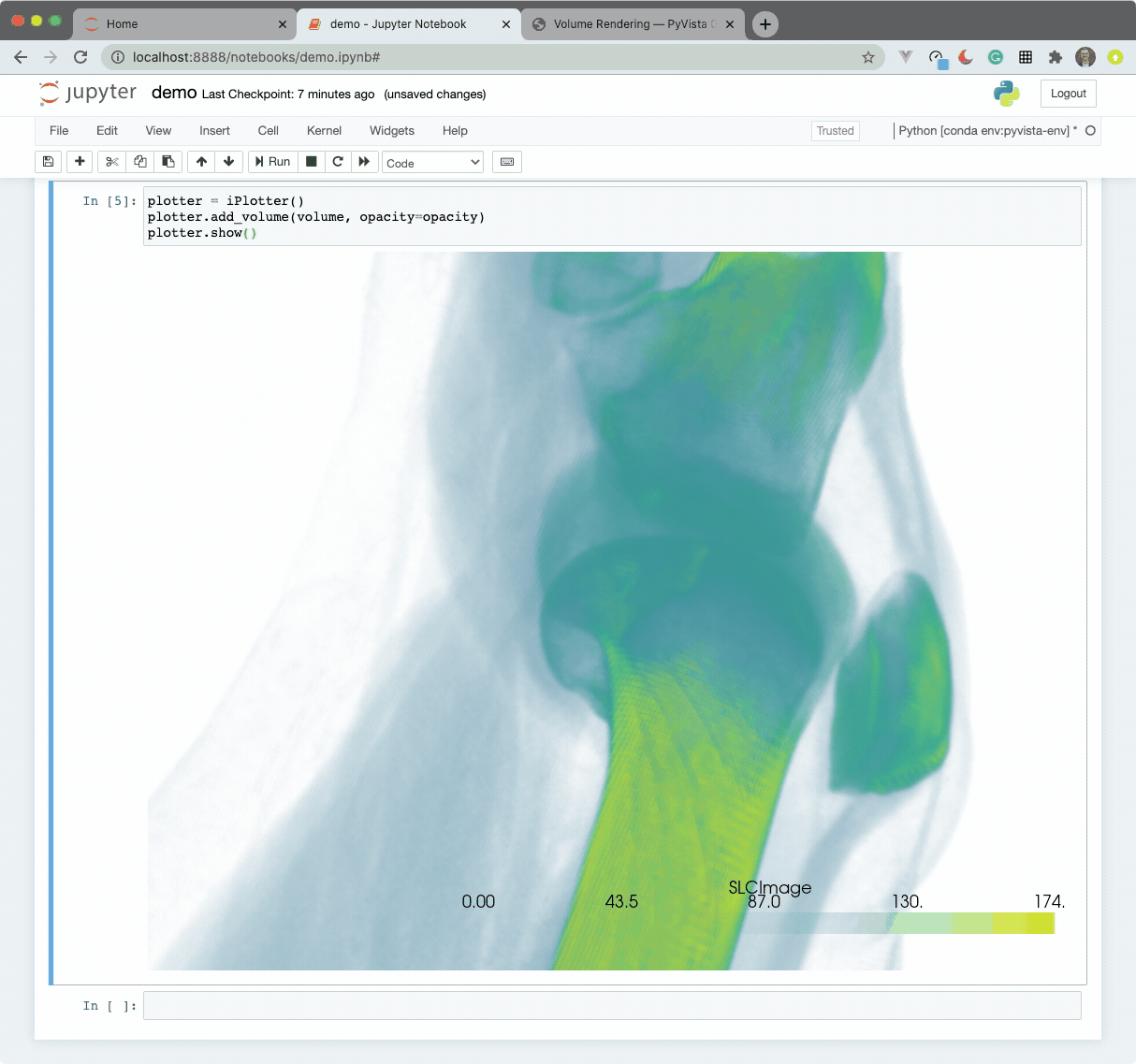
The widget here can be used with VTK. Here is a minimal example showing how
to pass any vtkRenderWindow to the ViewInteractiveWidget:
import vtk
from ipyvtklink.viewer import ViewInteractiveWidget
# Create some data
cylinder = vtk.vtkCylinderSource()
cylinder.SetResolution(8)
mapper = vtk.vtkPolyDataMapper()
mapper.SetInputConnection(cylinder.GetOutputPort())
actor = vtk.vtkActor()
actor.SetMapper(mapper)
# Set up render window
ren = vtk.vtkRenderer()
ren_win = vtk.vtkRenderWindow()
ren_win.SetOffScreenRendering(1)
ren_win.SetSize(600, 600)
ren_win.AddRenderer(ren)
iren = vtk.vtkRenderWindowInteractor()
iren.SetRenderWindow(ren_win)
style = vtk.vtkInteractorStyleTrackballCamera()
iren.SetInteractorStyle(style)
# Add actor to scene
ren.AddActor(actor)
ren.ResetCamera()
# Display
ViewInteractiveWidget(ren_win)
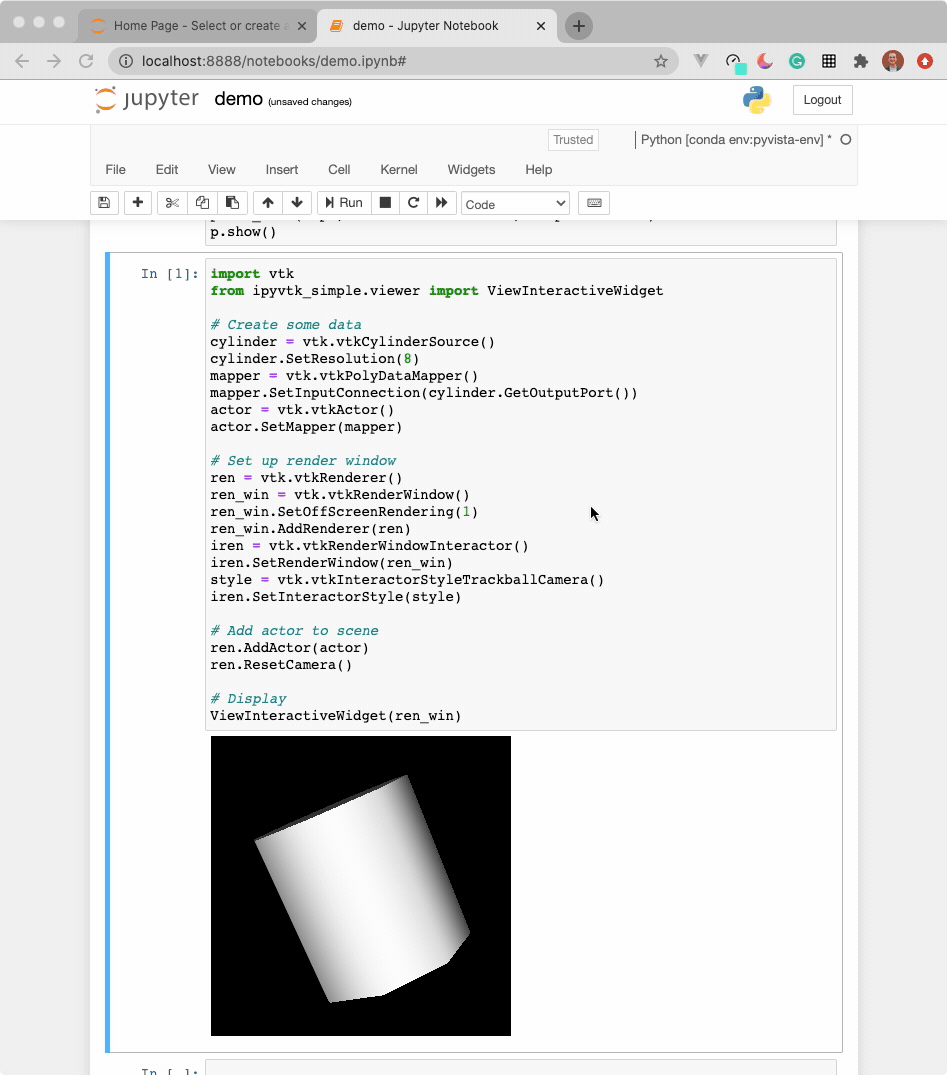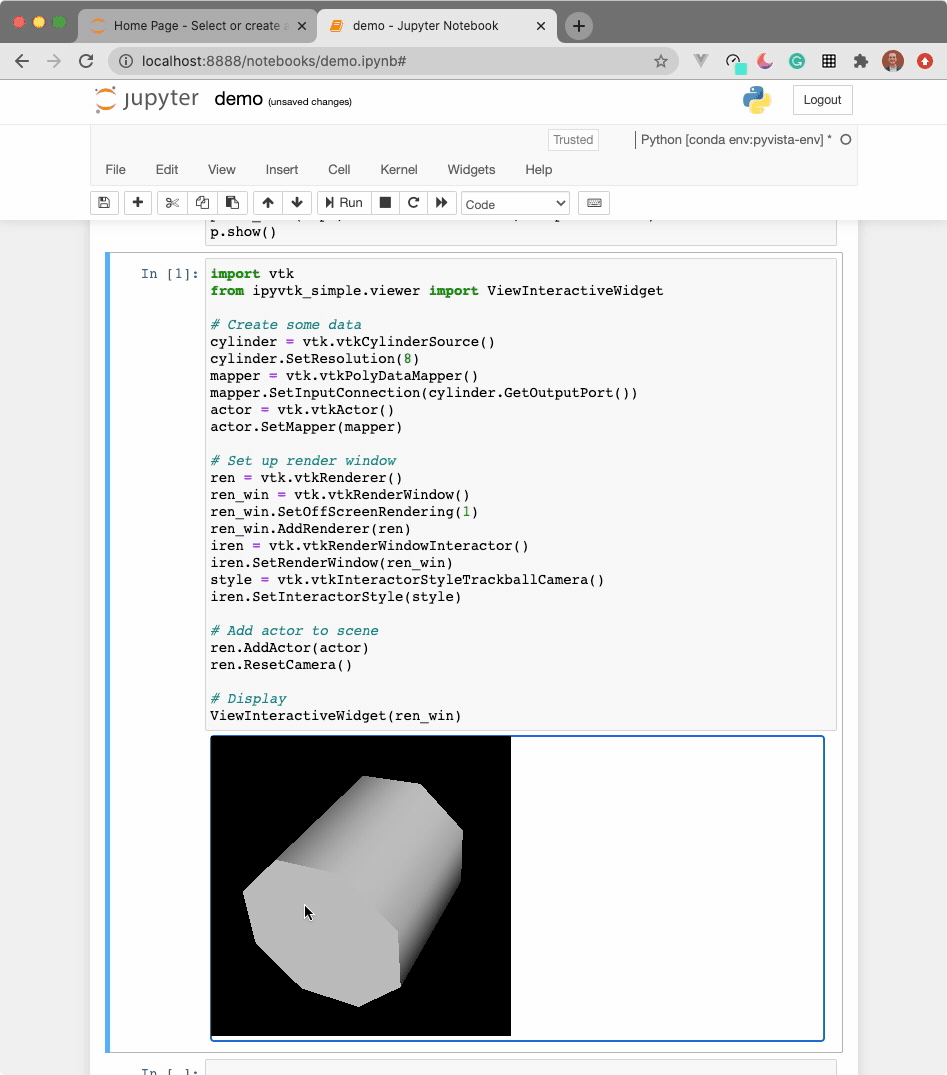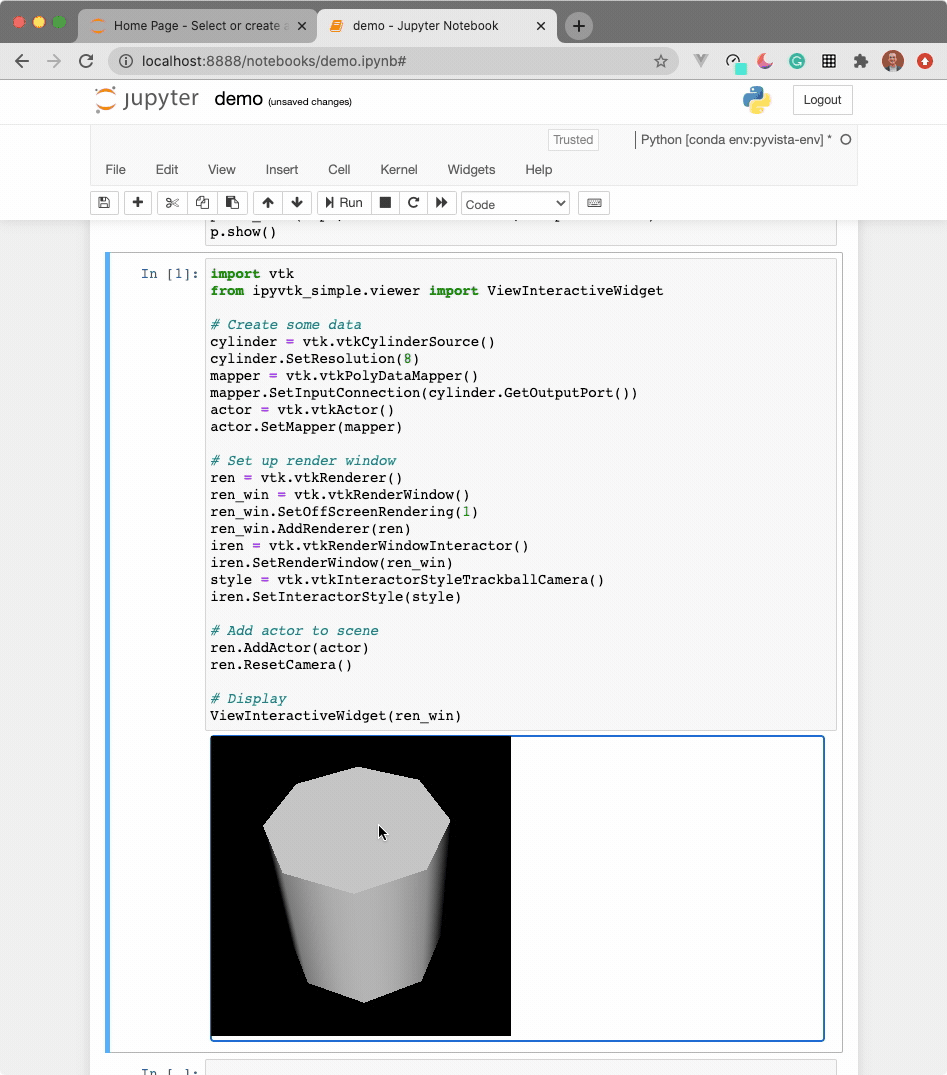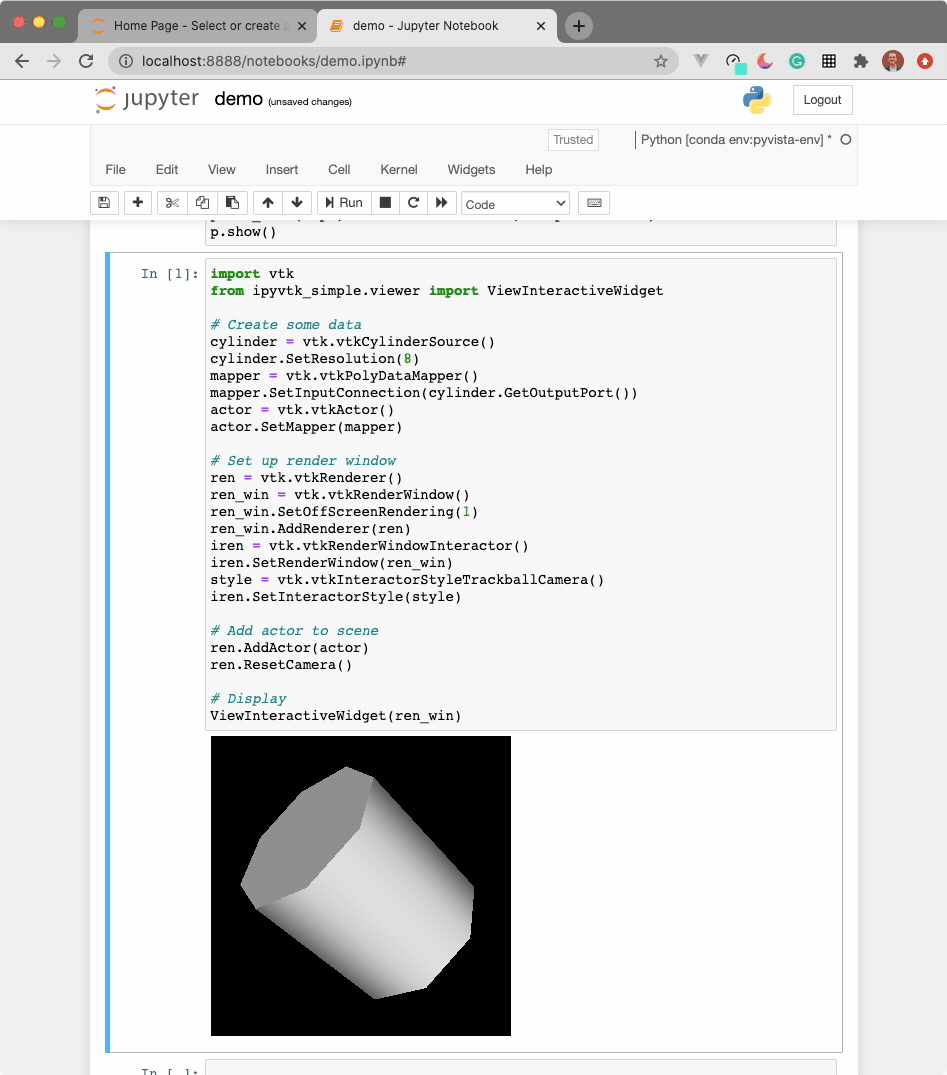
See instructions above for running ParaView in a Docker container.
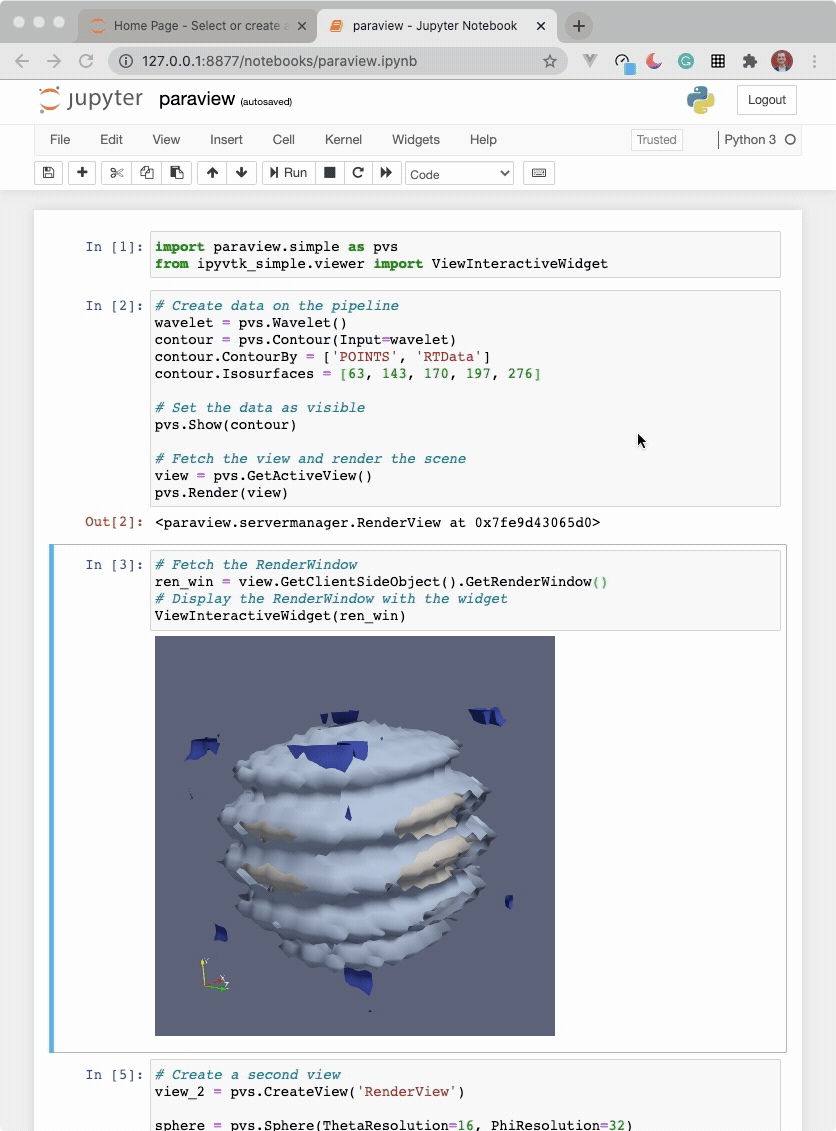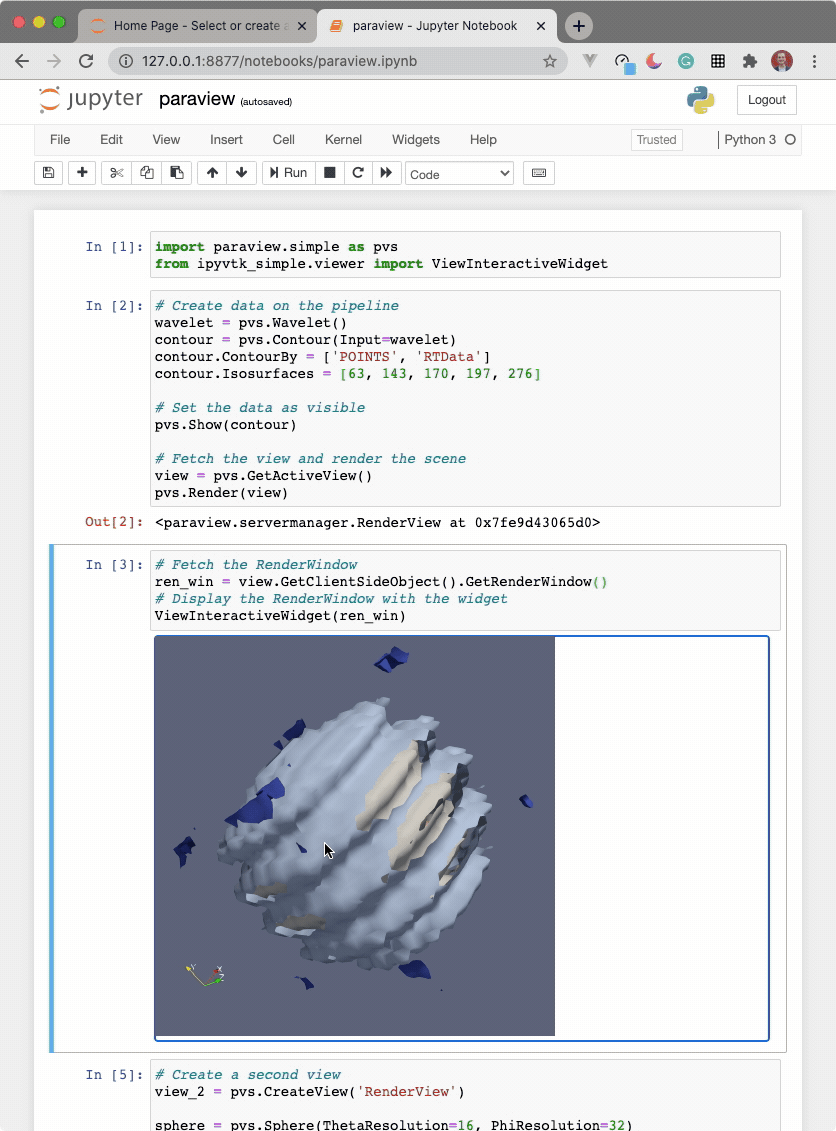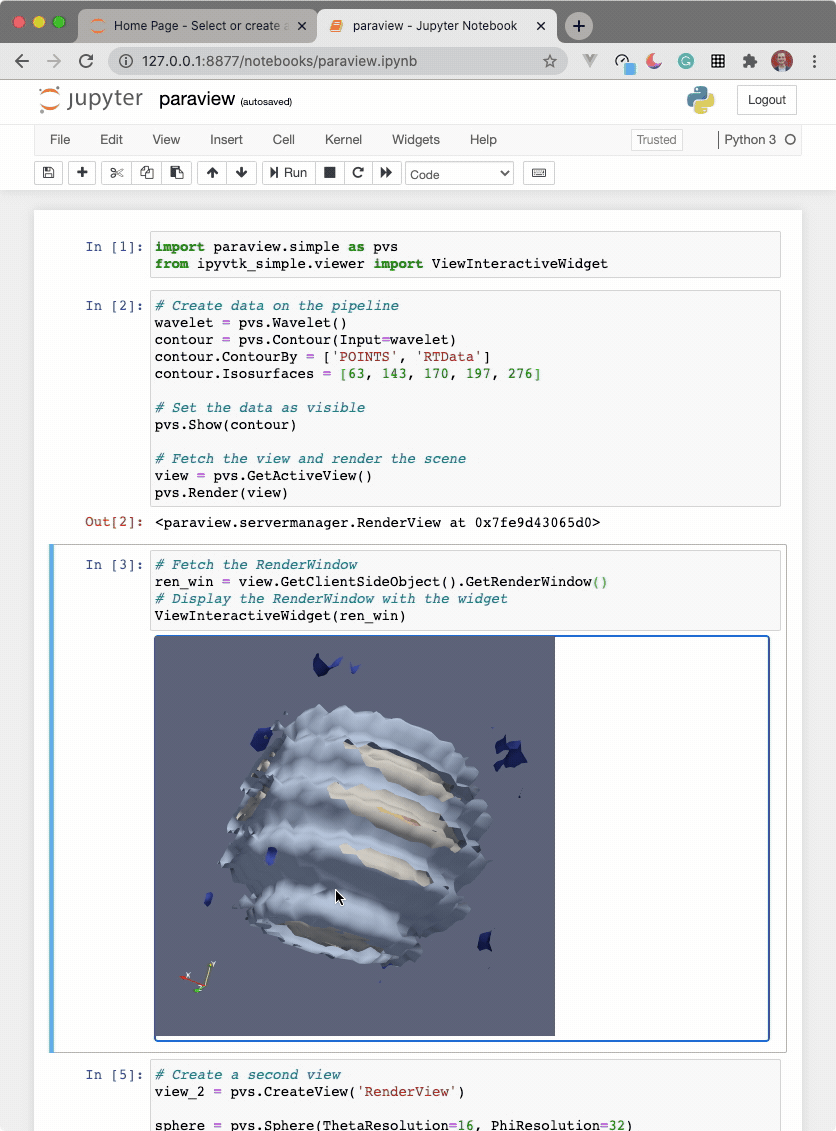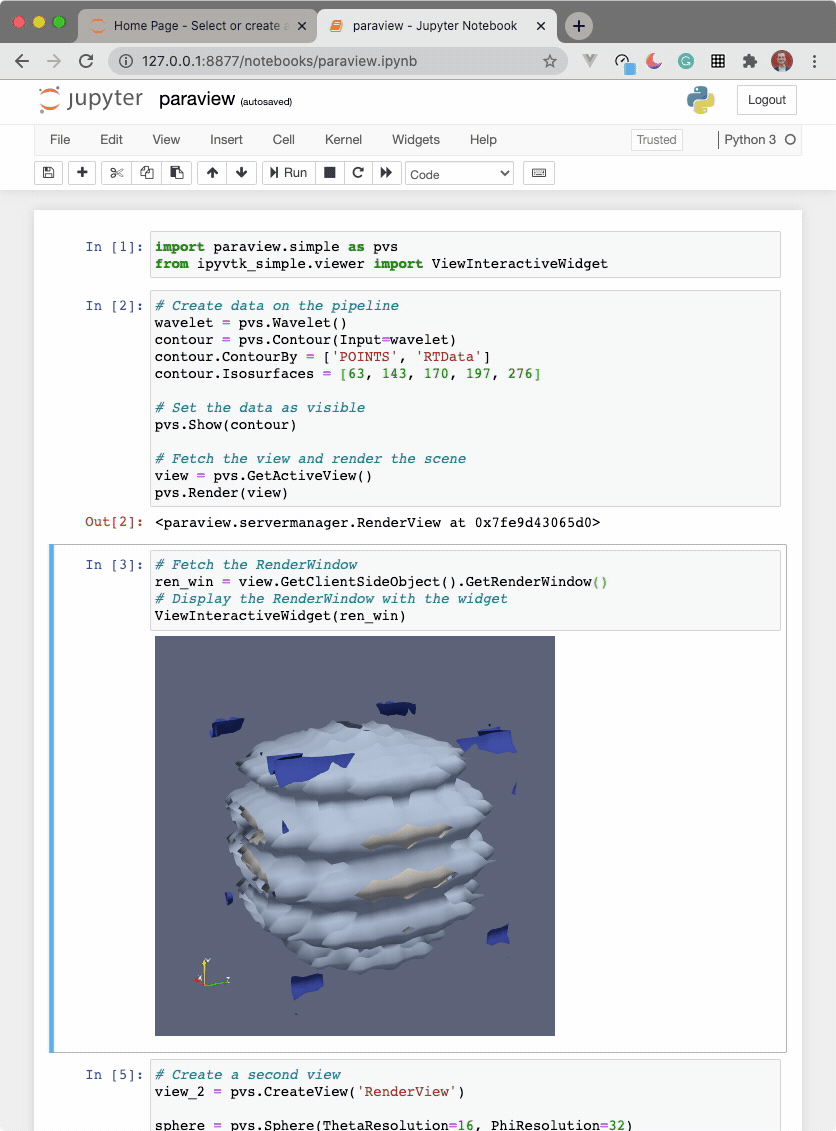
import paraview.simple as pvs
from ipyvtklink.viewer import ViewInteractiveWidget
# Create data on the pipeline
wavelet = pvs.Wavelet()
contour = pvs.Contour(Input=wavelet)
contour.ContourBy = ['POINTS', 'RTData']
contour.Isosurfaces = [63, 143, 170, 197, 276]
# Set the data as visible
pvs.Show(contour)
# Fetch the view and render the scene
view = pvs.GetActiveView()
pvs.Render(view)
# Fetch the RenderWindow
ren_win = view.GetClientSideObject().GetRenderWindow()
# Display the RenderWindow with the widget
ViewInteractiveWidget(ren_win)
FAQs
ipywidget for vtkRenderWindow
We found that ipyvtklink demonstrated a healthy version release cadence and project activity because the last version was released less than a year ago. It has 3 open source maintainers collaborating on the project.
Did you know?

Socket for GitHub automatically highlights issues in each pull request and monitors the health of all your open source dependencies. Discover the contents of your packages and block harmful activity before you install or update your dependencies.

Security News
Research
The Socket Research Team breaks down a malicious wrapper package that uses obfuscation to harvest credentials and exfiltrate sensitive data.

Research
Security News
Attackers used a malicious npm package typosquatting a popular ESLint plugin to steal sensitive data, execute commands, and exploit developer systems.

Security News
The Ultralytics' PyPI Package was compromised four times in one weekend through GitHub Actions cache poisoning and failure to rotate previously compromised API tokens.