Possible typosquat attack
Severity
Critical
Short Description
Package name is similar to other popular packages and may not be the package you want.
Suggestion
Use care when consuming similarly named packages and ensure that you did not intend to consume a different package. Malicious packages often publish using similar names as existing popular packages.
Information
Typosquatting is a malicious practice where attackers create packages with names that are intentionally similar to popular, legitimate packages. These packages often have slight variations in spelling, capitalization, or punctuation. The goal is to trick developers into accidentally installing the malicious package instead of the intended one, thereby compromising the security of their projects.
The concern with typosquats is that they can introduce significant security risks to your project. Once installed, a typosquatting package can execute malicious code, steal sensitive information, or create backdoors for future attacks. Because these packages are designed to closely resemble legitimate ones, they can easily go unnoticed, leading to potential widespread impact.
Recommended actions
Verify the Package Name:
- Double-check the spelling of the package name in your
package.jsonfile. Ensure that it matches the intended package exactly, including the correct case.
Confirm the Package Source:
- Visit the npm registry page of the suspected package to verify its legitimacy. Look for signs of trust, such as the number of downloads, reviews, and activity in the repository.
Compare with Known Packages:
- Compare the suspect package with the legitimate package you intended to use. Pay attention to details like the maintainer, version history, and repository links.
Check for Similar Names:
- Investigate if there are other packages with similar names. Typosquatting often involves creating packages with names that are very similar to popular packages.
Remove Malicious Packages:
- If you find that a malicious package was included in your code base, remove it immediately.
Replace with the Correct Package:
- If you identify that the package is indeed a typo, replace it with the correct package name in your
package.jsonfile.
Examples
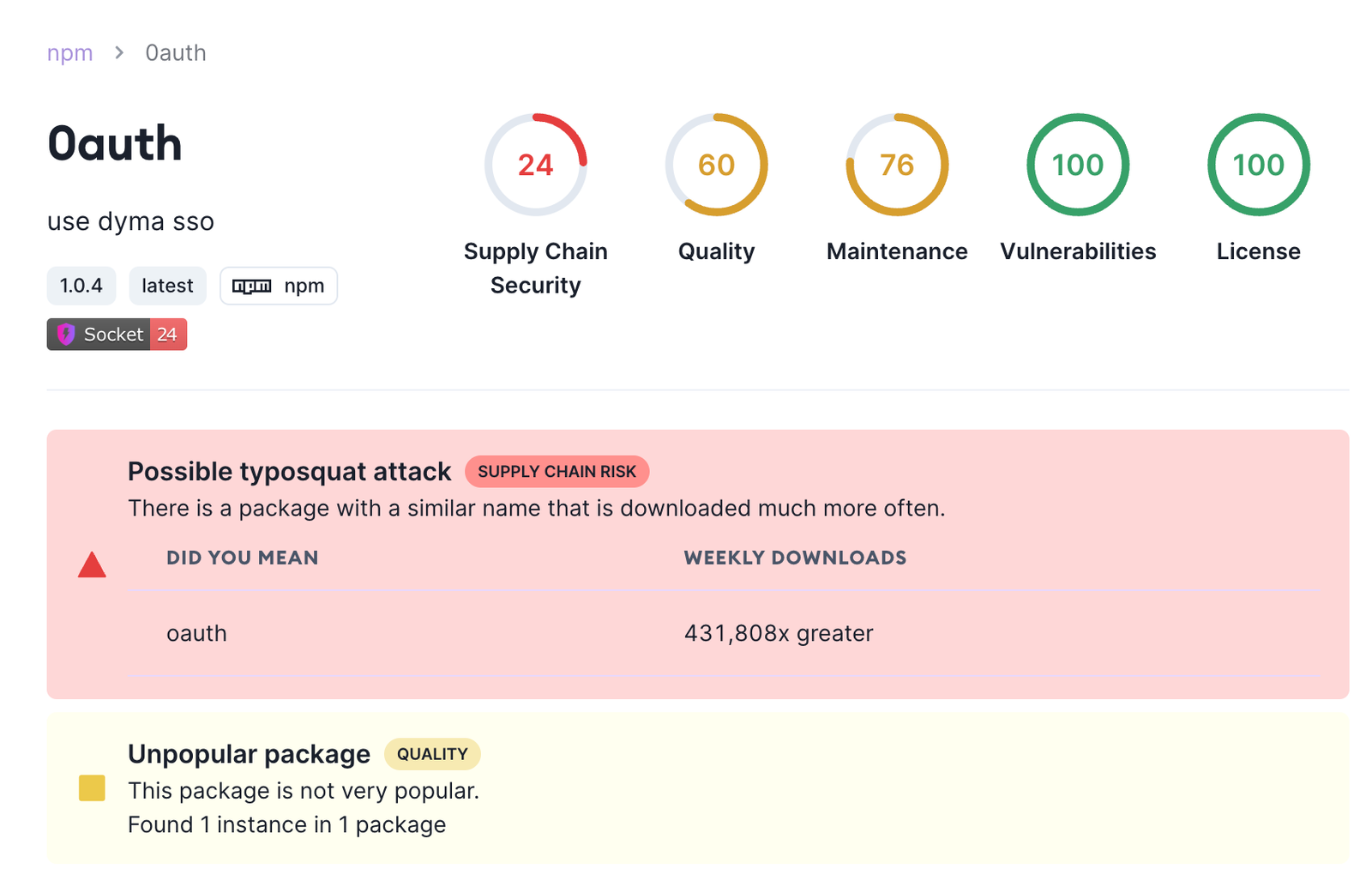
When Socket detects a Typosquatting package, the alert also asks, "Did you mean [legitimate package name]?" In this example, the legitimate package is OAuth, which is downloaded 1.4 million times per week.
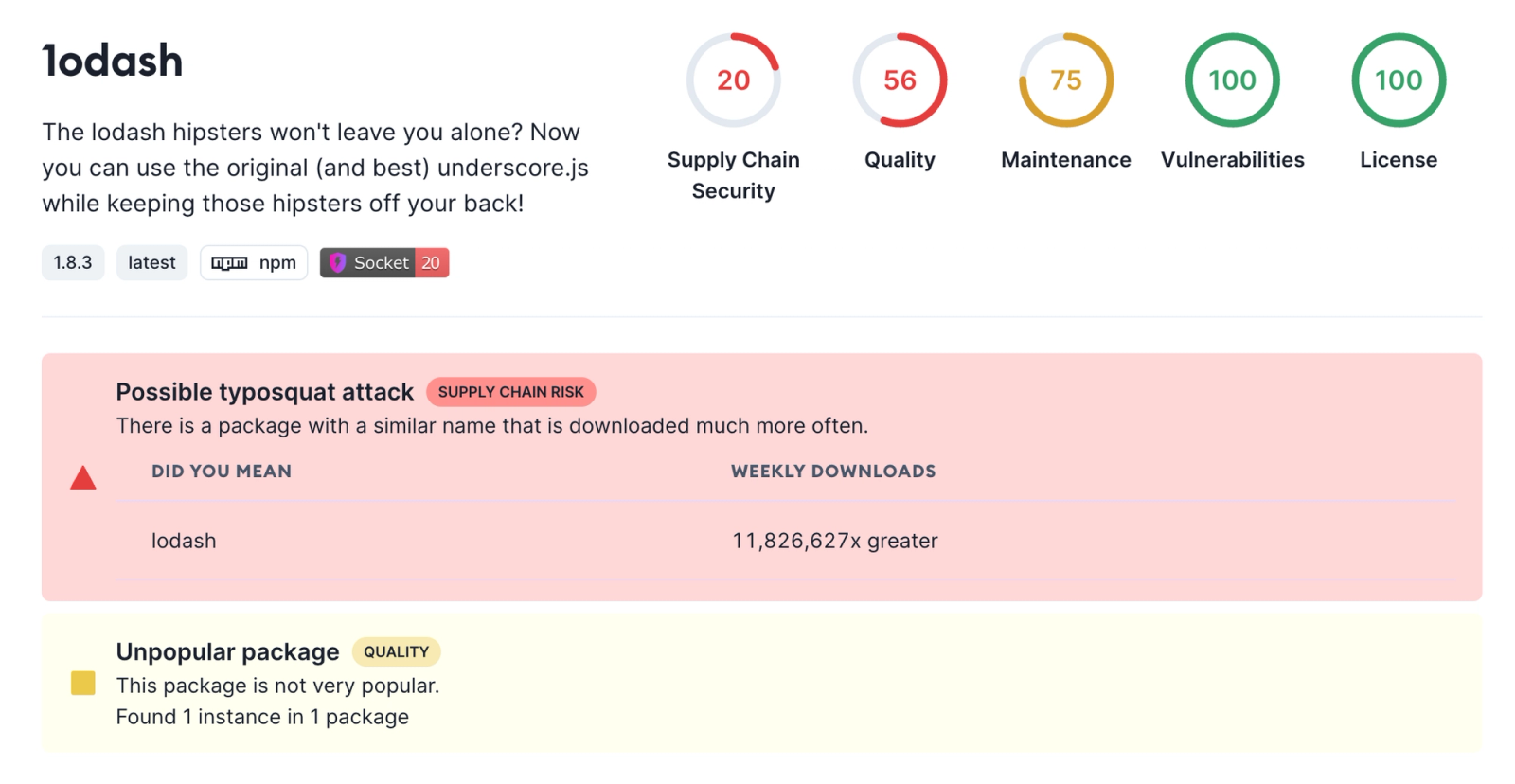
In another example, a package is typosquatting the Lodash utility library. The legitimate package is linked and it also displays a comparison of weekly downloads.
One of the most notorious package typosquatting incidents took place in 2019 when the Python security team had to take action against two malicious Python libraries found on PyPI. These libraries were designed to steal SSH and GPG keys from the developers' projects. The compromised packages were “python3-dateutil,” mimicking the widely-used “dateutil” library, and “jeIlyfish” (with the first 'L' replaced by an 'I'), which closely resembled the “jellyfish” library.
Detection Method
Socket fetches package with names similar to the target package, focusing on those with significantly higher download counts. It sorts these packages to prioritize the most likely typosquats, calculates the probability of each package being a typosquat, and flags packages if their probability exceeds a certain threshold.