October 18
Improved Organization of Ecosystem-Specific Alerts

The Alerts page now groups ecosystem-specific alerts (npm, Chrome extensions, and VS Code extensions) into a dedicated section, with clear prefixes to make them easier to identify. For example, Chrome extension alerts now appear as “Chrome: [Alert Name]” and VS Code alerts as “VS Code: [Alert Name]”. This is a UI-only change. Alert identifiers in API responses remain unchanged.
October 18
Socket Firewall v0.14.0
Socket Firewall version 0.14.0 adds new configuration options and improves reliability when connecting to the API.
New features
- Added graceful retry handling when API calls fail or return non-2xx responses.
- Made the action for unrecognized hostnames configurable, giving users more control over default network behavior.
Bug fixes and improvements
- Fixed linting issues.
- Updated documentation and internal tests.
- Refactored code for improved maintainability.
October 17
Python SDK: Improved File Upload Path Normalization
Fixed issues with file uploads that caused dotfiles (such as .socket.facts.json) to lose their leading dots and paths without directories to fail. The SDK now correctly preserves dotfile names and normalizes file paths consistently across operating systems, including Windows.
October 15
Python SDK: Fixed Deduplication for Compact API Responses
Resolved an issue in the Python SDK where the deduplication logic failed when processing compact API responses that omit optional fields. The updated logic now safely handles missing fields and avoids adding unnecessary null values to the output.
October 8
New: Support for Python Vulnerability Fixes in socket fix
The socket fix command now supports automatically fixing vulnerabilities in Python (PyPI) projects by upgrading affected dependencies in requirements.txt and uv.lock files. This allows you to apply suggested CVE fixes for Python dependencies just as easily as you can for npm or other ecosystems.
October 4
Fix: Unpublished npm Packages
Fixed unpublished npm packages with missing tarballs to ensure they can now be resolved via the /v0/purl batch endpoint and will properly return with unpublished alerts.
October 3
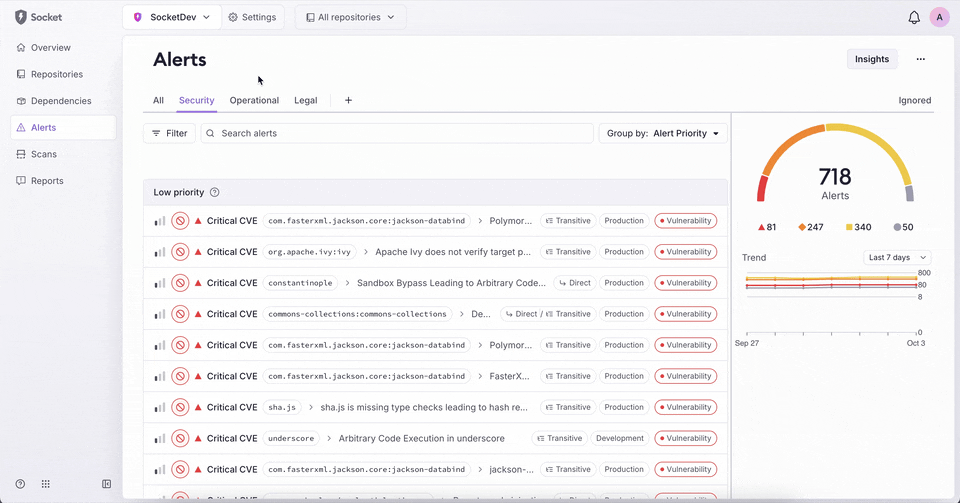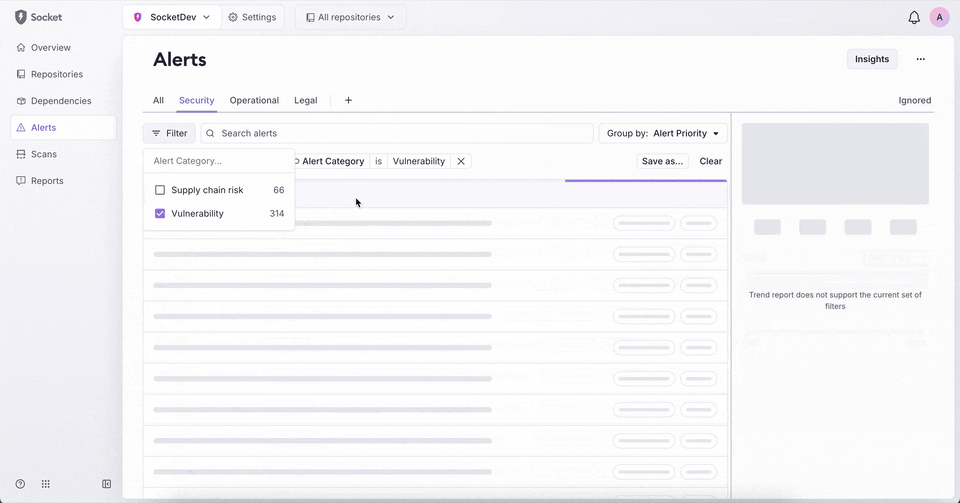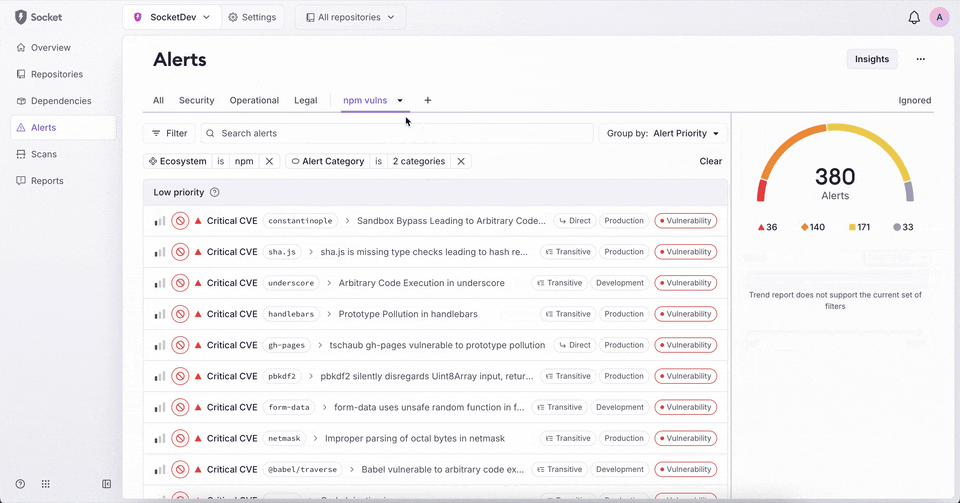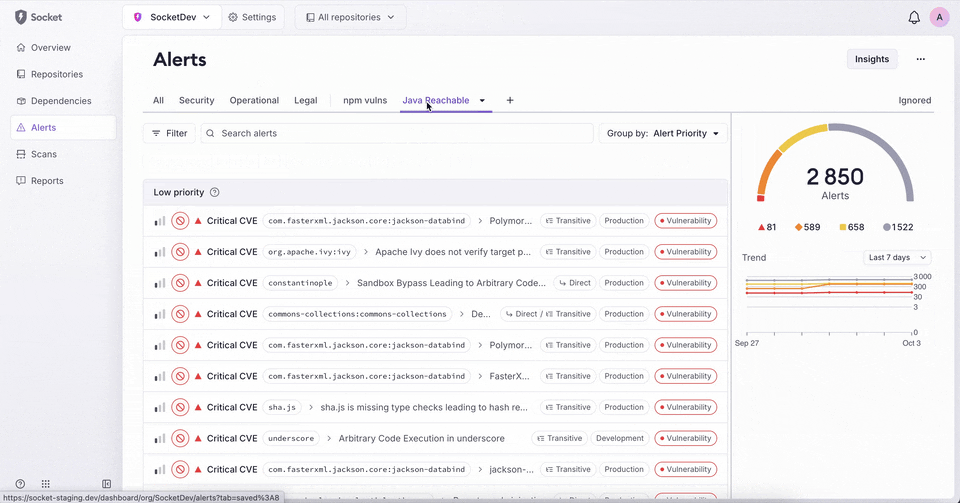
New: Custom Tabs in Org Alerts

You can now create and save custom tabs on the org alerts page. This lets you preserve a set of filters with a name, making it easy to return to and share across your organization.
- Add, rename, duplicate, or delete custom tabs.
- Save changes directly from the filter UI or dropdown.
- Tabs persist across sessions and are visible to all org members.
- Visual indicators show when filters differ from the saved state.
This feature is available today on the org alerts page for business and enterprise plans.
September 30
Fix: Scoped vs. Unscoped Package Search
Fixed organization dependency search API to correctly distinguish between scoped and unscoped npm packages. Searching for pkg:npm/package-name now returns only the unscoped package and will not incorrectly include scoped variants like pkg:npm/@types/package-name.
September 25
Filter by Repository Labels in RepoSwitcher
The RepoSwitcher at the top of the dashboard now supports repository label selection, letting you scope content across pages by label.
- Choose a label from the RepoSwitcher dropdown to filter repositories throughout the dashboard
- Internal links automatically preserve your selected label as you navigate
- Search results in the RepoSwitcher now highlight the matched text for easier scanning
September 23
New: Bulk Label Assignment for Repositories
You can now organize repositories more efficiently by assigning labels to multiple repositories at once.
- Select multiple repositories using checkboxes in the repository table
- Apply a common label to all selected repositories in one step
- Confirmation dialog appears if some repositories already have a label
- Improved DataTable behavior: row clicks open details, checkboxes handle selection
