
Product
Introducing Socket Firewall: Free, Proactive Protection for Your Software Supply Chain
Socket Firewall is a free tool that blocks malicious packages at install time, giving developers proactive protection against rising supply chain attacks.


Mix Irving

Alexandros Kapravelos

Eli Insua
July 30, 2025
Browser extensions are now an integral part of how we use the web, but they come with a supply chain challenge that’s difficult to solve at scale. Threat actors continuously develop new tactics to bypass defenses, from purchasing popular extensions to introducing malicious code through updates. With minimal friction to publish and install extensions, the ecosystem remains wide open to abuse, allowing legitimate tools to be turned into malware overnight.
Today, we’re announcing a major milestone for Socket:
We’re expanding beyond open source package registries to begin protecting browser extensions in a new product line, designed to bring visibility and security to the browser extension ecosystem. We’re starting with Chrome in an experimental release, with plans to expand support to other extension platforms.
Recent incidents have shown how quickly a trusted extension can become a threat. The RedDirection campaign, revealed earlier this month, compromised 18 Chrome and Edge extensions, including some with the Google "verified" badge, infecting 2.3 million users. These extensions started out as benign, useful tools (e.g., color pickers and volume boosters) but silently became malicious after updates, hijacking browsers, tracking every website visited, and redirecting users to phishing pages.
If you think a high-install extension with thousands of reviews is safe, you would be mistaken in this instance.
Because of how Google and Microsoft handle extension updates, malicious versions were silently pushed to over 2.3 million users with no clicks, no phishing, and no social engineering required to deliver the malicious update. A simple version bump turned legitimate productivity tools into surveillance malware. The update systems of both companies are optimized for scale, which can leave significant gaps in extension security.
Our own threat research has uncovered many more examples of the growing risk of malicious browser extensions across other ecosystems. We documented Firefox extensions hijacking sessions, manipulating content, and even being sold on the dark web for $100,000 with advanced malware capabilities. Our follow-up investigation revealed extensions impersonating popular games, hijacking shopping sessions, and stealing OAuth tokens, proving just how creative attackers have become in exploiting browser permissions.
Our new product provides:
In short, we bring the same rigorous, proactive security analysis we pioneered for open source to the browser extension supply chain.
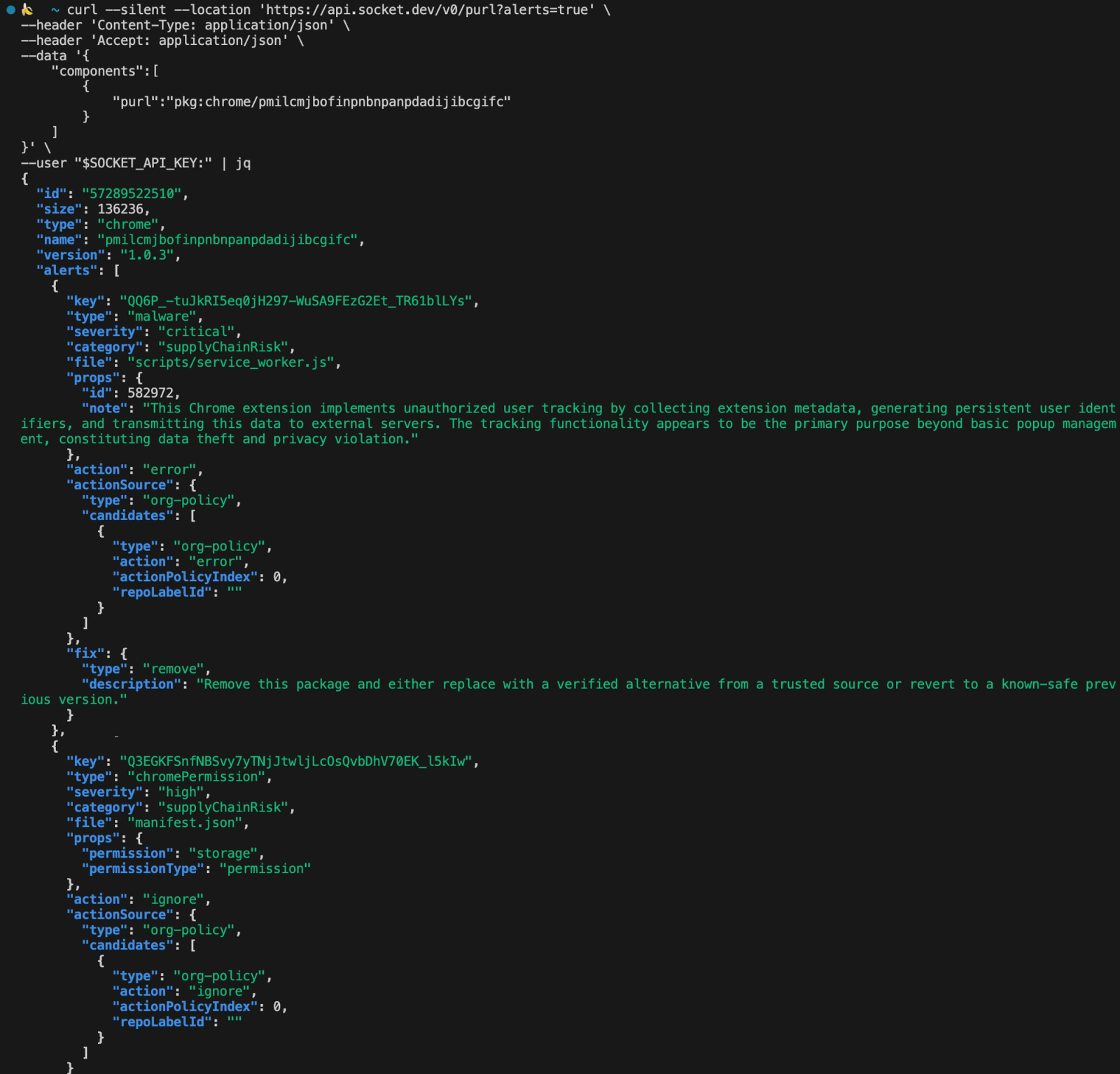
Here’s what happens behind the scenes when Socket scans a browser extension. When you query our API with an extension ID or package URL, we analyze the extension’s code, metadata, and permissions to detect malicious behavior, privacy violations, or risky patterns.
In the screenshot below, Socket flagged a Chrome extension as critical malware for implementing unauthorized user tracking by collecting extension metadata, generating persistent user identifiers, and transmitting this data to external servers.
The scan identifies key risks (e.g., data exfiltration) and highlights exactly which permissions and files are involved (e.g., manifest.json, service_worker.js).
Chrome is just the start. We’re actively working on support for VS Code, Open VSX, and Firefox extensions. These ecosystems share the same risks, including silent updates, high privileges, and lack of scrutiny, and they are ripe for exploitation.
We’re currently in experimental mode and looking for pilot partners. If you’re interested in securing your organization’s browser extensions, contact us to get early access.
Subscribe to our newsletter
Get notified when we publish new security blog posts!
Try it now

Product
Socket Firewall is a free tool that blocks malicious packages at install time, giving developers proactive protection against rising supply chain attacks.

Product
Socket now lets you customize pull request alert headers, helping security teams share clear guidance right in PRs to speed reviews and reduce back-and-forth.

Product
Socket's Rust support is moving to Beta: all users can scan Cargo projects and generate SBOMs, including Cargo.toml-only crates, with Rust-aware supply chain checks.