
Product
Introducing Socket Fix for Safe, Automated Dependency Upgrades
Automatically fix and test dependency updates with socket fix—a new CLI tool that turns CVE alerts into safe, automated upgrades.
Quickly evaluate the security and health of any open source package.
jessa-vue-components
9.17.1563
Removed from npm
Blocked by Socket
The script is designed to exfiltrate sensitive system information to an external server via DNS queries. The use of obfuscation and the method of data transmission indicate malicious intent.
Live on npm for 39 minutes before removal. Socket users were protected even while the package was live.
@azure-tests/perf-storage-file-share-track-1
0.0.1-security.14
by npm
Live on npm
Blocked by Socket
Malicious code in @azure-tests/perf-storage-file-share-track-1 (npm) Source: ghsa-malware (a77a70aec760d01762f6eea825194c2d558174a44b966b59043ce3f9424626f0) Any computer that has this package installed or running should be considered fully compromised. All secrets and keys stored on that computer should be rotated immediately from a different computer. The package should be removed, but as full control of the computer may have been given to an outside entity, there is no guarantee that removing the package will remove all malicious software resulting from installing it.
bitpay-cordova-sdk
0.0.1-security
by npm
Removed from npm
Blocked by Socket
Malicious code in bitpay-cordova-sdk (npm) Source: ghsa-malware (c65a1f5a2711ae665b870cf63ffa85839dffa1c1acff19b1dad0fc07233dd05b) Any computer that has this package installed or running should be considered fully compromised. All secrets and keys stored on that computer should be rotated immediately from a different computer. The package should be removed, but as full control of the computer may have been given to an outside entity, there is no guarantee that removing the package will remove all malicious software resulting from installing it.
Live on npm for 4 hours and 32 minutes before removal. Socket users were protected even while the package was live.
trello-enterprises
19.1000.1
by trello-x
Live on npm
Blocked by Socket
The script collects information like current working directory, hostname, username, and home directory and sends it to a remote server.
airbnb-jitney-schemas
99.9.9
by celesian
Removed from npm
Blocked by Socket
This script is highly suspicious and potentially malicious. It is attempting to exfiltrate system information and send it to a Telegram bot. This poses a significant security risk.
azure-graphrbac
5.6.1
by npm
Removed from npm
Blocked by Socket
Malicious code in azure-graphrbac (npm) Source: ghsa-malware (8753478507375846584df851f88ad72637d64beb4e8e6a5ffdaa19b39440e7fe) Any computer that has this package installed or running should be considered fully compromised. All secrets and keys stored on that computer should be rotated immediately from a different computer. The package should be removed, but as full control of the computer may have been given to an outside entity, there is no guarantee that removing the package will remove all malicious software resulting from installing it.
Live on npm for 11 hours and 34 minutes before removal. Socket users were protected even while the package was live.
coinmarketcap.com
1.0.9
by pooluniswap
Removed from npm
Blocked by Socket
Malicious code in coinmarketcap.com (npm) Source: ghsa-malware (cb95c3bffb062ee135c99ebd88cf1ed249f2d70dfb23f5b24477d3cc4fa471ea) Any computer that has this package installed or running should be considered fully compromised. All secrets and keys stored on that computer should be rotated immediately from a different computer. The package should be removed, but as full control of the computer may have been given to an outside entity, there is no guarantee that removing the package will remove all malicious software resulting from installing it.
Live on npm for 10 hours and 14 minutes before removal. Socket users were protected even while the package was live.
twitter-downloader
1.1.7
by tobyg74
Live on npm
Blocked by Socket
The code fetches and potentially exposes sensitive authorization information in an insecure manner from Pastebin, which is a red flag for data security and integrity.
typeahead-client-logger
7.537.1
by hexp-ahed
Removed from npm
Blocked by Socket
Malicious code in typeahead-client-logger (npm) Source: ghsa-malware (9121846b93247c8f8db2f98b553de9231e63282325f9bbaff65e8b6916d2a6cf) Any computer that has this package installed or running should be considered fully compromised. All secrets and keys stored on that computer should be rotated immediately from a different computer. The package should be removed, but as full control of the computer may have been given to an outside entity, there is no guarantee that removing the package will remove all malicious software resulting from installing it.
Live on npm for 4 hours and 54 minutes before removal. Socket users were protected even while the package was live.
azure-graphrbac
3.3.1000
by npm
Removed from npm
Blocked by Socket
Malicious code in azure-graphrbac (npm) Source: ghsa-malware (8753478507375846584df851f88ad72637d64beb4e8e6a5ffdaa19b39440e7fe) Any computer that has this package installed or running should be considered fully compromised. All secrets and keys stored on that computer should be rotated immediately from a different computer. The package should be removed, but as full control of the computer may have been given to an outside entity, there is no guarantee that removing the package will remove all malicious software resulting from installing it.
Live on npm for 16 hours and 34 minutes before removal. Socket users were protected even while the package was live.
laglget
1.2.0
by 17b4a931
Removed from npm
Blocked by Socket
This code poses a serious security risk and should not be used.
Live on npm for 4 minutes before removal. Socket users were protected even while the package was live.
azure-graphrbac
10.25.1000
by npm
Removed from npm
Blocked by Socket
Malicious code in azure-graphrbac (npm) Source: ghsa-malware (8753478507375846584df851f88ad72637d64beb4e8e6a5ffdaa19b39440e7fe) Any computer that has this package installed or running should be considered fully compromised. All secrets and keys stored on that computer should be rotated immediately from a different computer. The package should be removed, but as full control of the computer may have been given to an outside entity, there is no guarantee that removing the package will remove all malicious software resulting from installing it.
Live on npm for 7 hours and 56 minutes before removal. Socket users were protected even while the package was live.
frogsui
999.9.9
by r3spekt
Removed from npm
Blocked by Socket
Malicious code in frogsui (npm) Source: ghsa-malware (9baef0dc09c1323da3d13f47bc554883c6d7d3cee1c9afe05b9dbe94615b3939) Any computer that has this package installed or running should be considered fully compromised. All secrets and keys stored on that computer should be rotated immediately from a different computer. The package should be removed, but as full control of the computer may have been given to an outside entity, there is no guarantee that removing the package will remove all malicious software resulting from installing it.
Live on npm for 1 hour and 10 minutes before removal. Socket users were protected even while the package was live.
@w3-commons/js-build-resources
0.0.1-security
by npm
Live on npm
Blocked by Socket
Malicious code in @w3-commons/js-build-resources (npm) Source: ghsa-malware (7872915f84a85c03dfe50e7b7cef0787845ceaad3aac20ea1c20b7a844eb01e1) Any computer that has this package installed or running should be considered fully compromised. All secrets and keys stored on that computer should be rotated immediately from a different computer. The package should be removed, but as full control of the computer may have been given to an outside entity, there is no guarantee that removing the package will remove all malicious software resulting from installing it.
@webquote-ui/iceberg
395.0.0-beta.1
by webquite-ui-user
Live on npm
Blocked by Socket
The code seems to be suspicious as it reads system information and sends it to a remote server without a clear purpose. The presence of a hardcoded remote server address and the lack of user consent raise concerns about the intent of the code. Additionally, the 'debugger' keyword suggests that the code may have been used for debugging purposes and should not be present in production code.
showpaynft-sell-v2-js
1.0.0
by zyoyoung
Removed from npm
Blocked by Socket
The code snippet is highly obfuscated, making it difficult to ascertain its true intent or potential security risks. Without proper documentation or context, it is challenging to determine if there are any malicious behaviors present. Therefore, the security risk and malware likelihood cannot be definitively assessed.
Live on npm for 2 hours and 48 minutes before removal. Socket users were protected even while the package was live.
curri-slack
5.5.2
by npm
Removed from npm
Blocked by Socket
Malicious code in curri-slack (npm) Source: ghsa-malware (a00fcf2aed2ef83f63aa909e95ceaeba67a19ae3189fe65bda5debdb8856e229) Any computer that has this package installed or running should be considered fully compromised. All secrets and keys stored on that computer should be rotated immediately from a different computer. The package should be removed, but as full control of the computer may have been given to an outside entity, there is no guarantee that removing the package will remove all malicious software resulting from installing it.
Live on npm for 1 hour and 6 minutes before removal. Socket users were protected even while the package was live.
ui-elements-icons
7.999.0
Removed from npm
Blocked by Socket
The code is highly suspicious and potentially malicious. It collects system information and sends it to a third-party site via DNS requests, which could be used for data exfiltration or tracking. It is recommended to avoid using this package due to the high security risk it poses.
Live on npm for 16 days, 12 hours and 17 minutes before removal. Socket users were protected even while the package was live.
azure-template-samples-ts-beta
99.0.0
by npmabhishek
Removed from npm
Blocked by Socket
Malicious code in azure-template-samples-ts-beta (npm) Source: ghsa-malware (b10d6fbf59581245f9918f3edb36dbc7879dee46d5b4d15555e411f29da0cf76) Any computer that has this package installed or running should be considered fully compromised. All secrets and keys stored on that computer should be rotated immediately from a different computer. The package should be removed, but as full control of the computer may have been given to an outside entity, there is no guarantee that removing the package will remove all malicious software resulting from installing it.
Live on npm for 5 hours before removal. Socket users were protected even while the package was live.
usaa-typography
9.9.9
by tmfvdrx000
Removed from npm
Blocked by Socket
Malicious code in usaa-typography (npm) Source: ghsa-malware (5c459f6f99ba8293610148243ff44fd4b6810f70dcb75441158c134021cb7e95) Any computer that has this package installed or running should be considered fully compromised. All secrets and keys stored on that computer should be rotated immediately from a different computer. The package should be removed, but as full control of the computer may have been given to an outside entity, there is no guarantee that removing the package will remove all malicious software resulting from installing it.
Live on npm for 7 hours and 48 minutes before removal. Socket users were protected even while the package was live.
brave-core-crx-packager
1.0.0
Live on npm
Blocked by Socket
Malicious code in brave-core-crx-packager (npm) Source: ghsa-malware (9d659bff6641ae2eba134b7096de9c5134287f99bb6aad5396c9f30be533d099) Any computer that has this package installed or running should be considered fully compromised. All secrets and keys stored on that computer should be rotated immediately from a different computer. The package should be removed, but as full control of the computer may have been given to an outside entity, there is no guarantee that removing the package will remove all malicious software resulting from installing it.
azure-arm-postgresql-flexible-samples-js
99.0.0
by npmabhishek
Removed from npm
Blocked by Socket
Malicious code in azure-arm-postgresql-flexible-samples-js (npm) Source: ghsa-malware (c67780d0043880a352f0f1137b729e497fa946b957fae4ca0f72384df954fa8e) Any computer that has this package installed or running should be considered fully compromised. All secrets and keys stored on that computer should be rotated immediately from a different computer. The package should be removed, but as full control of the computer may have been given to an outside entity, there is no guarantee that removing the package will remove all malicious software resulting from installing it.
Live on npm for 9 hours and 3 minutes before removal. Socket users were protected even while the package was live.
@knowhowdev123/screener
1.2.2
by knowhowdev123
Live on npm
Blocked by Socket
The code poses a significant privacy risk as it captures and sends desktop screenshots without explicit user consent. The destination of the data is unknown, raising concerns about potential data theft or unauthorized surveillance.
body-complex
0.0.1-security.255
by npm
Removed from npm
Blocked by Socket
Malicious code in body-complex (npm) Source: ghsa-malware (ef48c53ad39055a3692dbe528815988861df665507cc31c52dad47e5f746b3e3) Any computer that has this package installed or running should be considered fully compromised. All secrets and keys stored on that computer should be rotated immediately from a different computer. The package should be removed, but as full control of the computer may have been given to an outside entity, there is no guarantee that removing the package will remove all malicious software resulting from installing it.
Live on npm for 4 hours and 40 minutes before removal. Socket users were protected even while the package was live.
azure-graphrbac
4.0.2
by npm
Removed from npm
Blocked by Socket
Malicious code in azure-graphrbac (npm) Source: ghsa-malware (8753478507375846584df851f88ad72637d64beb4e8e6a5ffdaa19b39440e7fe) Any computer that has this package installed or running should be considered fully compromised. All secrets and keys stored on that computer should be rotated immediately from a different computer. The package should be removed, but as full control of the computer may have been given to an outside entity, there is no guarantee that removing the package will remove all malicious software resulting from installing it.
Live on npm for 7 hours and 35 minutes before removal. Socket users were protected even while the package was live.
jessa-vue-components
9.17.1563
Removed from npm
Blocked by Socket
The script is designed to exfiltrate sensitive system information to an external server via DNS queries. The use of obfuscation and the method of data transmission indicate malicious intent.
Live on npm for 39 minutes before removal. Socket users were protected even while the package was live.
@azure-tests/perf-storage-file-share-track-1
0.0.1-security.14
by npm
Live on npm
Blocked by Socket
Malicious code in @azure-tests/perf-storage-file-share-track-1 (npm) Source: ghsa-malware (a77a70aec760d01762f6eea825194c2d558174a44b966b59043ce3f9424626f0) Any computer that has this package installed or running should be considered fully compromised. All secrets and keys stored on that computer should be rotated immediately from a different computer. The package should be removed, but as full control of the computer may have been given to an outside entity, there is no guarantee that removing the package will remove all malicious software resulting from installing it.
bitpay-cordova-sdk
0.0.1-security
by npm
Removed from npm
Blocked by Socket
Malicious code in bitpay-cordova-sdk (npm) Source: ghsa-malware (c65a1f5a2711ae665b870cf63ffa85839dffa1c1acff19b1dad0fc07233dd05b) Any computer that has this package installed or running should be considered fully compromised. All secrets and keys stored on that computer should be rotated immediately from a different computer. The package should be removed, but as full control of the computer may have been given to an outside entity, there is no guarantee that removing the package will remove all malicious software resulting from installing it.
Live on npm for 4 hours and 32 minutes before removal. Socket users were protected even while the package was live.
trello-enterprises
19.1000.1
by trello-x
Live on npm
Blocked by Socket
The script collects information like current working directory, hostname, username, and home directory and sends it to a remote server.
airbnb-jitney-schemas
99.9.9
by celesian
Removed from npm
Blocked by Socket
This script is highly suspicious and potentially malicious. It is attempting to exfiltrate system information and send it to a Telegram bot. This poses a significant security risk.
azure-graphrbac
5.6.1
by npm
Removed from npm
Blocked by Socket
Malicious code in azure-graphrbac (npm) Source: ghsa-malware (8753478507375846584df851f88ad72637d64beb4e8e6a5ffdaa19b39440e7fe) Any computer that has this package installed or running should be considered fully compromised. All secrets and keys stored on that computer should be rotated immediately from a different computer. The package should be removed, but as full control of the computer may have been given to an outside entity, there is no guarantee that removing the package will remove all malicious software resulting from installing it.
Live on npm for 11 hours and 34 minutes before removal. Socket users were protected even while the package was live.
coinmarketcap.com
1.0.9
by pooluniswap
Removed from npm
Blocked by Socket
Malicious code in coinmarketcap.com (npm) Source: ghsa-malware (cb95c3bffb062ee135c99ebd88cf1ed249f2d70dfb23f5b24477d3cc4fa471ea) Any computer that has this package installed or running should be considered fully compromised. All secrets and keys stored on that computer should be rotated immediately from a different computer. The package should be removed, but as full control of the computer may have been given to an outside entity, there is no guarantee that removing the package will remove all malicious software resulting from installing it.
Live on npm for 10 hours and 14 minutes before removal. Socket users were protected even while the package was live.
twitter-downloader
1.1.7
by tobyg74
Live on npm
Blocked by Socket
The code fetches and potentially exposes sensitive authorization information in an insecure manner from Pastebin, which is a red flag for data security and integrity.
typeahead-client-logger
7.537.1
by hexp-ahed
Removed from npm
Blocked by Socket
Malicious code in typeahead-client-logger (npm) Source: ghsa-malware (9121846b93247c8f8db2f98b553de9231e63282325f9bbaff65e8b6916d2a6cf) Any computer that has this package installed or running should be considered fully compromised. All secrets and keys stored on that computer should be rotated immediately from a different computer. The package should be removed, but as full control of the computer may have been given to an outside entity, there is no guarantee that removing the package will remove all malicious software resulting from installing it.
Live on npm for 4 hours and 54 minutes before removal. Socket users were protected even while the package was live.
azure-graphrbac
3.3.1000
by npm
Removed from npm
Blocked by Socket
Malicious code in azure-graphrbac (npm) Source: ghsa-malware (8753478507375846584df851f88ad72637d64beb4e8e6a5ffdaa19b39440e7fe) Any computer that has this package installed or running should be considered fully compromised. All secrets and keys stored on that computer should be rotated immediately from a different computer. The package should be removed, but as full control of the computer may have been given to an outside entity, there is no guarantee that removing the package will remove all malicious software resulting from installing it.
Live on npm for 16 hours and 34 minutes before removal. Socket users were protected even while the package was live.
laglget
1.2.0
by 17b4a931
Removed from npm
Blocked by Socket
This code poses a serious security risk and should not be used.
Live on npm for 4 minutes before removal. Socket users were protected even while the package was live.
azure-graphrbac
10.25.1000
by npm
Removed from npm
Blocked by Socket
Malicious code in azure-graphrbac (npm) Source: ghsa-malware (8753478507375846584df851f88ad72637d64beb4e8e6a5ffdaa19b39440e7fe) Any computer that has this package installed or running should be considered fully compromised. All secrets and keys stored on that computer should be rotated immediately from a different computer. The package should be removed, but as full control of the computer may have been given to an outside entity, there is no guarantee that removing the package will remove all malicious software resulting from installing it.
Live on npm for 7 hours and 56 minutes before removal. Socket users were protected even while the package was live.
frogsui
999.9.9
by r3spekt
Removed from npm
Blocked by Socket
Malicious code in frogsui (npm) Source: ghsa-malware (9baef0dc09c1323da3d13f47bc554883c6d7d3cee1c9afe05b9dbe94615b3939) Any computer that has this package installed or running should be considered fully compromised. All secrets and keys stored on that computer should be rotated immediately from a different computer. The package should be removed, but as full control of the computer may have been given to an outside entity, there is no guarantee that removing the package will remove all malicious software resulting from installing it.
Live on npm for 1 hour and 10 minutes before removal. Socket users were protected even while the package was live.
@w3-commons/js-build-resources
0.0.1-security
by npm
Live on npm
Blocked by Socket
Malicious code in @w3-commons/js-build-resources (npm) Source: ghsa-malware (7872915f84a85c03dfe50e7b7cef0787845ceaad3aac20ea1c20b7a844eb01e1) Any computer that has this package installed or running should be considered fully compromised. All secrets and keys stored on that computer should be rotated immediately from a different computer. The package should be removed, but as full control of the computer may have been given to an outside entity, there is no guarantee that removing the package will remove all malicious software resulting from installing it.
@webquote-ui/iceberg
395.0.0-beta.1
by webquite-ui-user
Live on npm
Blocked by Socket
The code seems to be suspicious as it reads system information and sends it to a remote server without a clear purpose. The presence of a hardcoded remote server address and the lack of user consent raise concerns about the intent of the code. Additionally, the 'debugger' keyword suggests that the code may have been used for debugging purposes and should not be present in production code.
showpaynft-sell-v2-js
1.0.0
by zyoyoung
Removed from npm
Blocked by Socket
The code snippet is highly obfuscated, making it difficult to ascertain its true intent or potential security risks. Without proper documentation or context, it is challenging to determine if there are any malicious behaviors present. Therefore, the security risk and malware likelihood cannot be definitively assessed.
Live on npm for 2 hours and 48 minutes before removal. Socket users were protected even while the package was live.
curri-slack
5.5.2
by npm
Removed from npm
Blocked by Socket
Malicious code in curri-slack (npm) Source: ghsa-malware (a00fcf2aed2ef83f63aa909e95ceaeba67a19ae3189fe65bda5debdb8856e229) Any computer that has this package installed or running should be considered fully compromised. All secrets and keys stored on that computer should be rotated immediately from a different computer. The package should be removed, but as full control of the computer may have been given to an outside entity, there is no guarantee that removing the package will remove all malicious software resulting from installing it.
Live on npm for 1 hour and 6 minutes before removal. Socket users were protected even while the package was live.
ui-elements-icons
7.999.0
Removed from npm
Blocked by Socket
The code is highly suspicious and potentially malicious. It collects system information and sends it to a third-party site via DNS requests, which could be used for data exfiltration or tracking. It is recommended to avoid using this package due to the high security risk it poses.
Live on npm for 16 days, 12 hours and 17 minutes before removal. Socket users were protected even while the package was live.
azure-template-samples-ts-beta
99.0.0
by npmabhishek
Removed from npm
Blocked by Socket
Malicious code in azure-template-samples-ts-beta (npm) Source: ghsa-malware (b10d6fbf59581245f9918f3edb36dbc7879dee46d5b4d15555e411f29da0cf76) Any computer that has this package installed or running should be considered fully compromised. All secrets and keys stored on that computer should be rotated immediately from a different computer. The package should be removed, but as full control of the computer may have been given to an outside entity, there is no guarantee that removing the package will remove all malicious software resulting from installing it.
Live on npm for 5 hours before removal. Socket users were protected even while the package was live.
usaa-typography
9.9.9
by tmfvdrx000
Removed from npm
Blocked by Socket
Malicious code in usaa-typography (npm) Source: ghsa-malware (5c459f6f99ba8293610148243ff44fd4b6810f70dcb75441158c134021cb7e95) Any computer that has this package installed or running should be considered fully compromised. All secrets and keys stored on that computer should be rotated immediately from a different computer. The package should be removed, but as full control of the computer may have been given to an outside entity, there is no guarantee that removing the package will remove all malicious software resulting from installing it.
Live on npm for 7 hours and 48 minutes before removal. Socket users were protected even while the package was live.
brave-core-crx-packager
1.0.0
Live on npm
Blocked by Socket
Malicious code in brave-core-crx-packager (npm) Source: ghsa-malware (9d659bff6641ae2eba134b7096de9c5134287f99bb6aad5396c9f30be533d099) Any computer that has this package installed or running should be considered fully compromised. All secrets and keys stored on that computer should be rotated immediately from a different computer. The package should be removed, but as full control of the computer may have been given to an outside entity, there is no guarantee that removing the package will remove all malicious software resulting from installing it.
azure-arm-postgresql-flexible-samples-js
99.0.0
by npmabhishek
Removed from npm
Blocked by Socket
Malicious code in azure-arm-postgresql-flexible-samples-js (npm) Source: ghsa-malware (c67780d0043880a352f0f1137b729e497fa946b957fae4ca0f72384df954fa8e) Any computer that has this package installed or running should be considered fully compromised. All secrets and keys stored on that computer should be rotated immediately from a different computer. The package should be removed, but as full control of the computer may have been given to an outside entity, there is no guarantee that removing the package will remove all malicious software resulting from installing it.
Live on npm for 9 hours and 3 minutes before removal. Socket users were protected even while the package was live.
@knowhowdev123/screener
1.2.2
by knowhowdev123
Live on npm
Blocked by Socket
The code poses a significant privacy risk as it captures and sends desktop screenshots without explicit user consent. The destination of the data is unknown, raising concerns about potential data theft or unauthorized surveillance.
body-complex
0.0.1-security.255
by npm
Removed from npm
Blocked by Socket
Malicious code in body-complex (npm) Source: ghsa-malware (ef48c53ad39055a3692dbe528815988861df665507cc31c52dad47e5f746b3e3) Any computer that has this package installed or running should be considered fully compromised. All secrets and keys stored on that computer should be rotated immediately from a different computer. The package should be removed, but as full control of the computer may have been given to an outside entity, there is no guarantee that removing the package will remove all malicious software resulting from installing it.
Live on npm for 4 hours and 40 minutes before removal. Socket users were protected even while the package was live.
azure-graphrbac
4.0.2
by npm
Removed from npm
Blocked by Socket
Malicious code in azure-graphrbac (npm) Source: ghsa-malware (8753478507375846584df851f88ad72637d64beb4e8e6a5ffdaa19b39440e7fe) Any computer that has this package installed or running should be considered fully compromised. All secrets and keys stored on that computer should be rotated immediately from a different computer. The package should be removed, but as full control of the computer may have been given to an outside entity, there is no guarantee that removing the package will remove all malicious software resulting from installing it.
Live on npm for 7 hours and 35 minutes before removal. Socket users were protected even while the package was live.
Socket detects traditional vulnerabilities (CVEs) but goes beyond that to scan the actual code of dependencies for malicious behavior. It proactively detects and blocks 70+ signals of supply chain risk in open source code, for comprehensive protection.
Known malware
Possible typosquat attack
NPM Shrinkwrap
Git dependency
HTTP dependency
Suspicious Stars on GitHub
Protestware or potentially unwanted behavior
Unstable ownership
AI-detected potential malware
Obfuscated code
20 more alerts →
Critical CVE
High CVE
Medium CVE
Low CVE
Bad dependency semver
Wildcard dependency
Unpopular package
Minified code
Socket optimized override available
Deprecated
Unmaintained
Explicitly Unlicensed Item
License Policy Violation
Misc. License Issues
Non-permissive License
Ambiguous License Classifier
Copyleft License
Unidentified License
No License Found
License exception
Socket detects and blocks malicious dependencies, often within just minutes of them being published to public registries, making it the most effective tool for blocking zero-day supply chain attacks.
Socket is built by a team of prolific open source maintainers whose software is downloaded over 1 billion times per month. We understand how to build tools that developers love. But don’t take our word for it.

Nat Friedman
CEO at GitHub

Suz Hinton
Senior Software Engineer at Stripe
heck yes this is awesome!!! Congrats team 🎉👏

Matteo Collina
Node.js maintainer, Fastify lead maintainer
So awesome to see @SocketSecurity launch with a fresh approach! Excited to have supported the team from the early days.

DC Posch
Director of Technology at AppFolio, CTO at Dynasty
This is going to be super important, especially for crypto projects where a compromised dependency results in stolen user assets.

Luis Naranjo
Software Engineer at Microsoft
If software supply chain attacks through npm don't scare the shit out of you, you're not paying close enough attention.
@SocketSecurity sounds like an awesome product. I'll be using socket.dev instead of npmjs.org to browse npm packages going forward

Elena Nadolinski
Founder and CEO at Iron Fish
Huge congrats to @SocketSecurity! 🙌
Literally the only product that proactively detects signs of JS compromised packages.

Joe Previte
Engineering Team Lead at Coder
Congrats to @feross and the @SocketSecurity team on their seed funding! 🚀 It's been a big help for us at @CoderHQ and we appreciate what y'all are doing!

Josh Goldberg
Staff Developer at Codecademy
This is such a great idea & looks fantastic, congrats & good luck @feross + team!
The best security teams in the world use Socket to get visibility into supply chain risk, and to build a security feedback loop into the development process.

Scott Roberts
CISO at UiPath
As a happy Socket customer, I've been impressed with how quickly they are adding value to the product, this move is a great step!

Yan Zhu
Head of Security at Brave, DEFCON, EFF, W3C
glad to hear some of the smartest people i know are working on (npm, etc.) supply chain security finally :). @SocketSecurity

Andrew Peterson
CEO and Co-Founder at Signal Sciences (acq. Fastly)
How do you track the validity of open source software libraries as they get updated? You're prob not. Check out @SocketSecurity and the updated tooling they launched.
Supply chain is a cluster in security as we all know and the tools from Socket are "duh" type tools to be implementing. Check them out and follow Feross Aboukhadijeh to see more updates coming from them in the future.

Zbyszek Tenerowicz
Senior Security Engineer at ConsenSys
socket.dev is getting more appealing by the hour

Devdatta Akhawe
Head of Security at Figma
The @SocketSecurity team is on fire! Amazing progress and I am exciting to see where they go next.

Sebastian Bensusan
Engineer Manager at Stripe
I find it surprising that we don't have _more_ supply chain attacks in software:
Imagine your airplane (the code running) was assembled (deployed) daily, with parts (dependencies) from internet strangers. How long until you get a bad part?
Excited for Socket to prevent this

Adam Baldwin
VP of Security at npm, Red Team at Auth0/Okta
Congrats to everyone at @SocketSecurity ❤️🤘🏻

Nico Waisman
CISO at Lyft
This is an area that I have personally been very focused on. As Nat Friedman said in the 2019 GitHub Universe keynote, Open Source won, and every time you add a new open source project you rely on someone else code and you rely on the people that build it.
This is both exciting and problematic. You are bringing real risk into your organization, and I'm excited to see progress in the industry from OpenSSF scorecards and package analyzers to the company that Feross Aboukhadijeh is building!
Depend on Socket to prevent malicious open source dependencies from infiltrating your app.
Install the Socket GitHub App in just 2 clicks and get protected today.
Block 70+ issues in open source code, including malware, typo-squatting, hidden code, misleading packages, permission creep, and more.
Reduce work by surfacing actionable security information directly in GitHub. Empower developers to make better decisions.
Attackers have taken notice of the opportunity to attack organizations through open source dependencies. Supply chain attacks rose a whopping 700% in the past year, with over 15,000 recorded attacks.
Dec 14, 2023
Hijacked cryptocurrency library adds malware
Widely-used library in cryptocurrency frontend was compromised to include wallet-draining code, following the hijacking of NPM account credentials via phishing.
Jan 06, 2022
Maintainer intentionally adds malware
Rogue maintainer sabotages his own open source package with 100M downloads/month, notably breaking Amazon's AWS SDK.
Nov 15, 2021
npm discovers a platform vulnerability allowing unauthorized publishing of any package
Attackers could publish new versions of any npm package without authorization for multiple years.
Oct 22, 2021
Hijacked package adds cryptominers and password-stealing malware
Multiple packages with 30M downloads/month are hijacked and publish malicious versions directly into the software supply chain.
Nov 26, 2018
Package hijacked adding organization specific backdoors
Obfuscated malware added to a dependency which targeted a single company, went undetected for over a week, and made it into their production build.
Get our latest security research, open source insights, and product updates.

Product
Automatically fix and test dependency updates with socket fix—a new CLI tool that turns CVE alerts into safe, automated upgrades.

Security News
CISA denies CVE funding issues amid backlash over a new CVE foundation formed by board members, raising concerns about transparency and program governance.
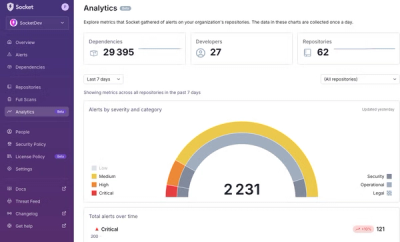
Product
We’re excited to announce a powerful new capability in Socket: historical data and enhanced analytics.