
Product
Introducing Webhook Events for Alert Changes
Add real-time Socket webhook events to your workflows to automatically receive software supply chain alert changes in real time.


Peter van der Zee

Eli Insua
July 28, 2025
We’re excited to announce that Socket now supports Scala and Kotlin in beta, building on our Java support and extending our coverage to more JVM-based ecosystems. This release enables teams working with modern JVM languages to leverage Socket’s powerful supply chain security and AI-powered threat detection.
With this expansion, developers using Scala or Kotlin can now benefit from the same proactive protection and deep package inspection that thousands of organizations already rely on to secure their software supply chain.
Scala and Kotlin are increasingly popular in enterprise and Android development:
As with any thriving open source ecosystem, dependencies in these languages are under relentless attack. The growing number of third-party libraries on MavenCentral and other registries presents a ripe target for supply chain attacks. Attackers exploit this trust with zero-day threats, malicious packages, typosquatting, telemetry, and protestware.
Socket’s mission is to detect and prevent these threats before they can compromise your applications. Our deep package inspection goes beyond traditional CVE-based scanning, analyzing actual code behavior to block malicious code before it lands in your code base.
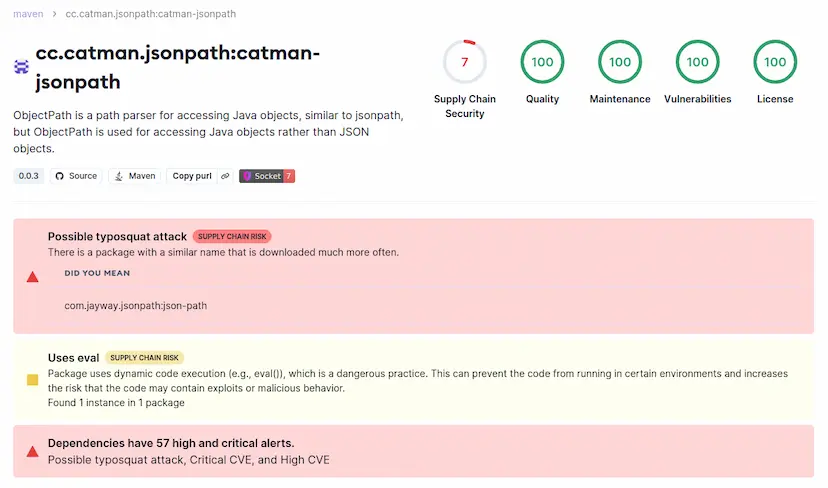
Over the past year, we’ve seen a rise in supply chain attacks targeting Maven packages, which are widely used across Java, Scala, and Kotlin projects. With so many mission-critical applications depending on these ecosystems, attackers see them as valuable entry points into enterprise infrastructure.
Recent examples include the discovery of a Maven package designed to exfiltrate OAuth credentials and a backdoor hidden in a malicious package impersonating the XZ for Java library.

Traditional Software Composition Analysis (SCA) tools, which rely solely on known CVEs, often miss these kinds of zero-day threats. Socket takes a different approach by inspecting packages for risky behaviors and malicious indicators in real time, including unexpected network calls, obfuscated code, and unsafe file system operations. With Socket, teams working with Scala or Kotlin can stop these threats before they reach production.
Note: Scala and Kotlin projects require using the Socket CLI only if you need to generate manifests (e.g., from sbt or Gradle builds without lockfiles). If your project already has a committed gradle.lockfile, you can skip manifest generation entirely and Socket will analyze the lockfile directly.
socket manifest scala command from your project root. This will invoke sbt to generate pom.xml files for your dependencies.socket scan create in the same directory to upload the manifest for analysis.socket manifest scala --help for details.Check out the documentation for Scala setup instructions.
Kotlin uses Gradle by default, so you can follow the general Gradle instructions:
socket cdxgen -t gradle -o socket-gradle.cdx.json --install-deps --lifecycle buildsocket manifest gradle to use your local Gradle setup.socket scan createIf your Kotlin or Scala project already uses Gradle, enabling lockfiles is the simplest approach:
dependencyLocking.lockAllConfigurations()Then run:
./gradlew dependencies --write-locksCommit the generated gradle.lockfile to source control, and Socket will automatically analyze it.
This release continues our mission to enable developers to secure their open source dependencies while still shipping fast. By supporting Java, Scala, and Kotlin, Socket now covers the entire JVM ecosystem with:
Whether you’re building a complex data pipeline in Scala, an Android app in Kotlin, or an enterprise monolith in Java, Socket brings the same level of protection to all your dependencies.
Install Socket’s free GitHub App and scan your JVM-based projects in just a few clicks. If you’re using Scala or Kotlin, follow the setup instructions above, and you’ll be ready to detect supply chain threats in minutes.
Subscribe to our newsletter
Get notified when we publish new security blog posts!
Try it now

Product
Add real-time Socket webhook events to your workflows to automatically receive software supply chain alert changes in real time.

Product
Socket now scans OpenVSX extensions, giving teams early detection of risky behaviors, hidden capabilities, and supply chain threats in developer tools.

Product
Bringing supply chain security to the next generation of JavaScript package managers