Dynamic require
Severity
Low
Short Description
Dynamic require can indicate the package is performing dangerous or unsafe dynamic code execution.
Suggestion
Packages should avoid dynamic imports when possible. Audit the use of dynamic require to ensure it is not executing malicious or vulnerable code.
Information
This alert indicates that the package uses require dynamically to load modules. Dynamic require calls can pose risks as they may introduce unsafe or malicious code into the application if not properly controlled.
Dynamic require allows loading modules at runtime based on dynamic input (e.g., require(variable) instead of require('module-name')). While it provides flexibility, it also presents several risks, including:
- Code Injection: If user inputs are passed unchecked to a dynamic
requirecall, attackers can load malicious modules or code. - Obfuscation: Dynamic
requirecan make the code harder to analyze, audit, or understand, increasing the chance of unnoticed vulnerabilities. - Supply Chain Risks: Improper use of dynamic imports may inadvertently introduce unverified third-party modules into the dependency tree.
Dynamic require usage should be carefully audited to ensure it is not being used for unsafe or insecure purposes.
Recommended actions
Audit Dynamic Require Usage:
- Identify all instances of dynamic
requirein the codebase. - Verify that the dynamically loaded modules are explicitly intended and safe.
Avoid Unnecessary Dynamic Imports:
- Refactor code to use static imports wherever possible (
require('module-name')orimport). - Replace dynamic logic with more predictable and secure patterns.
Validate Inputs:
- If dynamic
requireis unavoidable, sanitize and validate the inputs to prevent malicious module loading.
Review Module Sources:
- Ensure that any dynamically required module is from a trusted and verified source.
Consider Alternatives:
- Use
import()dynamically for modern ECMAScript modules, as they have more predictable behavior and are often easier to secure. - Use conditional logic to statically import modules that might otherwise be dynamically required.
Examples
Here's an example of a package flagged for the Dynamic Require alert.
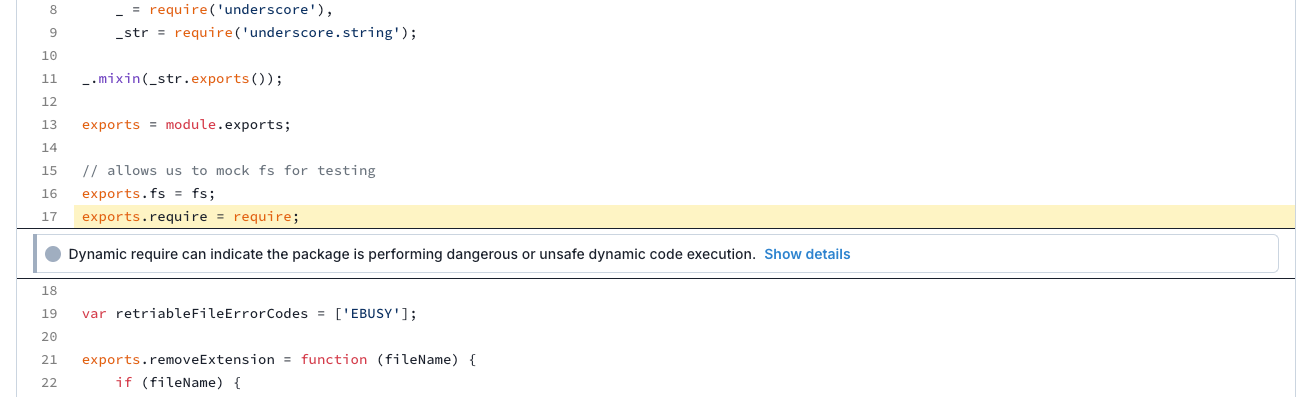
By exposing require, the package effectively enables dynamic imports at runtime, which is flagged because it can lead to:
- Code Injection: If user-provided input is passed to the exported
require, it could load malicious or untrusted modules. - Obfuscation: Makes the module harder to audit or analyze since the actual dependencies loaded at runtime may not be obvious from static analysis.
- Expanded Attack Surface: If the package is widely used, this dynamic behavior could increase the attack surface for potential exploits in consumer projects.
Detection Method
The Dynamic Require alert detects the exposure of Node.js's require function as it allows dynamic module imports, which could enable arbitrary code execution or code injection if user inputs are not validated.