Uses eval
Severity
Medium
Short Description
Package uses dynamic code execution (e.g., eval()), which is a dangerous practice. This can prevent the code from running in certain environments and increases the risk that the code may contain exploits or malicious behavior.
Suggestion
Avoid packages that use dynamic code execution like eval(), since this could potentially execute any code.
Information
The usesEval alert is generated when a package uses a Dynamic Execution Type function or similar code-evaluation methods. The eval() function is a powerful feature that allows code to be executed as a string. While it can be useful in some scenarios, it is generally considered dangerous and is often associated with security risks and performance issues.
Why is eval() Considered Dangerous?
- Security Risks:
- Injection Attacks: The use of
eval()can expose applications to injection attacks if user input is not properly sanitized. Attackers can inject malicious scripts that can be executed, leading to unauthorized access, data breaches, or other malicious activities. - Code Obfuscation: Malicious actors often use
eval()to obfuscate their code, making it difficult for security tools and developers to analyze and understand what the code does.
- Injection Attacks: The use of
- Performance Issues:
- Slow Execution:
eval()is slower than direct code execution because the JavaScript engine must interpret the string code at runtime. - Deoptimization: The use of
eval()can deoptimize the surrounding code, preventing the JavaScript engine from applying performance optimizations.
- Slow Execution:
When is eval() Used Legitimately?
While the use of eval() is generally discouraged, there are some legitimate scenarios where it might be used, such as:
- Dynamic Code Execution: Applications that need to execute dynamically generated code might use
eval(). - Parsing JSON in Legacy Code: Before the introduction of
JSON.parse(),eval()was sometimes used to parse JSON strings.
Recommended actions
If your project depends on a package that uses eval(), consider the following actions:
- Review the Code:
- Inspect the package code to understand why
eval()is being used. - Determine if the use of
eval()is necessary and whether it poses a security risk.
- Inspect the package code to understand why
- Seek Alternatives:
- Look for alternative libraries or packages that offer similar functionality without using
eval(). - Consider replacing or rewriting parts of the code that use
eval()with safer alternatives.
- Look for alternative libraries or packages that offer similar functionality without using
- Monitor and Restrict Usage:
- If you must use a package with
eval(), closely monitor the usage to ensure it does not introduce security vulnerabilities. - Use Content Security Policy (CSP) headers to restrict the use of
eval()in your application.
- If you must use a package with
Examples
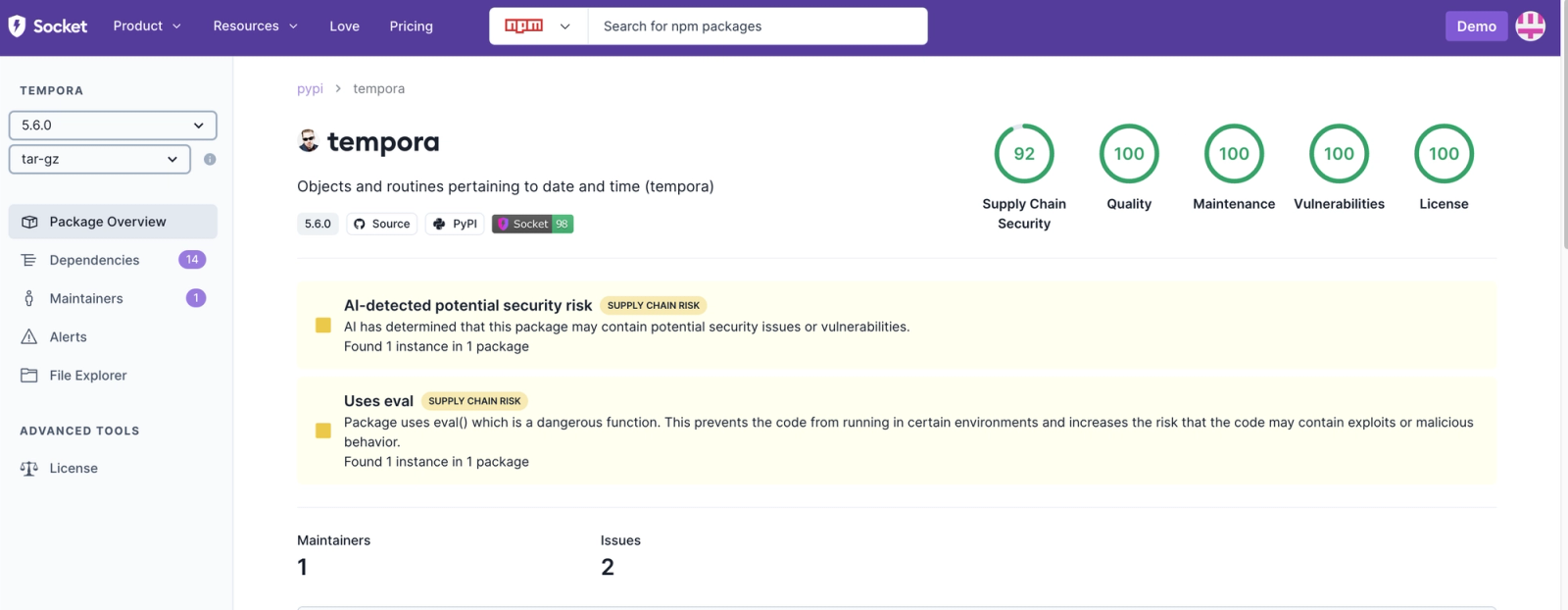
- Package Name: tempora 5.6.0
Description: This package makes use ofeval()to dynamically evaluate expressions, which can introduce security risks if not properly sanitized. Evaluating code dynamically witheval()can lead to injection vulnerabilities, especially when handling untrusted input. It is recommended to review the use ofeval()within this package and consider safer alternatives for executing dynamic code.
Detection Method
Socket's detection for a Dynamic Execution Type function is based on a set of heuristics that analyze its usage, context, and potential risks. The system flags direct uses of eval() type functions due to the ability to execute arbitrary code, often making them targets for exploitation. As we expand to support more programming languages, some languages like Java and C# don't have an eval() function but still allow dynamic code execution through reflection methods, like Function() in JavaScript.
Additional resources
To learn more about the risks associated with eval() and how to mitigate them, check out the following resources: