
Research
/Security News
Shai Hulud Strikes Again (v2)
Another wave of Shai-Hulud campaign has hit npm with more than 500 packages and 700+ versions affected.


Sarah Gooding
December 8, 2023
Ransomware, one of the fastest growing cyber threats, has seen a resurgence in recent years, and continues to be a foremost concern among security professionals. Splunk’s most recent CISO report, which collected data from 350 CISO’s across 17 global industries, found that 90% reported suffering a disruptive attack on their organizations over the last year, and 47% of those experienced multiple attacks.
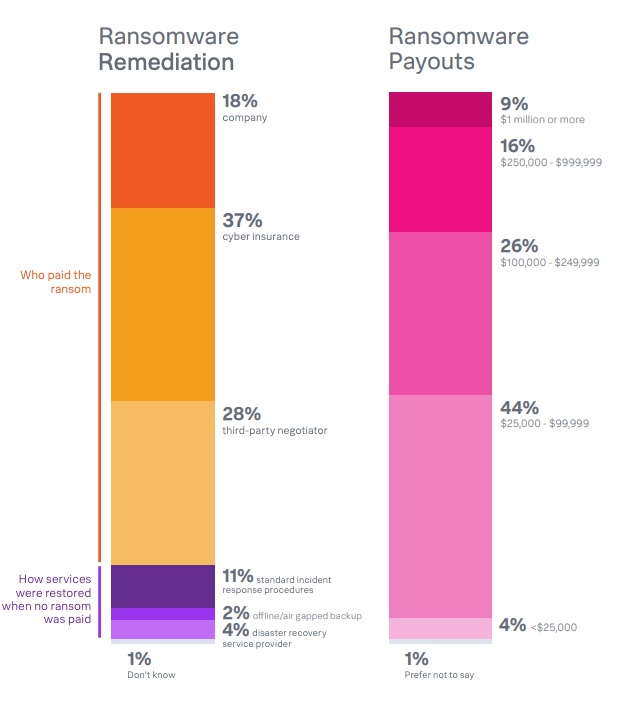
A staggering 96% of respondents were victims of ransomware attacks, with 52% experiencing one that significantly impacted their business systems and operations. While virtually all governments and law enforcement agencies recommend against paying a ransom, 83% of CISO respondents confirmed that they paid the ransom directly (18%), through cyber insurance (37%), or through a third party (28%). Ransoms ranged between $25,000 to $99,999 (44%), and half of respondents paid more than $100,000. Approximately 9% paid $1 million or more.
Ransomware threats are often featured prominently in the media and can have catastrophic financial outcomes. This is evident with recent high profile targets like Fidelity National Financial, where operations were paralyzed for a week, as they took down their own systems to contain the threat. In addition to ransoms paid, companies often bear the additional costs of security breaches, including loss of business, reputational damage, third-party liabilities, data loss, and regulatory notification costs.
In 2022, the FBI reported the Internet Crime Complaint Center (IC3) received 800,944 complaints, with reported financial losses of $10.3 billion. Ransomware attacks are not always reported, but 2,385 of these complaints were identified as ransomware with losses exceeding $34.3 million. Kapersky reported that targeted ransomware nearly doubled in 2022, as new groups have changed their techniques to favor precisely tailored ransomware attacks over opportunistic assaults. Payments are also better enabled by the maturing cryptocurrency industry.
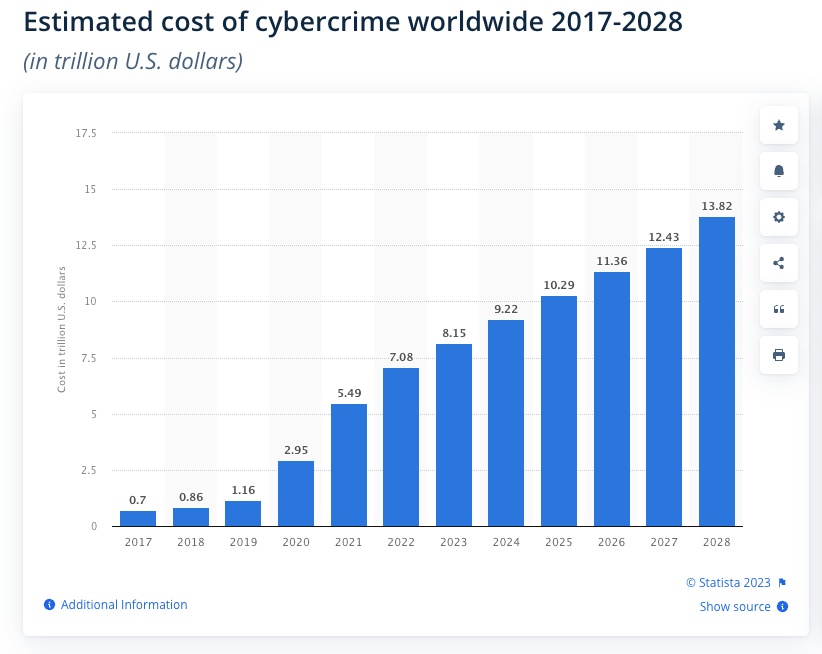
The increasing costs of ransomware attacks is a contributing factor to the cost of cybercrime worldwide. Statista’s “Estimated Cost of Cybercrime” in the cybersecurity market is forecast to continuously increase between 2023 and 2028 in total by $5.7 trillion dollars (+69.94%).
These forecasts and the current financial burden of crisis management following ransomware attacks has contributed to the growth of the cybersecurity insurance market. As businesses are increasingly adding cybersecurity insurance as part of their incident response plans, the market’s value is expected to reach $84.62 billion by 2030.
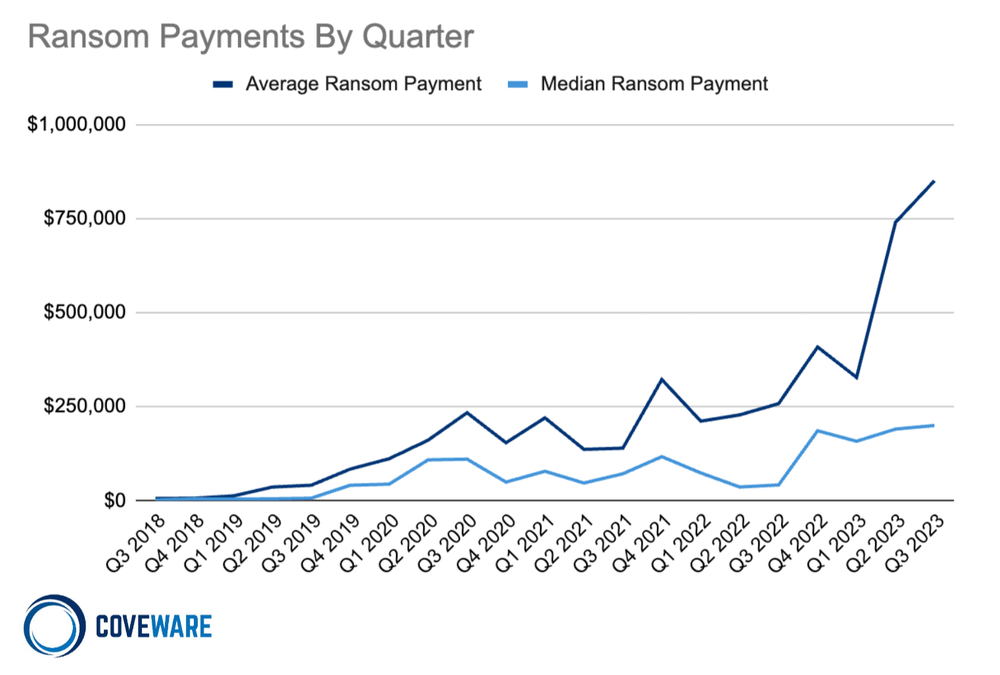
If you think you have been hit with inflation at the grocery store in the traditional marketplace, the rising cost of ransom demands demonstrates a similar trend within the ominous landscape of cyber threats. Covewear’s Q3 ransomware report pins the average ransomware payment at $850,700, a significant15% increase from the preceding quarter. Similarly, the median ransom payment experienced a modest uptick, reaching $200,000, reflecting a 5% rise from the previous quarter.
There is a profound disconnect between official advice from law enforcement and the vast majority of company policies when it comes to paying ransoms. Most respondents on Fortinet’s 2023 Global Ransomware Report whose enterprises fielded a ransomware attack have a policy that dictates they pay the ransom as requested. The report states that despite 72% detecting the incident within hours, sometimes minutes, more than 70% said they paid at least a portion of the ransom demanded, despite FBI guidance recommending no payment, as it doesn’t guarantee organizations will recover their data.
Claroty, a cyber-physical systems protection company, released new research this week on the state of industrial cybersecurity in 2023, which surveyed 1,100 information technology (IT) and operational technology (OT) security professionals. The research showed 75% of respondents worked at organizations that were targeted by ransomware attacks this year, and 69% confirmed they paid the ransom. More than half (54%) of those paid $100,000 USD or more. The demand for cyber insurance was high among respondents, as 80% of organizations already have cyber insurance policies and 49% are insured for half a million dollars or more.
The stakes are getting higher while almost 50% of organizations plan to reduce cybersecurity headcounts and infrastructure spending, while also reporting higher numbers of security incidents, according to a report from Observe. This necessitates a faster, more proactive response to the current threat landscape, from companies that plan to reduce security staff.
Adding more tools to the toolbox isn’t a guarantee that companies will be immune to attacks. Security teams need smarter tools that work in the background as a natural part of their workflows, with actionable alerts that continually raise the standard of security in response to more sophisticated threats.
It’s widely believed that large enterprises are the primary targets for ransomware, as they receive the most media attention, but reports show it’s not all “big game hunting.” Large institutions represent a much smaller percentage of lucrative targets.
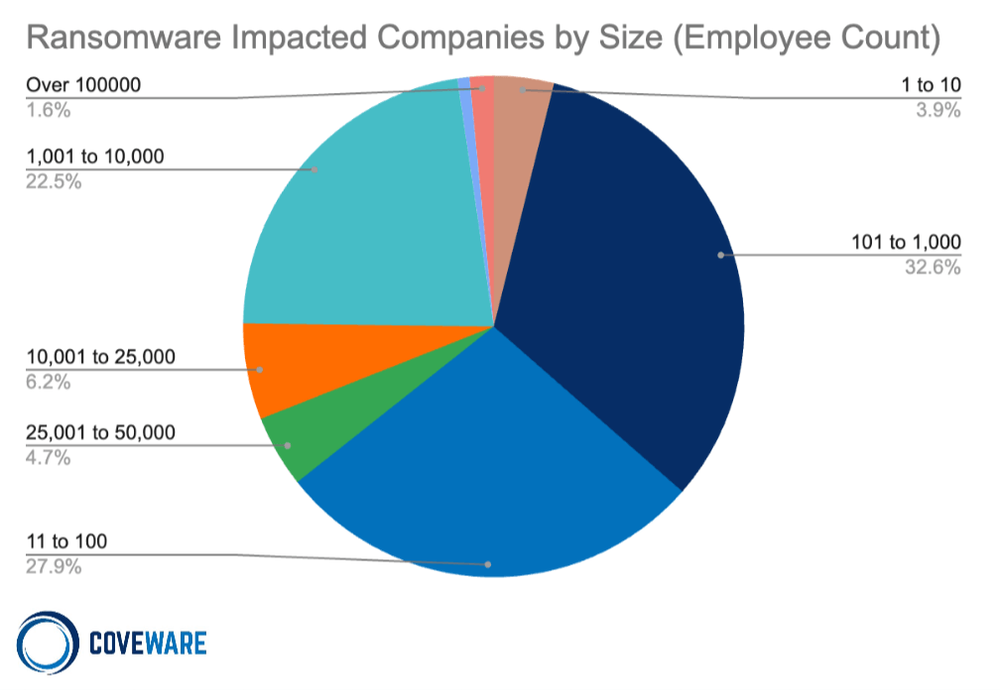
Coveware’s Q3 ransomware report shows a third of ransomware impacted companies have 101-1,000 employees, and nearly 28% have 11 to 100 employees. Just 1.6% of impacted companies have more than 100,000 employees. This hasn’t changed much since 2021, when the National Association of Insurance Commissioners reported that between 50 and 75% of ransomware attack victims are small businesses.
Although open source software has enabled engineering teams, both small and large, to move faster than ever before, it can also cause systems to come to a screeching halt when used to deliver malicious payloads as part of a ransomware attack. RDP compromise and email phishing remain the primary two attack vectors, but software vulnerability is trending higher as an entry point.
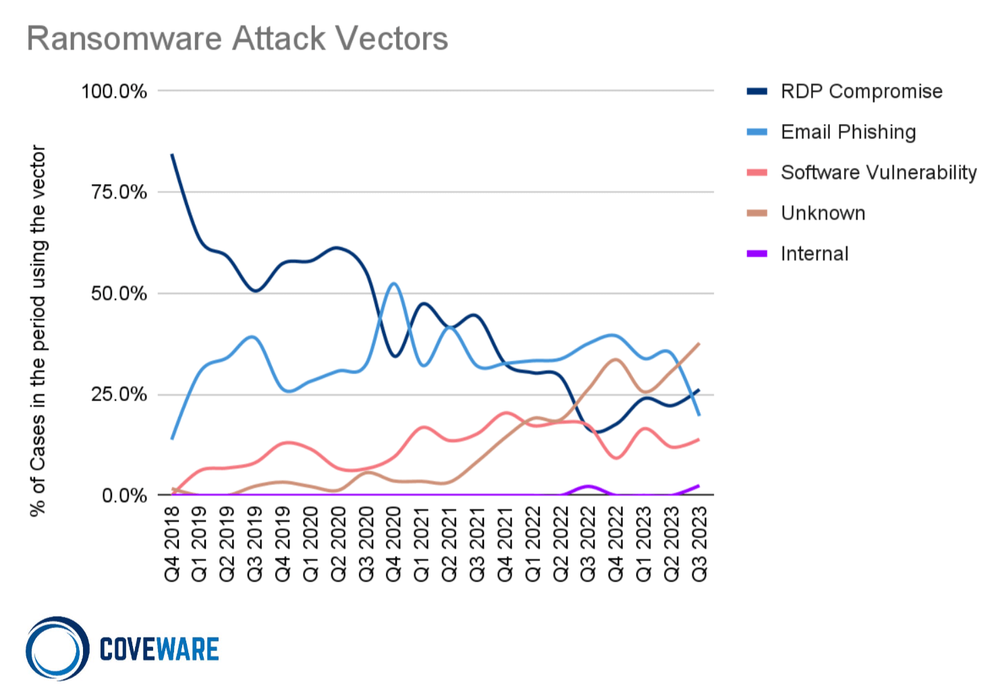
Coveware’s report infers that software vulnerability is likely a more common ransomware attack vector than this chart shows:
While the most common conclusion to an investigation in Q3 was unknown/undetermined entry vector, the subtext behind this trendline is as follows:
(1) a greater incidence of software vulnerability exploitation that leaves little-to-no forensic footprints that can be used to conclusively identify it as such, AND
(2) a continued reliance of ransomware actors on access brokers who may establish a foothold weeks or months ahead of the actual incident, whose access points cannot be confidently proven due to the expiration of critical forensic artifacts from the time of initial access.
Ransomware lurking in malicious open source packages is also a rising concern. Vulnerabilities in widely-used internet-facing technologies, such as the Log4j vulnerability, can and have been exploited by ransomware operators with a high impact.
As ransomware attack methods become increasingly more sophisticated, security professionals are moving to implement tools that utilize artificial intelligence (AI) and machine learning (ML) to speed up threat detection. Enterprises with inefficient processes that are slow to patch vulnerable systems will fall victim to breaches regardless of having the best tools in place.
Socket’s AI-driven threat analysis was created to help engineering teams get out ahead of these threats but cyber insurance sits on the other end of the spectrum, as a tool for remediating the damage following a security incident. The surge in ransomware attacks has driven up the demand for cyber insurance, as many businesses don’t have the financial capacity to pay the increasingly large sums that are often demanded by attackers.
A report from AM Best on the cyber insurance marekt’s first hard market cycle showed a 50% increase in premiums in 2022 to $7.2 billion:
Direct premiums written (DPW) has tripled in the past three years with surging demand, far outpacing that of the broader commercial lines industry by a wide margin. Calendar-year results improved dramatically in 2022 following two straight difficult years, as insurers benefited from continued rate increases, tighter underwriting and a decrease in ransomware attacks. Compared with 2021, the loss ratio fell 23 percentage points to 43% on standalone policies, and 18 percentage points to 48% on packaged policies.
Underwriters have managed to reduce their loss ratio on both standalone and packaged policies using tools to manage exposures.
“In addition to the rate increases, underwriters have cut limits, increased insureds’ own retention and improved risk selection,” AM Best senior industry analyst Christopher Graham said. “With the cyber universe expanding and becoming more complex with artificial intelligence creating new exposures and ransomware attacks returning to prominence in 2023, the demand for cyber coverage will only increase.”
The emerging cyber insurance market has a complicated relationship with ransomware response. Although it would be easy to conclude that cyber insurance companies are enabling the ransomware ecosystem by covering payments, the situation is more nuanced. Law enforcement’s black and white approach to ransom requests has resulted in a dearth of best practices for incident response.
Certainly if companies never paid ransoms, the ransomware industry would not have the lucrative business model that it operates on today. Combating ransomware requests has become even more complicated in the face of the emerging Ransomware-as-a-Service (RaaS) model where affiliates flock to the most effective ransomware strains.
Companies pay ransoms for a multitude of complex reasons. Sometimes paying is more economical than rebuilding IT systems and repairing reputational damage. Other times it’s driven by the threat of sensitive customer data being exposed. The company risks getting sued or investigated by a regulator. Lawyers frequently play a strong role in advising the company during incident response. Often the encrypted data stolen is vital for business continuity and companies may have no other way of recovering their losses to remain operational.
An exhaustive study from the Royal United Services Institute (RUSI) examined the role of cyber insurance in addressing the threats posed by ransomware. Researchers contend that there is “no compelling evidence that victims with cyber insurance are much more likely to pay ransoms than those without.” They concluded that “by linking improvements in security practices to coverage, cyber insurance is currently one of the few market-based levers for incentivizing organizations to implement security controls and resilience measures.”
RUSI’s research highlights the unique role that cyber insurance companies play in bringing some semblance of order to a ransomware victim's process for navigating sensitive decisions:
For victims, the decision to pay a ransom is a complex dilemma involving many factors, and it is rarely a silver bullet. Crucially, there is no strong evidence that insurers are encouraging victims to pay ransoms. In fact, it seems likely that most ransomware victims with cyber insurance make more informed decisions about ransom payments and generally handle incidents better than those without insurance.
At the same time, the potential role that cyber insurance could play in actively reducing the profitability of ransomware is limited by a lack of market-wide best practices for ransomware response, a lack of clarity over what constitutes a reasonable last resort for a ransom payment, and limited market penetration.
Cyber insurance companies have been instrumental in requiring companies to improve their security controls as a prerequisite for obtaining coverage and for setting acceptable limits for ransomware coverage. Many insurance companies are also willing to work together with those they insure to reduce their attack surface and respond in a timely way to known vulnerabilities. RUSI’s report includes an example of an underwriter that helped identify and remediate a critical Microsoft Exchange vulnerability in 2021:
“We were able to scan our entire book immediately as soon as that hit and find out how many of our clients had that vulnerability, and then we were on the phone, on the emails, getting them to remediate. So, we narrowed that down from 750 companies in our book that had that vulnerability to five or six within a matter of a couple of weeks.”
The 2023 cyber insurance market is responding to the rise in ransomware with higher premiums, more restricted and conditional coverage, and more rigorous security requirements, which can have a positive impact on reducing the profitability of ransomware operations. This is a rapidly evolving market where insurers are currently incentivized to help companies adopt better security practices to mitigate their risk.
Subscribe to our newsletter
Get notified when we publish new security blog posts!
Try it now

Research
/Security News
Another wave of Shai-Hulud campaign has hit npm with more than 500 packages and 700+ versions affected.

Security News
ENISA has become a CVE Program Root, giving the EU a central authority for coordinating vulnerability reporting, disclosure, and cross-border response.

Research
/Security News
Malicious npm packages use Adspect cloaking and fake CAPTCHAs to fingerprint visitors and redirect victims to crypto-themed scam sites.