
Security News
How Enterprise Security Is Adapting to AI-Accelerated Threats
Socket CTO Ahmad Nassri discusses why supply chain attacks now target developer machines and what AI means for the future of enterprise security.


Sarah Gooding
January 26, 2024
Want to get emailed every time one of your repositories has a critical vulnerability? Tines has a Socket integration for that!
Tines is a workflow automation platform geared towards security professionals. It supports a library of nearly 700 “Stories,“ which are pre-built workflows that anyone can use. These include integrations that work across a range of IT, engineering, and security products, similar to Zapier or IFTTT. There are Stories available for combining all kinds of actions, such as monitoring and deactivating long-lasting AWS IAM keys or uploading a file and searching VirusTotal to see if the hash has been scanned before.
Tines offers a visual interface for creating and managing automated workflows, designed for both technical and non-technical users to increase productivity by automating tasks that might otherwise require manual checks.
The team at Tines created an integration that generates a vulnerability report for an any repository that is protected by Socket. The report enables developers, organization leaders, auditors, and anyone else to get emails for critical vulnerabilities.
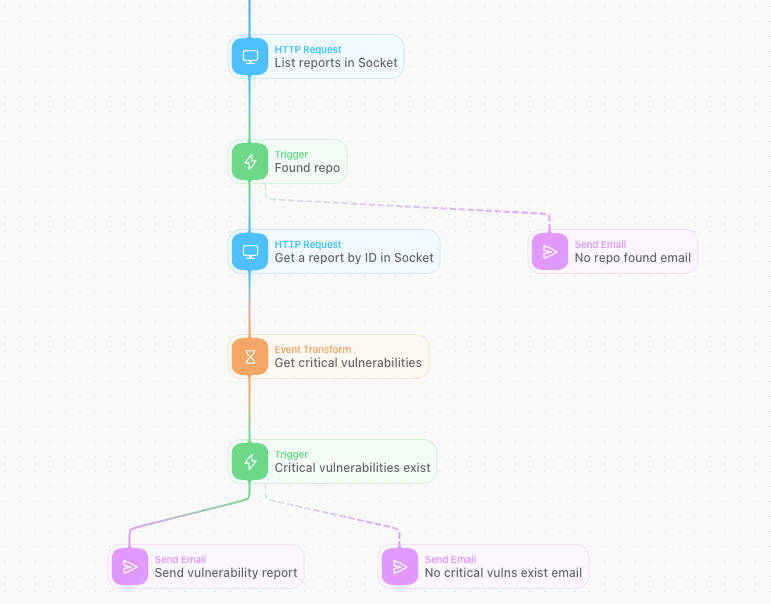
This Tines Story starts with a form that uses Socket’s API to fetch a report for a repository. If it doesn’t find a repository, the integration sends an email. If the repository is found, it gets the report by ID and gets the critical vulnerabilities.
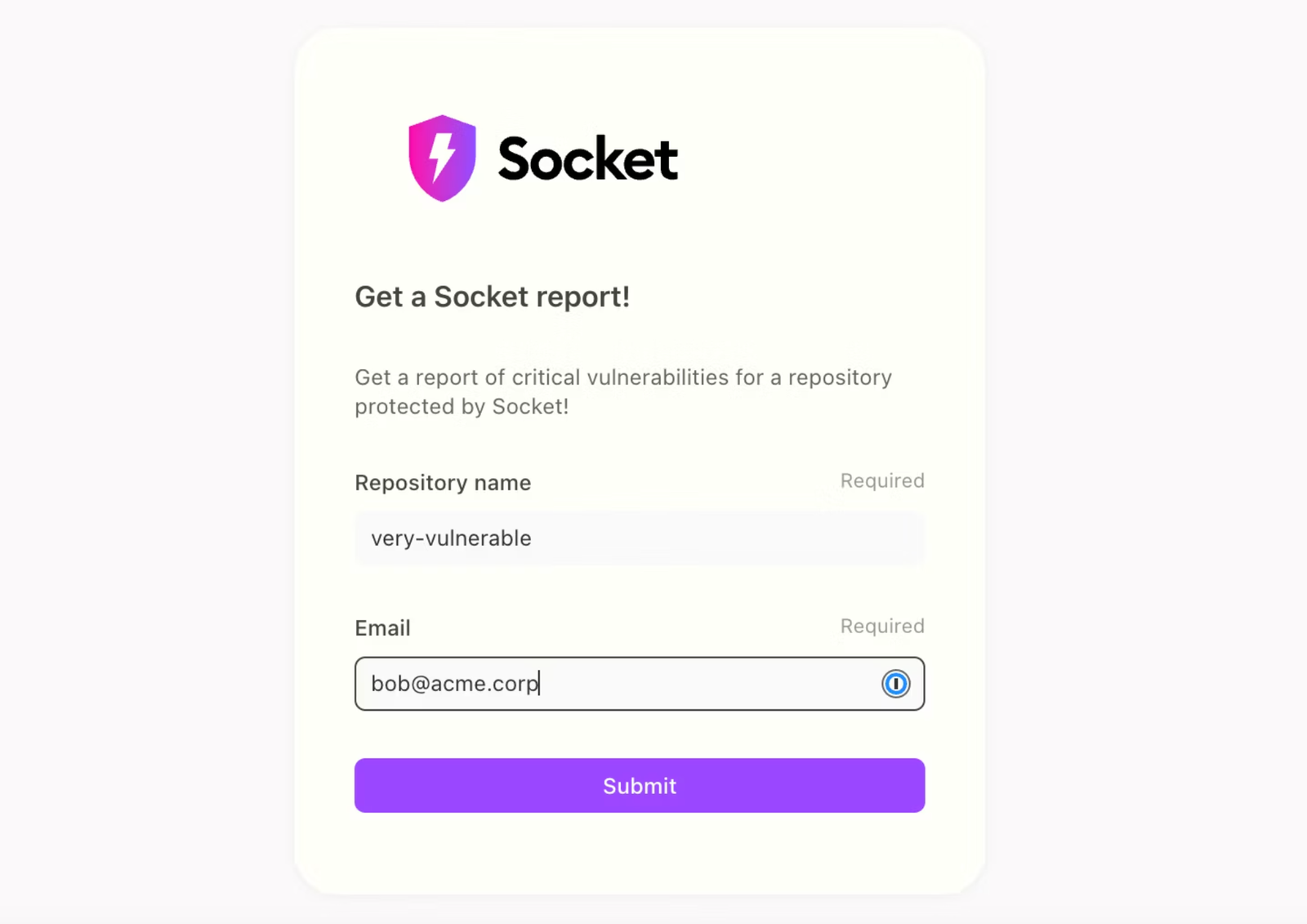
If no critical vulnerabilities exist, the report sends an email to the address submitted in the form. If it finds critical vulnerabilities, it sends an email listing them out.
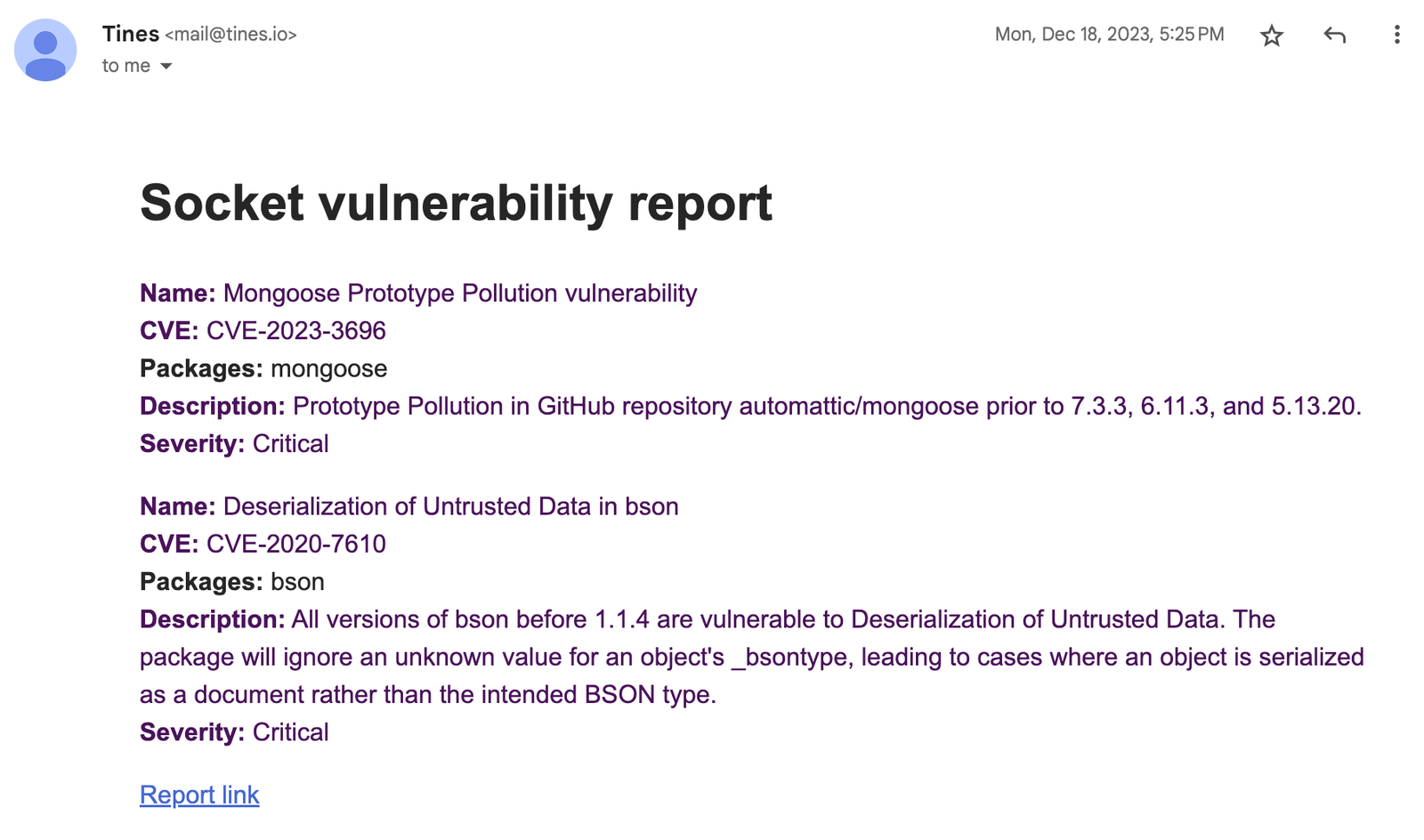
The email includes the name and description of the vulnerability with the CVE and severity, affected packages, and a link to the report.
Tines users can import this story to their tenants and further customize it to suit their unique needs.
Socket’s robust security scanning capabilities, combined with Tines’ automation features, makes it possible to get real-time critical vulnerability reports delivered directly to your inbox. It streamlines the process of monitoring and reporting vulnerabilities to different stakeholders, ensuring that security teams are instantly informed about potential risks in their software dependencies without having to grant additional access rights.
Subscribe to our newsletter
Get notified when we publish new security blog posts!
Try it now

Security News
Socket CTO Ahmad Nassri discusses why supply chain attacks now target developer machines and what AI means for the future of enterprise security.

Security News
Learn the essential steps every developer should take to stay secure on npm and reduce exposure to supply chain attacks.

Security News
Experts push back on new claims about AI-driven ransomware, warning that hype and sponsored research are distorting how the threat is understood.