Product
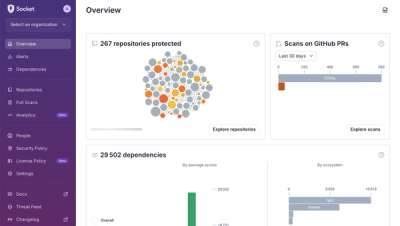
A New Overview in our Dashboard
We redesigned Socket's first logged-in page to display rich and insightful visualizations about your repositories protected against supply chain threats.
Security News

Last week, the idea of “ghost engineers” sparked a lively conversation across the tech world. It began with a viral tweet highlighting a hidden reality within software engineering: a subset of professionals in major tech companies who contribute minimal effort—often as little as two code changes per month at around five hours of work per week—while raking in $200-300K salaries.
According to Deedy Das, VC investor at Menlo Ventures, and many who confirmed his observations in the replies, this phenomenon isn’t confined to just the FAANG giants but extends to companies like Oracle, Salesforce, and Adobe.
The ghost engineer phenomenon is a new twist on the classic "quiet quitting" saga. This particular breed of top engineering talent, affectionately dubbed 0.1x-ers, has mastered the art of looking busy while perfecting excuses for delays.
Das highlighted a few tools of the trade from the “quiet quitting” playbook:
“And no, AI is not writing their code,” Das said. “Most of these people are chilling so hard they have no idea what AI can do.
“Most people in tech were never surprised that Elon could lay off 80% of Twitter, you can lay off 80% of most of these companies.”
Couple this with remote work, and you have a recipe for some engineers effectively disappearing into the ether, doing the bare minimum to remain employed.
Anyone working in tech for awhile will have heard whispers and rumors of ghost engineering jobs, but Stanford researcher Yegor Denisov-Blanch recently shared findings that take these reports from urban legend to a statistically backed reality.
By analyzing private Git repositories of over 50,000 engineers at 100 companies, researchers discovered:
The researchers’ model quantifies productivity by analyzing source code from private Git repos, simulating a panel of 10 experts evaluating each commit across multiple dimensions. Denisov-Blanch acknowledged that counting code commits is a flawed way to measure productivity but it can reveal inactivity. His team’s metric revealed that ~58% make <3 commits/month, and the other 42% make trivial changes, like editing one line or character--pretending to work.

The financial implications of having ghost engineers on the payroll are staggering when you look at companies that employ tens of thousands of engineers. Stanford researchers estimate that by letting go of their “ghost” workforce, companies like Cisco, Intuit, and IBM could save billions annually, adding $465 billion to combined market caps—with zero impact on performance. On a global scale, even a conservative estimate suggests more than $90 billion is effectively wasted on engineers who contribute little to nothing.

Denisov-Blanch contends that it’s not just about money. This inefficiency stifles innovation and creates a ripple effect throughout the entire tech ecosystem.
“It’s insane that ~9.5% of software engineers do almost nothing while collecting paychecks,” he said. “This unfairly burdens teams, wastes company resources, blocks jobs for others, and limits humanity’s progress. It has to stop.”
Denisov-Blanch said his team’s next paper is on using LLMs to measure developer productivity and should be available in a few weeks. Companies with 50+ engineers can participate in the research by connecting their git repositories.
Beyond the economic and productivity concerns, ghost engineers pose significant security risks. Their lack of meaningful engagement can lead to a few critical issues: unreviewed or improperly tested code changes, unnoticed vulnerabilities, and outdated systems left unpatched. A disengaged engineer might also miss—or deliberately ignore—critical security protocols, creating potential entry points for malicious actors.
When these engineers aren't actively involved in maintaining secure practices, they can create blind spots in a company’s defense strategy, increasing the risk of breaches or compliance failures. Threat actors can exploit disengaged engineers through phishing, social engineering, or leveraging neglected updates and poorly reviewed code to infiltrate systems and compromise security. Addressing these gaps requires better oversight and collaborative practices.
Before you start side-eyeing your coworkers, it’s worth noting that measuring productivity in software engineering is notoriously tricky. Commit counts or hours logged are often poor indicators of true impact. Some high-performing engineers—the mythical “10x engineers”—produce significant results with fewer, well-thought-out contributions.
However, the “ghost engineer” trend exposes systemic inefficiencies in talent management and performance evaluation. Remote work policies, once heralded as a game-changer, are now under the microscope. They’ve enabled flexibility for many but have also given rise to the ghost engineering phenomenon. The tug-of-war over remote versus in-office work is likely to intensify as companies grapple with these kinds of leadership and accountability issues.
Subscribe to our newsletter
Get notified when we publish new security blog posts!
Try it now

Product
We redesigned Socket's first logged-in page to display rich and insightful visualizations about your repositories protected against supply chain threats.

Product
Automatically fix and test dependency updates with socket fix—a new CLI tool that turns CVE alerts into safe, automated upgrades.

Security News
CISA denies CVE funding issues amid backlash over a new CVE foundation formed by board members, raising concerns about transparency and program governance.