
Security News
How Enterprise Security Is Adapting to AI-Accelerated Threats
Socket CTO Ahmad Nassri discusses why supply chain attacks now target developer machines and what AI means for the future of enterprise security.


Sarah Gooding
February 20, 2024
In a coordinated effort, dubbed “Operation Cronos,” international law enforcement organizations have disrupted LockBit, the world’s largest ransomeware gang. A combined task force including the U.K. National Crime Agency (NCA), Europol, and Eurojust, have seized control of LockBit's leak site and infrastructure.
In addition to dismantling 34 servers across Europe, the US, and the UK, police in Poland and Ukraine arrested two LockBit threat actors. The United States has also indicted two Russian nationals and imposed sanctions on LockBit affiliates. Authorities have frozen approximately 200 cryptocurrency accounts used by the gang and seized a massive amount of data.
“We have taken control of their infrastructure, seized their source code and obtained keys that will help victims decrypt their systems,” NCA director Graeme Biggar told journalists.
“Together, we have arrested, indicted or sanctioned some of the perpetrators and we have gained unprecedented and comprehensive access to Lockbit’s systems.
“As of today, Lockbit is effectively redundant. Lockbit has been locked out.”
Unlike the ALPHV/BlackCat disruption in December 2023, which both temporarily hobbled and inflamed the ransomware gang, the measures taken against LockBit appear to be more comprehensive.
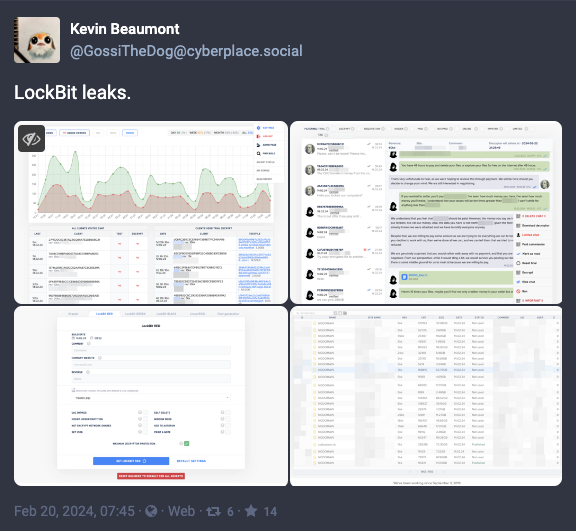
Multiple screenshots of the LockBit backend have been leaked (including images of source code), several responsible parties have been arrested and others sanctioned, and decryptor and recovery tool support for victims is now available.
“So there's loads more to come on the LockBit takedown, including new info on how they exfiltrate data and such,” security researcher Kevin Beaumont said.
“One extra bit of info - even after companies paid the ransom, LockBit were keeping the data - it was on the servers the NCA seized,” Beaumont noted, indirectly calling out companies that assured ICO and EU regulators that their data had been secured after paying off LockBit ransoms.
The fact that cybercriminals kept the data and didn't delete it comes as no surprise, but it would be interesting if authorities can determine how many victims paid out of sheer extortion compared to those who also were subject to data encryption.
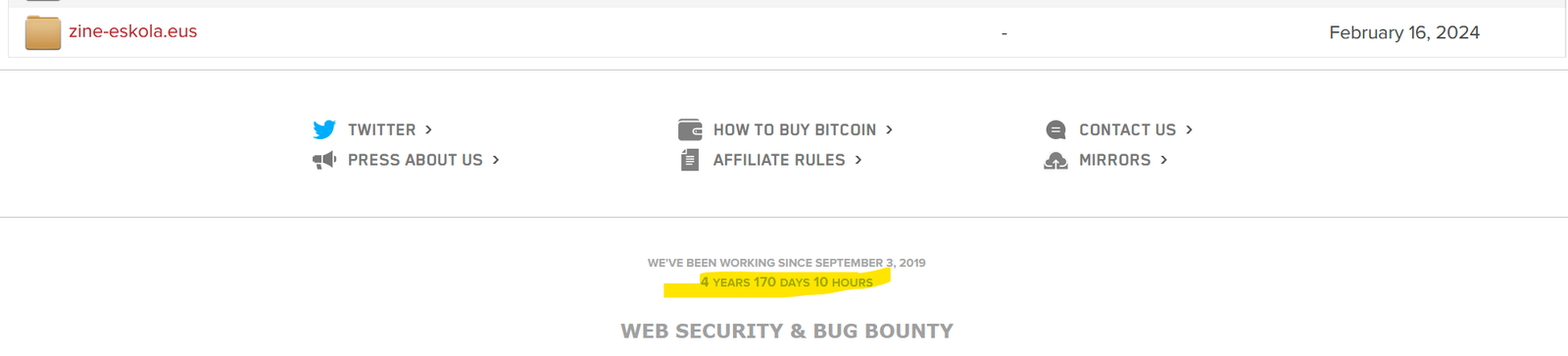
“It's pretty mind boggling to me that for 4 years 170 days, these guys have been doing horse carriage robbery of schools and hospitals and.. uh...they just did it,” Beaumont said. “Also, yes, they have a bug bounty that pays better than most large orgs.”
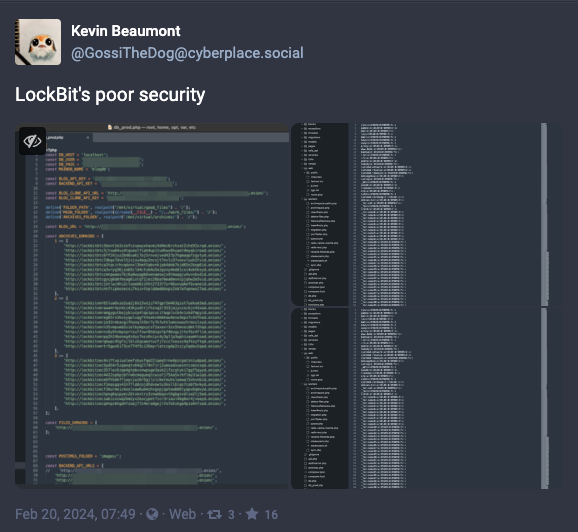
Security researchers speculated that law enforcement hacked LockBit using a PHP vulnerability. According to vx-underground, the infrastructure was compromised via an exploit of (CVE-2023-3824), a critical PHP vulnerability that could lead to a stack buffer overflow and potentially memory corruption or remote code execution.
LockBit’s ransomware-as-a-service (RaaS) operation claimed responsibility for many high-profile attacks since 2019, including the Royal Mail in the United Kingdom, Boeing, a Chicago children’s hospital, governments, schools, emergency services, and, most notably, the ICBC (Industrial and Commercial Bank of China). The group took a percentage of the paid ransoms from those to whom it licensed its ransomware software. According to the US Department of Justice (DOJ), LockBit and its affiliates compromised more than 2,000 victims worldwide, and received more $120 million in ransom payments.
Disrupting a group as prolific as LockBit is likely to change the trajectory of ransomware attacks in 2024 and will impact the balance of power among its rivals. Underwriters cited ransomware as the top threat, expected to drive cyber insurance premiums higher this year. LockBit’s elimination may create a power vacuum in the cybercriminal world, leading to increased competition among rival ransomware gangs eager to take the top spot.
“This is by far the most damaging blow to a ransomware group we have ever seen by a significant margin,” vx-underground commented on the LockBit takedown. “This is a homicide, the funeral, the final nail in the coffin, and the burial.”
Subscribe to our newsletter
Get notified when we publish new security blog posts!
Try it now

Security News
Socket CTO Ahmad Nassri discusses why supply chain attacks now target developer machines and what AI means for the future of enterprise security.

Security News
Learn the essential steps every developer should take to stay secure on npm and reduce exposure to supply chain attacks.

Security News
Experts push back on new claims about AI-driven ransomware, warning that hype and sponsored research are distorting how the threat is understood.