
Security News
Meet Socket at Black Hat Europe and BSides London 2025
Socket is heading to London! Stop by our booth or schedule a meeting to see what we've been working on.


Sarah Gooding
March 24, 2025
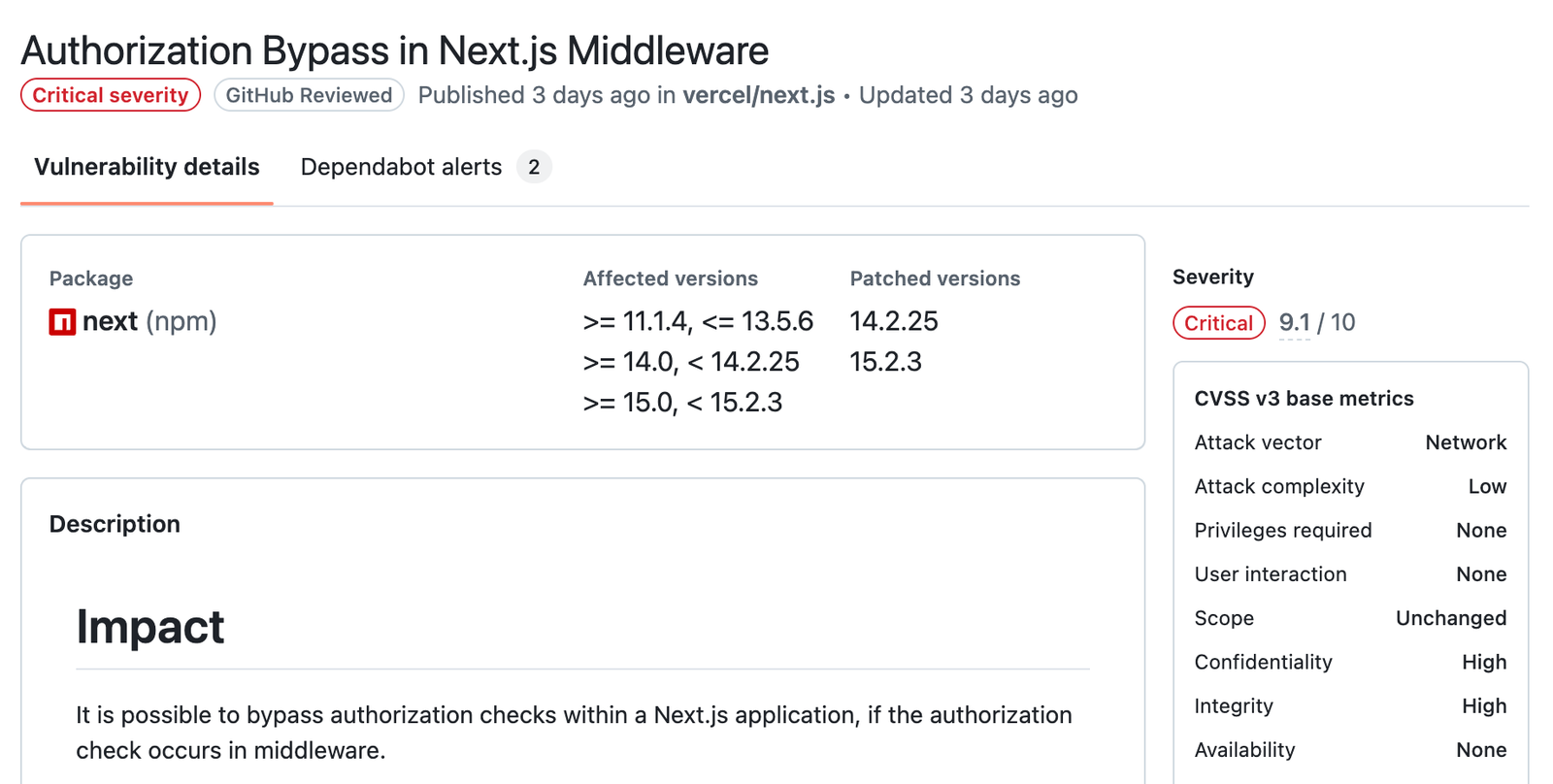
This weekend, the Next.js team released patches addressing a critical vulnerability (CVE-2025-29927) that allowed attackers to bypass middleware-based security checks, including authentication and authorization logic. The issue affected all self-hosted Next.js applications relying on next start with output: 'standalone', and remained present in all actively used major versions prior to the fix.
The vulnerability was discovered and responsibly disclosed by researchers Allam Rachid (zhero;) and Allam Yasser (inzo_), who published their findings in a detailed technical paper titled "Next.js and the Corrupt Middleware: the Authorizing Artifact." According to their research, the issue stems from how the framework processes the internal x-middleware-subrequest header.
“We recommend that all self-hosted Next.js deployments using next start and output: 'standalone' should update immediately,” wrote Lee Robinson, VP of Product at Vercel, in the official advisory.
The vulnerability arises from the misuse of the x-middleware-subrequest header, which is internally used to prevent infinite middleware recursion. The header can be spoofed by an external client. If it contains specific values matching the name of middleware paths, Next.js will skip running middleware entirely, forwarding requests directly to protected routes without triggering any of the logic meant to enforce access controls.
This creates a critical security issue for applications relying on middleware to enforce user authentication, authorization, or security headers. The researchers describe it as a "universal bypass key" that grants unauthenticated access to protected resources:
“The header and its value act as a universal key allowing rules to be overridden,” the researchers wrote in their publication. “We can now completely bypass the middleware, and therefore any protection system based on it, starting with authorization.”
The vulnerability affects all versions starting from 11.1.4 up to but not including the patched releases:
Applications hosted on Vercel or Netlify, or deployed as static exports, are not affected, as they do not execute middleware in the same context. For those unable to immediately patch, the advisory recommends filtering and blocking any external requests that include the x-middleware-subrequest header. Cloudflare has also deployed an automatic WAF rule to block requests that exploit the Next.js middleware auth bypass, and users can manually create a similar rule now from the dashboard under Security > WAF.
The researchers detailed how the vulnerability manifests differently across Next.js versions. In older versions (pre-12.2), bypassing middleware required constructing the header with legacy path formats such as pages/_middleware. In newer versions, especially those using the /src directory and the App Router introduced in v13, the logic changed slightly but remained vulnerable.
In recent versions (up to v15.2.2), the vulnerability depends on a constant called MAX_RECURSION_DEPTH. By including repeated middleware names in the header (e.g., middleware:middleware:middleware:middleware:middleware), the framework would treat the request as recursive and skip all middleware execution.
The paper also outlines real-world exploit examples, including:
The response timeline shows a short delay in triaging the full scope of the issue, but once confirmed, the Next.js team issued and backported patches within a matter of hours.
CVE-2025-29927 has been rated 9.1 (Critical) by GitHub, which maintains the Next.js advisory database. With Next.js downloaded over nine million times per week, this vulnerability has far-reaching implications, particularly for enterprises relying on middleware to enforce access controls.
“A critical vulnerability can occur in any software, but when it affects one of the most popular frameworks, it becomes particularly dangerous,” the researchers noted. “The risk is even greater when the vulnerability impacts a mature feature that users rely on for essential functions like authorization and authentication.”
All self-hosted users of Next.js are strongly advised to upgrade to the patched versions as soon as possible. For deployments where patching is not immediately feasible, blocking or sanitizing requests containing the x-middleware-subrequest header is a recommended temporary mitigation.
Developers are encouraged to audit their use of middleware to ensure it is not the sole line of defense for sensitive operations, especially in legacy versions.
Subscribe to our newsletter
Get notified when we publish new security blog posts!
Try it now

Security News
Socket is heading to London! Stop by our booth or schedule a meeting to see what we've been working on.

Security News
OWASP’s 2025 Top 10 introduces Software Supply Chain Failures as a new category, reflecting rising concern over dependency and build system risks.

Research
/Security News
Socket researchers discovered nine malicious NuGet packages that use time-delayed payloads to crash applications and corrupt industrial control systems.