
Research
/Security News
Shai Hulud Strikes Again (v2)
Another wave of Shai-Hulud campaign has hit npm with more than 500 packages and 700+ versions affected.


Kirill Boychenko
October 23, 2024
Evidence uncovered as part of an investigation by Socket's Threat Research Team strongly suggests that a new dark web bulletproof hosting provider, Noxia, is enabling cybercriminals to distribute malicious code and conduct software supply chain attacks by offering low-cost servers for hosting Python, Node.js, Go, and Rust applications.
On October 10, 2024, “noxia”, a member of the dark web forum “BreachForums”, posted an advertisement for Noxia (noxia[.]cloud) – a bulletproof hosting provider. The term “bulletproof” alludes to the fact that these infrastructure and services are provided to other threat actors for ostensibly malicious purposes, and operate outside of the purview of legitimate activity.
While bulletproof hosting advertisements are common among the criminal underground, and bulletproof hosting provides a range of services, Noxia claims the ability to host Python, Node.js, Go, and Rust applications. By acting as a platform for these applications, Noxia may be used as a malware distribution vector as it relates to software supply chains. Socket actively monitors, detects, and blocks supply chain attacks. When coupled with our Threat Research Team’s analysis, we are able to identify emergent threats like Noxia’s bulletproof hosting.

Figure 1: Noxia advertisement on BreachForums
Bulletproof hosting providers, as evidence suggests Noxia is, specifically advertise their services on dark web forums, enabling crime, and are a vital part of the underground economy. Bulletproof hosting providers are known to facilitate cybercrime, including ransomware attacks, and are often a target of law enforcement investigations and research by the information security community.
Noxia is renting servers configured for Python, Node.js, and Go for as little as £0.25 GBP ($0.32 USD) per month for the “basic” configuration. This low-cost subscription offers disposable infrastructure to threat actors who can cheaply create and discard multiple servers, making it harder for law enforcement and researchers to track their activities. Noxia’s website (noxia[.]cloud) has a seemingly legitimate appearance, and its service has not been widely reported on by the security community, which may allow traffic from their servers to bypass organizations’ security filters.
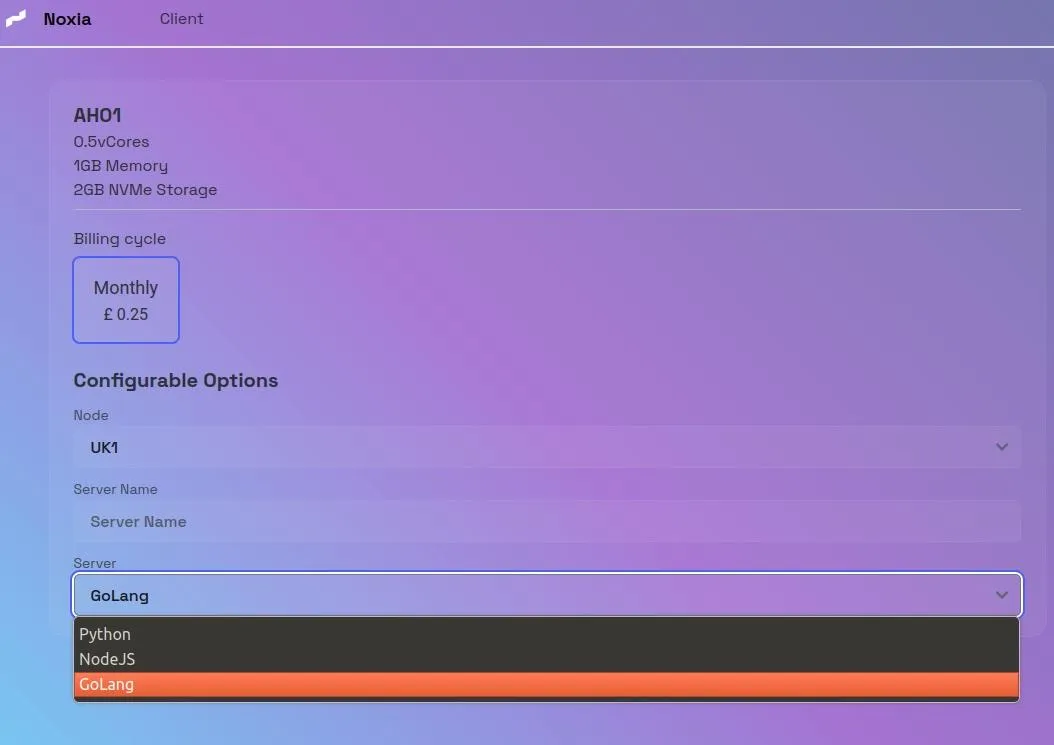
Figure 2: Noxia’s configurable server options for Python, Node.js, and Go
Additionally, threat actors can use Noxia’s servers for command and control (C2) servers, phishing, managing botnets, and hosting malicious software updates, which can lead to system compromise, if downloaded unknowingly.
Despite being new dark web bulletproof hosting provider on the block, Noxia is already participating in malicious campaigns, hosting malware at hxxp://uk1[.]noxia[.]cloud:10022/downloadFilesFrom[.]txt (filename “octane.exe”; SHA256: cb800cc9a220ac17e8f222b8c33f4afcc92b6d17b5453e19be99705806c32dc2) and hxxp://uk1[.]noxia[.]cloud:10022/version (filename “octane.exe”; SHA256: cc16da3e9a5d56c8a0ac96e1211acb8b728bf66dbaad24f15ad8190f7bedce72). Both files are flagged as “malicious” by 36 out of 72 and 6 out of 94 security vendors on VirusTotal respectively.
An additional analysis of these malware samples indicates a link between Noxia and the octane malware via the IP address 149.40.3[.]138 through their forward DNS records. A list of Noxia’s domains, subdomains, and associated IP addresses is included in the indicators of compromise (IOCs) section below.
Both octane.exe files contain a URL string pointing to octane[.]lol, which serves dozens of malicious files, according to VirusTotal. The octane[.]lol site is designed similarly to noxia[.]cloud and features an advertisement banner for Noxia.

Figure 3: Noxia’s banner on octane[.]lol
To protect themselves from attacks that use bulletproof hosting services like Noxia, developers should adopt a comprehensive security strategy focusing on supply chain security, dependency management, and proactive monitoring. Here’s how developers can safeguard their applications:
Socket offers robust solutions to enhance application security against software supply chain attacks through the use of:
Install the free Socket for GitHub app in two clicks to protect your repositories from vulnerable and malicious dependencies.
Noxia associated domains, subdomains, IP addresses:
MITRE ATT@CK:
Subscribe to our newsletter
Get notified when we publish new security blog posts!
Try it now

Research
/Security News
Another wave of Shai-Hulud campaign has hit npm with more than 500 packages and 700+ versions affected.

Security News
ENISA has become a CVE Program Root, giving the EU a central authority for coordinating vulnerability reporting, disclosure, and cross-border response.

Research
/Security News
Malicious npm packages use Adspect cloaking and fake CAPTCHAs to fingerprint visitors and redirect victims to crypto-themed scam sites.