
Research
/Security News
npm Malware Campaign Uses Adspect Cloaking to Deliver Malicious Redirects
Malicious npm packages use Adspect cloaking and fake CAPTCHAs to fingerprint visitors and redirect victims to crypto-themed scam sites.


Sarah Gooding
November 19, 2024
CVEs awaiting analysis by the NVD have broken the 20,000 mark, after the security community noticed its enrichment activity slowed to nearly a halt again last week. NIST failed to meet its self-imposed deadline of clearing the NVD's backlog by the end of the fiscal year. Meanwhile, CVE's awaiting analysis have increased 11% from ~18,000 in October.
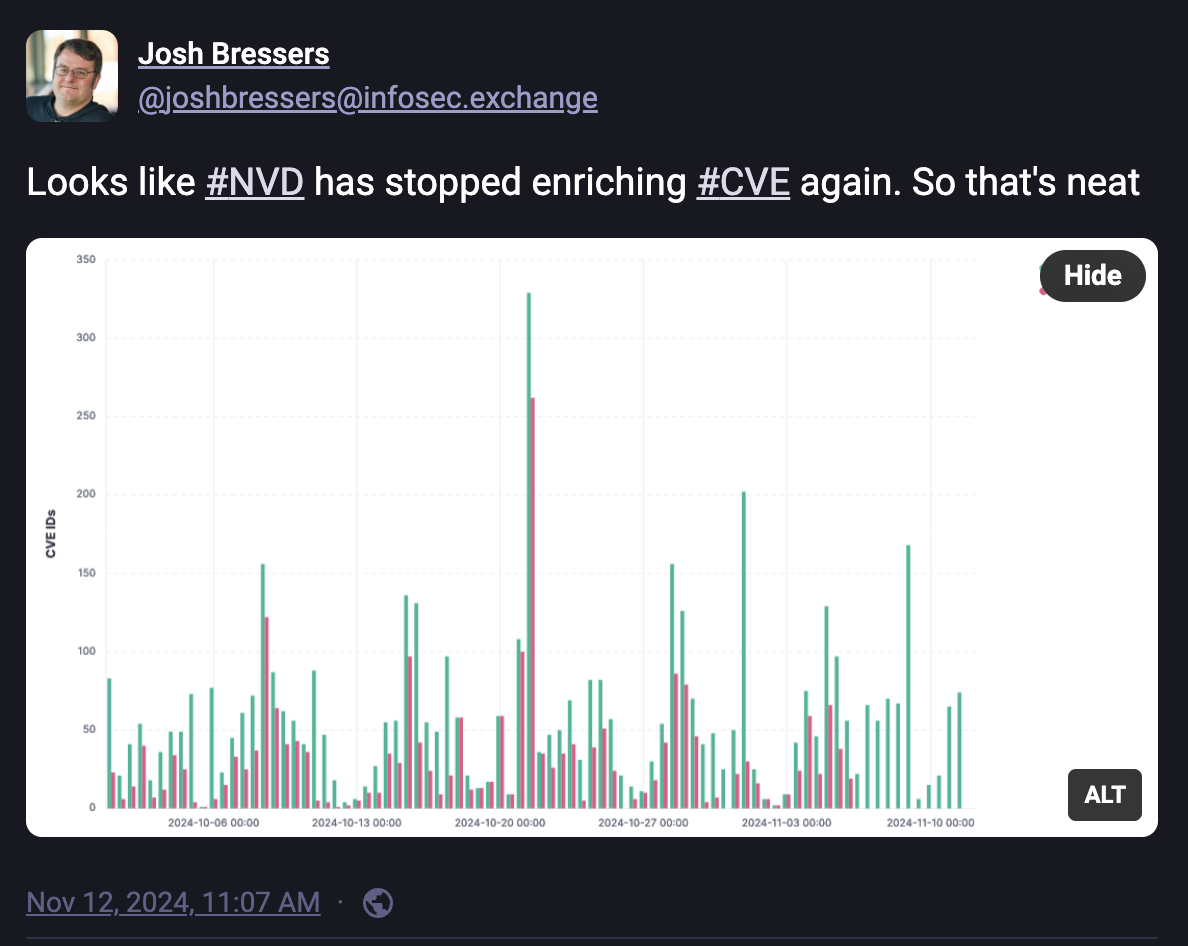
NIST didn’t acknowledge missing the deadline at the time. The latest update, published November 13, instead frames the issue as an ongoing challenge, stating that the earlier estimate was an "optimistic" timeline.
The latest announcement shifts the focus to technical hurdles with data formats from Authorized Data Providers (ADPs). This indirect admission sidesteps the earlier commitment, emphasizing the development of new systems to handle the incoming CVEs without directly addressing the impact of the delay on users or the broader security ecosystem:
This update provides information on our progress as we work to process all incoming Common Vulnerabilities and Exposures (CVEs) and to address the backlog of CVEs that built up earlier this calendar year.
We now have a full team of analysts on board, and we are addressing all incoming CVEs as they are uploaded into our system. In addition, we have addressed all Known Exploited Vulnerabilities (KEVs) that were in the backlog, and we are processing all new KEVs as they come in.
However, our initial estimate of when we would clear the backlog was optimistic. This is due to the fact that the data on backlogged CVEs that we are receiving from Authorized Data Providers (ADPs) are in a format that we are not currently able to efficiently import and enhance.
To address this issue, we are developing new systems that will allow us to process incoming ADP data more efficiently. We are working to complete this project as quickly as possible and will continue to provide updates on our progress to this NVD Updates page.
On November 15, the NVD published a technical update with a new plan to improve future processing capabilities. The NVD will deploy an update the week of November 18th to incorporate more data sources and improve record enrichment.
Key changes include:
The NVD also identified several changes to reference tags and CVE Record Change History, including the following:
Some search filters in the CVE API (e.g., HasCertAlerts, HasCertNotes, HasOval) and Vulnerability Search (e.g., US-CERT Alerts, Notes, OVAL Queries) will no longer work due to upstream removal of data points used by the NVD systems and will be phased out in a future update.
Although efforts are underway to build new systems capable of handling additional data, no timeline for clearing the backlog has been provided. While these promised updates might improve the quality of future data, they fail to compensate for the current gaps caused by the backlog and current processing inefficiencies.
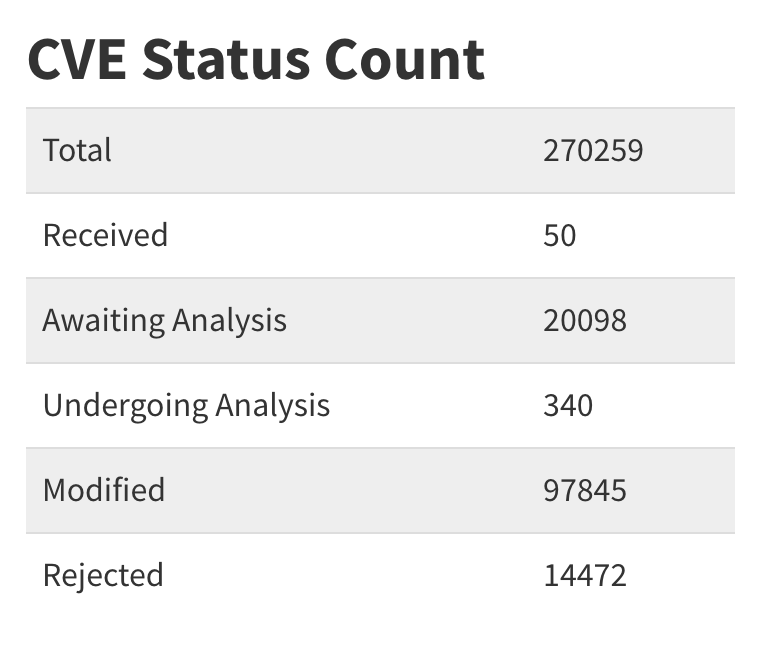
While the updates provide incremental improvements, some of these changes may introduce challenges and disruptions for tools relying on the NVD’s data. For security professionals, the message is clear: the NVD remains a critical resource, but its limitations and must be accounted for. Organizations should be supplementing NVD data with other sources while NIST continues to dig out from underneath the backlog of 20,000+ CVEs awaiting analysis.
Subscribe to our newsletter
Get notified when we publish new security blog posts!
Try it now

Research
/Security News
Malicious npm packages use Adspect cloaking and fake CAPTCHAs to fingerprint visitors and redirect victims to crypto-themed scam sites.

Security News
Recent coverage mislabels the latest TEA protocol spam as a worm. Here’s what’s actually happening.

Security News
PyPI adds Trusted Publishing support for GitLab Self-Managed as adoption reaches 25% of uploads