
Research
/Security News
npm Malware Campaign Uses Adspect Cloaking to Deliver Malicious Redirects
Malicious npm packages use Adspect cloaking and fake CAPTCHAs to fingerprint visitors and redirect victims to crypto-themed scam sites.


Sarah Gooding
November 8, 2025
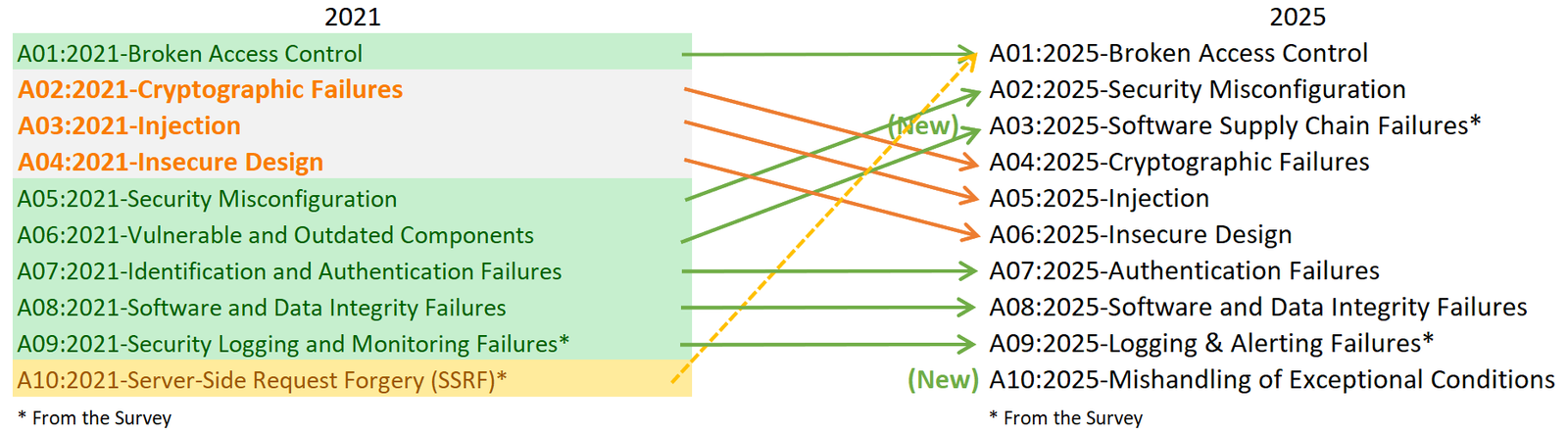
For the first time, Software Supply Chain Failures has its own dedicated category in the OWASP Top 10. It expands on the earlier 'Vulnerable and Outdated Components' category to reflect how supply chain attacks now reach beyond outdated dependencies into the tools and infrastructure that build and deliver software.
Published as a release candidate on November 6, the OWASP Top 10 is a benchmark list of the most critical web application security risks, updated periodically based on industry data and community input. The 2025 edition expands its focus to include compromises in dependencies, build systems, IDEs, and CI/CD pipelines, the infrastructure developers rely on to produce and ship software.
A few of the highlights from this year's report:
Security Misconfiguration moved from fifth position in 2021 to second place in 2025, with 3% of tested applications showing one or more of the 16 related CWEs. Broken Access Control remains at number one, with 3.73% of applications tested showing one or more of the 40 CWEs in the category.
Earlier OWASP lists treated vulnerable components as a subset of traditional security bugs where “update your libraries” was the standard advice. The 2025 version acknowledges that this framing no longer fits reality.
OWASP cited a myriad of example attack scenarios that fall under the new category Software Supply Chain Failures:
According to the 2025 report, OWASP continues to group multiple Common Weakness Enumerations (CWEs) under broader categories rather than listing individual CWEs, as MITRE’s Top 25 Most Dangerous Software Weaknesses does. The 2025 Top 10 includes 248 CWEs distributed across its ten categories.
The report explains that this approach helps address two challenges. First, not all CWEs apply to every programming language or framework, which would make a single global list of weaknesses less useful for training and automation. Second, many common vulnerability types, such as injection, cross-site scripting, hardcoded passwords, and buffer overflows, are represented by multiple CWEs. Different organizations and testing tools may classify the same issue differently.
By grouping related weaknesses under a single category, OWASP says it aims to raise general awareness of the most significant problem areas while keeping the list relevant across diverse technology stacks.
The OWASP Top 10 uses a hybrid methodology: eight categories come from contributed testing data, while two are promoted based on community survey responses. The organization takes this approach because testing data inherently looks backward and misses emerging threats.
"Application Security researchers dedicate time to identifying new vulnerabilities and developing new testing methods. It takes weeks to years to integrate these tests into tools and processes," the report explains. "By the time we can reliably test a weakness at scale, years may have passed."
Supply chain security exemplifies this testing gap. Despite ranking as the top community concern, supply chain failures appear in only 5.19% of tested applications on average. The category includes just five CWEs with only 11 associated CVEs in the contributed data, the smallest data footprint of any category on the list. However, when vulnerabilities are found, they carry the highest average exploit and impact scores.
The community survey allows practitioners on the front lines to flag risks they're seeing that haven't yet appeared in testing data and may never be fully captured through automated testing alone.
By giving Software Supply Chain Failures a dedicated place in the Top 10, OWASP is acknowledging what many teams have already learned the hard way: the biggest risks today aren’t just in the code you write, but in the code, tools, and infrastructure you depend on.
OWASP’s recommendations for managing supply chain risk focus on maintaining visibility and integrity across the development process: managing a software bill of materials, tracking transitive dependencies, using signed and verified packages, and securing CI/CD systems with strong access controls and separation of duties. Developer workstations and build infrastructure should be monitored and secured with the same rigor as production environments.
The report's “How to Prevent” section goes further, advising teams to “treat components in your CI/CD pipeline as part of this process; harden them, monitor them, and document changes accordingly.” That guidance marks a clear cultural shift in how developers are advised to think about security. The Top 10 now frames dependencies, build pipelines, and even IDEs as part of the threat model rather than as background tools that can be trusted by default.
Subscribe to our newsletter
Get notified when we publish new security blog posts!
Try it now

Research
/Security News
Malicious npm packages use Adspect cloaking and fake CAPTCHAs to fingerprint visitors and redirect victims to crypto-themed scam sites.

Security News
Recent coverage mislabels the latest TEA protocol spam as a worm. Here’s what’s actually happening.

Security News
PyPI adds Trusted Publishing support for GitLab Self-Managed as adoption reaches 25% of uploads