
Security News
GitHub Actions Pricing Whiplash: Self-Hosted Actions Billing Change Postponed
GitHub postponed a new billing model for self-hosted Actions after developer pushback, but moved forward with hosted runner price cuts on January 1.


Sarah Gooding
April 1, 2025
Python has officially standardized a lock file format.
PEP 751 introduces pylock.toml, a TOML-based format that records exact dependency versions, file hashes, and installation sources. This is a major step forward for achieving reliable, reproducible Python environments, especially in deployment and CI settings.
The PEP was accepted on March 31, 2025. It brings Python in line with ecosystems like JavaScript (package-lock.json), Rust (Cargo.lock), and Go (go.sum), which already rely on standardized lock files.
Until now, Python had no standard way to lock dependency versions and sources across environments. Projects relied on tools like pip freeze, Poetry, PDM, pip-tools, or uv, each with their own lock file format, leading to:
PEP 751 aims to unify the ecosystem around a single format: pylock.toml.
The new lock file format is designed to be machine-generated but human-readable. It records everything an installer needs to perform a reproducible install, including:
The format also eliminates the need for dependency resolution during installation, allowing for faster and more predictable installs.
The Python community already had a de facto lock file in requirements.txt, widely used and supported by tools like pip, pip-tools, and Poetry. But it was never formally standardized, which was part of the problem.
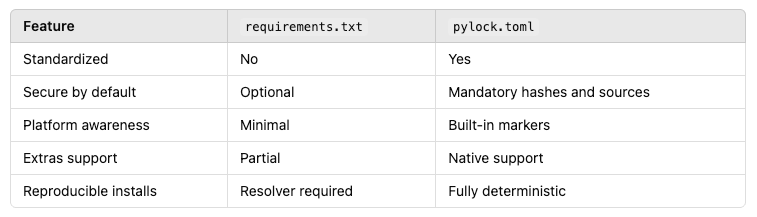
The proposal explains that they opted not to standardize on requirements.txt because the format was designed specifically for pip’s needs, making it inflexible and hard to extend. It lacks a formal specification, relies on conventions, and doesn’t support features like dependency groups or platform-specific logic in a structured way. Most critically, it isn’t secure by default: file hashes are optional, and pip doesn’t restrict installs to what's listed unless explicitly told to do so.
In contrast, pylock.toml is designed from the ground up to be auditable, reproducible, and tool-agnostic—with security and multi-environment support baked in.
Under this new system, tools fall into two categories:
Because the format is standardized and self-contained, installers don’t need to perform any resolution. They simply install what the lock file specifies. That also means cloud platforms or security scanners can more easily support Python environments without needing to interpret half a dozen formats.
The PEP allows for both single-use and multi-use lock files, supporting complex setups like monorepos and conditional dependencies via extras and dependency groups.
PEP 751 adopts a security-first stance by requiring:
While the PEP doesn't address all supply chain threats (such as typosquatting, maintainer account compromise, and concealed payloads), it lays the groundwork for better auditing and tamper resistance.
While requirements.txt remains useful, especially for specifying install-time options like --index-url—it lacks many of the guarantees that pylock.toml offers. Here’s how they compare:
PEP 751 is a big step toward modern, secure, and reliable Python packaging. Its adoption promises better reproducibility and auditability, especially in cloud and CI environments. In 2025, we could potentially see support for pylock.toml become a key differentiator for packaging tools, marking a turning point in the effort to end lock file fragmentation across the Python ecosystem.
Subscribe to our newsletter
Get notified when we publish new security blog posts!
Try it now

Security News
GitHub postponed a new billing model for self-hosted Actions after developer pushback, but moved forward with hosted runner price cuts on January 1.

Security News
Socket CTO Ahmad Nassri shares practical AI coding techniques, tools, and team workflows, plus what still feels noisy and why shipping remains human-led.

Research
/Security News
A five-month operation turned 27 npm packages into durable hosting for browser-run lures that mimic document-sharing portals and Microsoft sign-in, targeting 25 organizations across manufacturing, industrial automation, plastics, and healthcare for credential theft.