
Security News
OWASP 2025 Top 10 Adds Software Supply Chain Failures, Ranked Top Community Concern
OWASP’s 2025 Top 10 introduces Software Supply Chain Failures as a new category, reflecting rising concern over dependency and build system risks.


Sarah Gooding
October 29, 2024
In a significant blow to the cybercriminal infostealer business, the Dutch National Police have successfully disrupted two prominent malware-as-a-service (MaaS) operations known as Redline and Meta. In a takedown, dubbed Operation Magnus, international law enforcement compromised their backend infrastructure and source code. The seized data is being reviewed as part of an ongoing investigation.
Redline and Meta, infamous for their information-stealing operations, have been plaguing internet users for years. At Socket, we encounter a steady stream of infostealer malware in our threat feed, and frequently see open source packages used as the attack vector for sensitive data exfiltration. It’s a lucrative activity, allowing attackers to exploit the stolen data for their own malicious activities, sell credentials to other cybercriminals, or initiate larger-scale attacks such as ransomware operations.
The Dutch National Police’s PR is on point, taunting the underworld with a takedown video presented as a "final update" for Redline and Meta users, mimicking a software update announcement. It warns of impending consequences and redefines “VIP” as “Very Important to Police.”
Law enforcement gained access to all Redline and Meta servers, usernames, passwords, IP addresses, timestamps, registration date, and more. They also took possession of all their source code, including the license servers, REST API servers, panels, stealers, and Telegram bots.
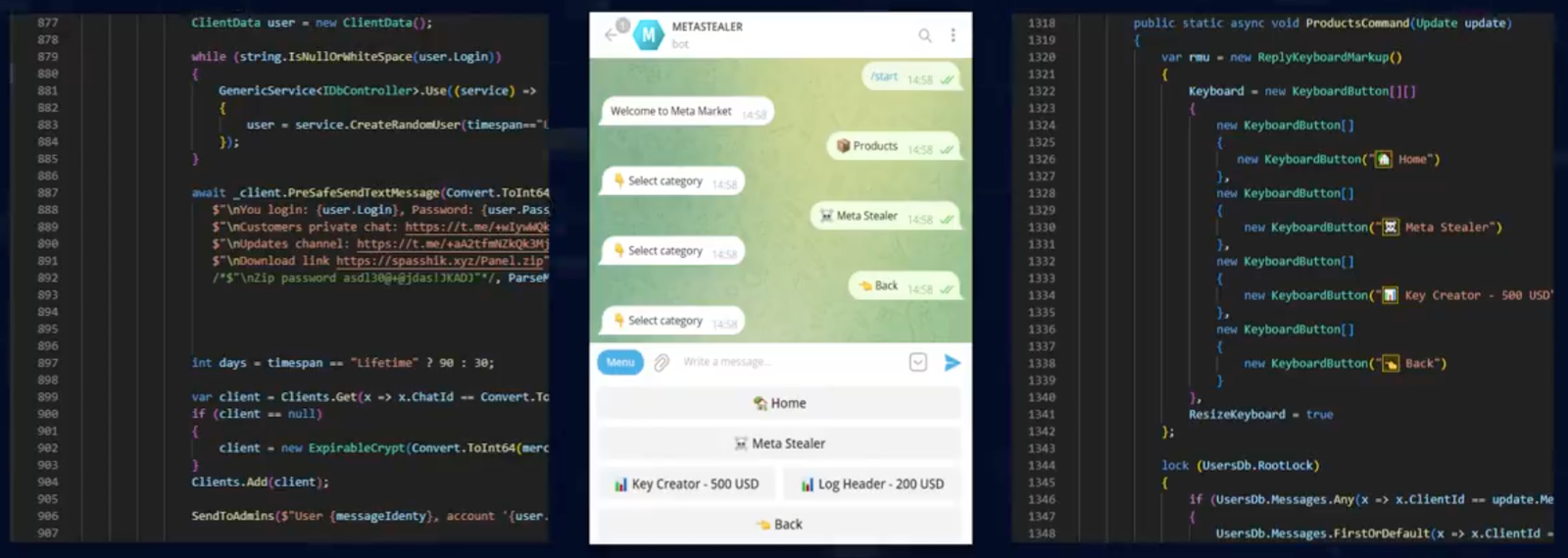
Redline and Meta malware strains targeted both Windows and macOS systems, pilfering sensitive data including login credentials, credit card information, and cryptocurrency wallet details.
Operating on a subscription-based model, Redline and Meta offered cybercriminals easy access to sophisticated malware tools for as little as $125 per month. This low barrier to entry contributed to their widespread use and longevity in the cybercrime ecosystem.
The malware-as-a-service (MaaS) model for Redline and Meta operates similarly to legitimate software-as-a-service businesses, but with malicious intent. Cybercriminals can purchase access to Redline and Meta on a subscription basis:
The Dutch police's operation revealed that both malware operations shared significant infrastructure, a factor that may have contributed to their ability to evade detection. Their distribution methods, including phishing emails and compromised websites, further complicated efforts to trace and neutralize the threats. This allowed Redline and Meta to operate effectively for several years before law enforcement agencies were able to disrupt their operations.
The Dutch National Police created a new website for tracking and sharing the details of the operation: http://operation-magnus.com. A countdown on the website indicates that more information will be released tomorrow.
Subscribe to our newsletter
Get notified when we publish new security blog posts!
Try it now

Security News
OWASP’s 2025 Top 10 introduces Software Supply Chain Failures as a new category, reflecting rising concern over dependency and build system risks.

Research
/Security News
Socket researchers discovered nine malicious NuGet packages that use time-delayed payloads to crash applications and corrupt industrial control systems.

Security News
Socket CTO Ahmad Nassri discusses why supply chain attacks now target developer machines and what AI means for the future of enterprise security.