
Security News
OWASP 2025 Top 10 Adds Software Supply Chain Failures, Ranked Top Community Concern
OWASP’s 2025 Top 10 introduces Software Supply Chain Failures as a new category, reflecting rising concern over dependency and build system risks.


Sarah Gooding
May 21, 2024
The Securities and Exchange Commission (SEC) has adopted new rule amendments to Regulation S-P, which will require covered institutions to report incidents involving unauthorized access to or use of customer information within 30 days. Financial institutions are the focus of this update to disclosure requirements:
The amendments update the rules’ requirements for broker-dealers (including funding portals), investment companies, registered investment advisers, and transfer agents (collectively, “covered institutions”) to address the expanded use of technology and corresponding risks that have emerged since the Commission originally adopted Regulation S-P in 2000.
The amendments were updated in the interest of protecting consumer data, so that those who are affected can respond in a timely way. It requires institutions to include details about the incident, the breached data, and how affected individuals can respond to protect themselves.
The new rules will take effect 60 days after publication in the Federal Register. Larger entities have 18 months to comply and smaller entities have 24 months.
The 30-day disclosure requirement for financial institutions has gained adoption just as the SEC’s new disclosure requirements for publicly traded companies are landing into enforcement. These requirements mandate even stricter incident reporting, including the following:
CISA has also recently proposed a new mandate that would require critical infrastructure to report ransom payments within 24 hours. The growing number of required disclosures has become somewhat controversial. In addition to the operational challenges of meeting reporting requirements for various federal agencies, some contend that the tight timeline on disclosures exposes victimized companies to further attacks before incidents can be fully remediated.
Despite the U.S. federal government’s many attempts to mandate faster incident reporting, cyber incidents frequently go unreported. In a recent research report that surveyed 170 cybersecurity professionals in the US, the UK, and Ireland, cybersecurity and compliance company VikingCloud found that 40% of cyber teams have intentionally not reported cyber incidents because they were worried about losing their jobs.
Although 96% of surveyed professionals were confident in their ability to detect and respond to cyberattacks in real time, they also report being unprepared for specific types of attacks:
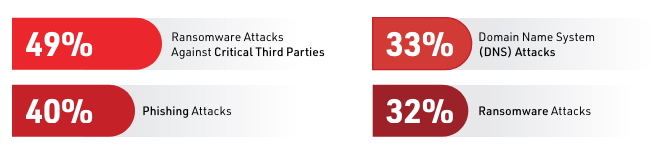
Only 5% have allocated additional budget to their cyber programs in the past 12 months, due to talent and budget shortages. At the same time, 49% of respondents reported that their companies saw cyberattacks increase in frequency and 43% said they increased in severity over the past 12 months. VikingCloud highlighted these findings, stating the research “uncovers an alarming disconnect between perceived and actual cybersecurity readiness.”
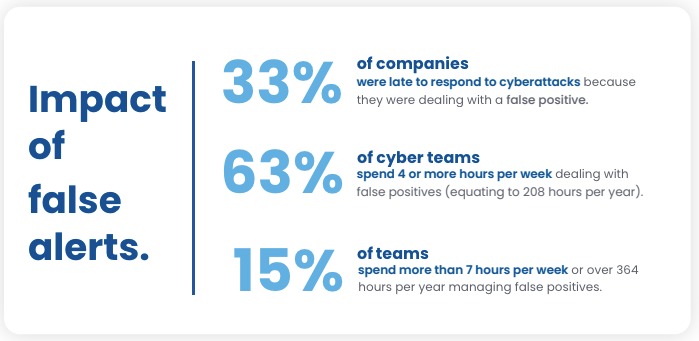
In terms of meeting reporting requirements, 68% of cyber teams surveyed said they would not be able to meet the SEC’s new 4-day disclosure rule. Roughly 1 in 3 companies reported being late to respond to cyberattacks because they were dealing with a false positive.
Despite being overly confident in their ability to detect and respond to cyberattacks, 55% of companies said modern cyber criminals are more advanced than their internal teams. Ransomware attacks are the category companies report they are least prepared for, with only 17% having taken steps in the past 12 months to secure their supply chain.
Alert fatigue and lack of resources are a few of the most critical factors in companies being unprepared to respond to modern cyber attacks and less likely to report them. Even major companies are finding it difficult to comply with the SEC’s new 4-day reporting requirement. The first reports from Microsoft, Hewlett Packard, UnitedHealth Group, Prudential Financial, VF Corp, and Loan Depot, have not explicitly met the incident disclosure requirements, as they leave out the material impacts or reasonably likely material impacts of the incidents.
The stark contrast between mandated incident reporting and the reality of unreported cyber incidents indicates that many organizations may be having a rocky transition into the latest disclosure requirements. The federal push to enforce transparency may not elicit the intended response in the face of fear of job loss among cyber professionals.
Inadequate security resource allocation has created a gap between perceived readiness and actual preparedness. This gap is further widened by the reluctance to report incidents, which can delay necessary responses and recovery efforts, ultimately exacerbating the impact of cyberattacks.
Subscribe to our newsletter
Get notified when we publish new security blog posts!
Try it now

Security News
OWASP’s 2025 Top 10 introduces Software Supply Chain Failures as a new category, reflecting rising concern over dependency and build system risks.

Research
/Security News
Socket researchers discovered nine malicious NuGet packages that use time-delayed payloads to crash applications and corrupt industrial control systems.

Security News
Socket CTO Ahmad Nassri discusses why supply chain attacks now target developer machines and what AI means for the future of enterprise security.