
Security News
Another Round of TEA Protocol Spam Floods npm, But It’s Not a Worm
Recent coverage mislabels the latest TEA protocol spam as a worm. Here’s what’s actually happening.
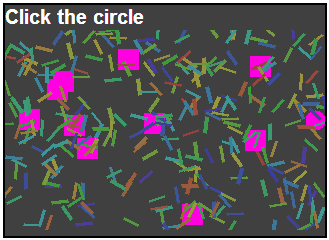
Click CAPTCHA is a concept PHP implementation of a visual CAPTCHA which requires a single mouse click to authenticate that the user is human. The user must select a circle in a raster image hidden among dashes and like-colored distractors.
The CAPTCHA generates a 320x200 PNG image using PHP. It is a grid of 10x16 cells, in which one is filled with a circle of random hue. A click attempt is sent via AJAX to the server using POST, and compared to the hashed answer. The hash is sent to the page, but it is salted such that an attack could not just try 10x16 positions against the hash. The chance that an informed attacker selects the correct cell at random is 1 / 10x16 = 0.625 percent. The distracting squares and dashes make image processing approach difficult.
Example generated image. The target circle is on the far right, middle:
FAQs
Unknown package
Did you know?

Socket for GitHub automatically highlights issues in each pull request and monitors the health of all your open source dependencies. Discover the contents of your packages and block harmful activity before you install or update your dependencies.

Security News
Recent coverage mislabels the latest TEA protocol spam as a worm. Here’s what’s actually happening.

Security News
PyPI adds Trusted Publishing support for GitLab Self-Managed as adoption reaches 25% of uploads

Research
/Security News
A malicious Chrome extension posing as an Ethereum wallet steals seed phrases by encoding them into Sui transactions, enabling full wallet takeover.