
Security Fundamentals
Turtles, Clams, and Cyber Threat Actors: Shell Usage
The Socket Threat Research Team uncovers how threat actors weaponize shell techniques across npm, PyPI, and Go ecosystems to maintain persistence and exfiltrate data.
github.com/shauryaag/tcms-go
Note: Its still a work-in-progress, however the proof of concept is ready.
A test case management tool written in Go. Following all the SOLID properties.
This project is built in a way that anything can be plugged in, and replaced with something else.
The current database used is MongoDB, but can easily be replaced with any other database, even with a relational database.
As an example, we have used Chi as the router, but it can be replaced with Gorilla Mux easily (or any other router as one wishes).
Why would anyone need to replace their router with something else?
Since the whole project is built in a way that any part of it can be replaced with something else, it is very easy to change the router, this is because the whole project is based on abstractions. Even the subrouter can be replaced with something else, that is, you can have multiple routers in the same project.
The point is not to have multiple routers in the same project, but combining multiple projects built using different frameworks into one at will, think of the whole project as a modular monolith.

Any number of services can be added or removed easily, and multiple microservices could be turned into a monolith. This can often save costs and runtime.
FAQs
Unknown package
Did you know?

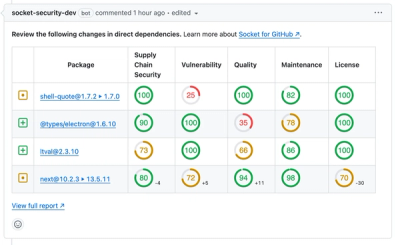
Socket for GitHub automatically highlights issues in each pull request and monitors the health of all your open source dependencies. Discover the contents of your packages and block harmful activity before you install or update your dependencies.

Security Fundamentals
The Socket Threat Research Team uncovers how threat actors weaponize shell techniques across npm, PyPI, and Go ecosystems to maintain persistence and exfiltrate data.

Security News
At VulnCon 2025, NIST scrapped its NVD consortium plans, admitted it can't keep up with CVEs, and outlined automation efforts amid a mounting backlog.
Product
We redesigned our GitHub PR comments to deliver clear, actionable security insights without adding noise to your workflow.