
Security Fundamentals
Turtles, Clams, and Cyber Threat Actors: Shell Usage
The Socket Threat Research Team uncovers how threat actors weaponize shell techniques across npm, PyPI, and Go ecosystems to maintain persistence and exfiltrate data.
github.com/thomaslanghorst/mock-generator
This is a small project I wrote to help create mock files using golangs template package. It will generate mock files that would be written using the mock package of testify.
To build the mock-generator you simply have to build the binary using
go build -o ./bin/mock-generator
If you want to make it gobally available, just export the path to your ~/.bashrc file.
export PATH=$PATH:</path/to/your/project>/bin/mock-generator
After you have build the binary you can call and test it using the ./example/service.go file.
./bin/mock-generator -i ./example/service.go
This will generate a file called service_mock.go next to the service.go file.
If you take this simple example
package service
type User struct {
}
type ServiceInterface interface {
Login(userId string, password string) error
ListUsers() ([]User, error)
Logout(userId string)
}
and run the mock-generator. The output file will look like this:
package service
import "github.com/stretchr/testify/mock"
type MockServiceInterface struct {
mock.Mock
}
func (m *MockServiceInterface) Login(userId string, password string) error {
args := m.Called(userId, password)
return args.Error(0)
}
func (m *MockServiceInterface) ListUsers() ([]User, error) {
args := m.Called()
var v0 []User
if args.Get(0) != nil {
v0 = args.Get(0).([]User)
}
return v0, args.Error(1)
}
func (m *MockServiceInterface) Logout(userId string) {
m.Called(userId)
}
FAQs
Unknown package
Did you know?

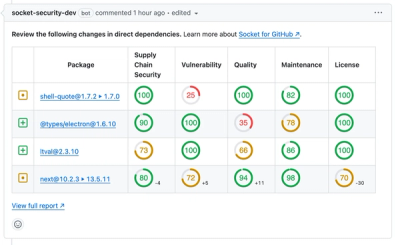
Socket for GitHub automatically highlights issues in each pull request and monitors the health of all your open source dependencies. Discover the contents of your packages and block harmful activity before you install or update your dependencies.

Security Fundamentals
The Socket Threat Research Team uncovers how threat actors weaponize shell techniques across npm, PyPI, and Go ecosystems to maintain persistence and exfiltrate data.

Security News
At VulnCon 2025, NIST scrapped its NVD consortium plans, admitted it can't keep up with CVEs, and outlined automation efforts amid a mounting backlog.
Product
We redesigned our GitHub PR comments to deliver clear, actionable security insights without adding noise to your workflow.