
Security News
curl Shuts Down Bug Bounty Program After Flood of AI Slop Reports
A surge of AI-generated vulnerability reports has pushed open source maintainers to rethink bug bounties and tighten security disclosure processes.
Sunglasses is a proxy server that presents an RFC 6962-compatible view of a static-ct-api log.
The submission endpoints (add-chain, add-pre-chain, and get-roots) are proxied to the log's submission endpoint without translation.
get-entries is converted to a single data tile fetch, and the response is translated to RFC 6962 syntax. To build the response, issuer certificates are retrieved from the log as needed and cached.
get-sth returns the latest checkpoint retrieved from the log, translated to an RFC 6962 STH.
get-sth-consistency and get-entry-and-proof fetch the necessary tiles from the log to build a proof.
get-proof-by-hash is the most complicated endpoint to implement, since it requires determining the position of the leaf specified by the client. Sunglasses continuously downloads leaf tiles from the log to build an index from leaf hash to leaf position. get-proof-by-hash looks up the hash in the index, and then fetches the necessary tiles from the log to build a proof.
The leaf index, issuer cache, and latest STH are stored in a SQLite database.
Note that get-sth only returns trees which have been fully indexed, and get-entries only returns entries within the tree returned by get-sth. Consequentially, standing up a proxy for a large log takes a long time because all existing leaves have to be downloaded and indexed before the proxy is usable. Once all leaves have been indexed, Sunglasses should have no problem keeping up with the growth of the log.
These are for testing purposes only and should not be used in production.
https://itko-2025.sunglasses.sslmate.net/https://rome-2024h2.sunglasses.sslmate.net/https://rome-2025h1.sunglasses.sslmate.net/https://rome-2025h2.sunglasses.sslmate.net/go install src.agwa.name/sunglasses@latest
-db PATHPath to database file, which will be created if necessary. If omitted, leaf indexing and issuer caching will be disabled.
-id BASE64 (Mandatory)Log ID, in base64.
-listen SOCKETListen on the given address, provided in go-listener syntax. You can specify the -listen flag multiple times to listen on multiple addresses.
-monitoring URL (Mandatory)URL prefix of the log's monitoring endpoint.
-submission URL (Mandatory)URL prefix of the log's submission endpoint.
-no-leaf-indexDisable leaf indexing. This considerably reduces the size of the database and allows you to stand up a proxy without waiting for the log to be indexed, but it means that the get-proof-by-hash endpoint won't work.
-unsafe-nofsyncDangerously disable fsync when writing to the database. This is useful for speeding up the initial indexing, but if your system shuts down uncleanly you may experience database corruption, requiring you to reindex the log from scratch. You should not use this flag once initial indexing is complete and the proxy is running in production.
The following command will launch an RFC 6962-compatible log at https://itko-2025.sunglasses.example.com which proxies requests to the Itko 2025 log.
sunglasses -id yLkilxtwEtRI1qd7fACK5qViNNxRkxAzwlUNQjiVeZo= -db /srv/sunglasses/itko-2025.db -listen tls:itko-2025.sunglasses.example.com:tcp:443 -monitoring https://ct2025.itko.dev -submission https://ct2025.itko.dev
FAQs
Unknown package
Did you know?

Socket for GitHub automatically highlights issues in each pull request and monitors the health of all your open source dependencies. Discover the contents of your packages and block harmful activity before you install or update your dependencies.

Security News
A surge of AI-generated vulnerability reports has pushed open source maintainers to rethink bug bounties and tighten security disclosure processes.
Product
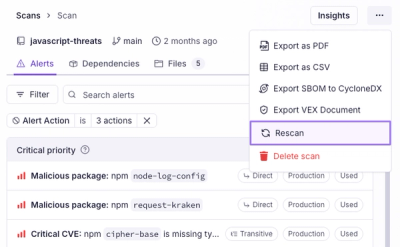
Scan results now load faster and remain consistent over time, with stable URLs and on-demand rescans for fresh security data.
Product
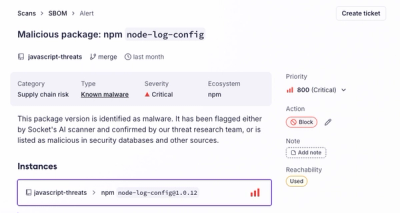
Socket's new Alert Details page is designed to surface more context, with a clearer layout, reachability dependency chains, and structured review.