Obfuscated code
Severity
High
Short Description
Obfuscated files are intentionally packed to hide their behavior. This could be a sign of malware.
Suggestion
Packages should not obfuscate their code. Consider not using packages with obfuscated code.
Information
Consuming this package may involve risks due to its hidden or unclear functionality. Review and evaluate the necessity of including such code in your project.
Obfuscated code refers to programming that has been deliberately made difficult to understand. Developers may use obfuscation for various legitimate reasons, such as protecting intellectual property or preventing reverse engineering. However, in the context of security, obfuscated code is often used to conceal malicious activities and evade detection by security tools.
Risks of Obfuscated Code:
- Malware Concealment: Obfuscation can hide malicious payloads, making it challenging to identify and mitigate threats.
- Unintended Behavior: Hidden code can introduce bugs or unexpected behaviors in your software, affecting its reliability and security.
- Compliance Issues: Using obfuscated code might conflict with industry standards and compliance requirements, which often demand transparency in codebases.
Because of the potential threats posed by obfuscated code, Socket’s AI-powered threat detection flags these packages as high severity risks:
- Code Complexity: Obfuscated code adds unnecessary complexity, making it difficult to maintain and audit.
- Security Risks: Hidden malicious code can execute unauthorized actions, such as data exfiltration, privilege escalation, or installing backdoors.
Recommended actions
Investigate the Dependency:
- Verify the Legitimacy: Check the official repository, issue trackers, and recent changes to understand why the code is obfuscated.
- Evaluate the Necessity: Assess whether the obfuscated code is essential for your project or if an alternative exists.
- Conduct a Security Review: Perform a thorough security review to ensure that the obfuscated code does not introduce vulnerabilities or malicious behaviors.
Replace the Dependency:
- Find an Alternative Library: Search for other libraries that provide similar functionality but have a more transparent codebase.
- Fork and Maintain: If no suitable alternatives exist, consider forking the original repository and maintaining your own version without obfuscation. This ensures that you retain control over the dependency.
Monitor the Dependency:
- Regular Scans: Keep the dependency under regular security scans to detect any changes or updates that might introduce obfuscation again.
- Community Feedback: Engage with the developer community to stay informed about any reported issues or vulnerabilities related to the obfuscated code.
Examples
Examples
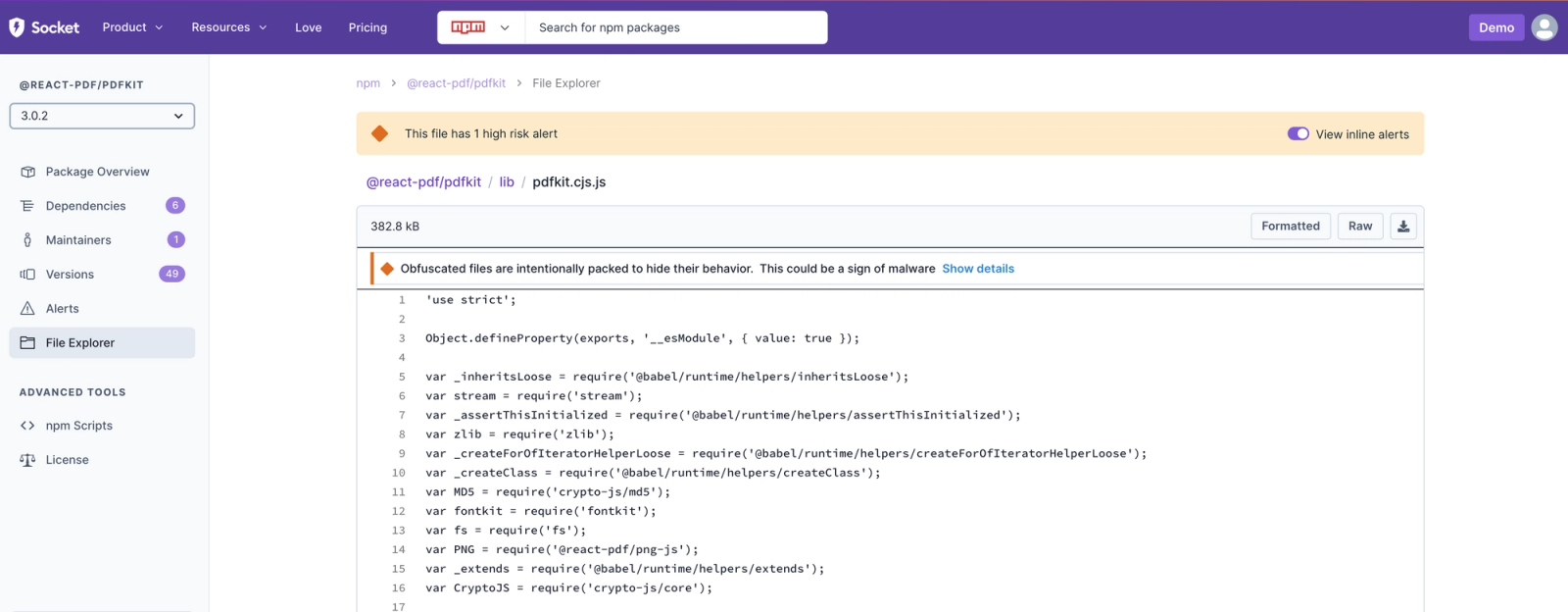
Example 1: @react-pdf/pdfkit
- File: pdfkit.cjs.js
- Description: The
@react-pdf/pdfkitpackage contains obfuscated code within thepdfkit.cjs.jsfile. This obfuscation makes it challenging to understand the actual behavior of the code, raising concerns about potential hidden malicious activities.
Example 2: Coverage
- File: test_context.py
- Description: The
coveragepackage includes obfuscated code in thetest_context.pyfile. This obfuscation obscures the code's functionality, making it difficult to assess its impact on the overall security of the project.
Example 3: Crypto-mining Malware
- In 2018, several npm packages were found to contain obfuscated code that executed crypto-mining scripts on users' machines without their consent.
Example 4: Adware and Spyware
- Obfuscated adware and spyware have been discovered in various open-source libraries, performing unauthorized data collection and tracking.
Detection Method
For Python
Socket detects files obfuscated via the PyArmor tool using a regular expression. PyArmor is a tool used to obfuscate Python scripts, bind obfuscated scripts to fixed machines, or expire obfuscated scripts. For more information, visit PyArmor.
For JavaScript
Socket uses a custom algorithm to detect code obfuscation and minification. This algorithm analyzes various aspects of code structure and syntax, including:
- Line Lengths: Extremely long lines can indicate minified code.
- Whitespace Usage: Minified code often lacks regular whitespace.
- Identifier Patterns: Unusually short or non-descriptive variable names.
- Constant Usage: Excessive use of constants.
- String Manipulation: Complex string operations that obscure code intent.
In addition, Socket leverages AI to flag files as obfuscated, further enhancing its detection capabilities.
Additional resources
Effectively managing obfuscated code in your projects is crucial for maintaining security and transparency. By leveraging Socket’s alert system, you can identify and address potential threats posed by obfuscated code, ensuring a secure development environment. For more detailed guidance, visit the Socket Documentation.
Additional Information:
- What is JavaScript Obfuscation and Why Should You Care?: Guardsquare Blog
- Catch Me If You Can: JavaScript Obfuscation: Akamai Blog
- The Power of Code Obfuscation: Verimatrix
- Code Obfuscation Techniques: ASEE Cybersecurity
- Analysis of SolarWinds Hack: eCloudControl