
Security News
curl Shuts Down Bug Bounty Program After Flood of AI Slop Reports
A surge of AI-generated vulnerability reports has pushed open source maintainers to rethink bug bounties and tighten security disclosure processes.
keet-identity-key
Advanced tools
Hierarchical keychains that derives deterministic Ed25519 keypairs
npm install keet-identity-key
const IdentityKey = require('keet-identity-key')
const mnemonic = IdentityKey.generateMnemonic()
const id = await IdentityKey.from({ mnemonic })
const proof0 = id.bootstrap(mainDevice.publicKey)
const proof = IdentityKey.attest(auxillaryDevice.publicKey, mainDevice, proof0)
const info = IdentityKey.verify(proof)
if (info === null) {
// verification failed
} else {
console.log(b4a.equals(info.identityPublicKey, id.identityPublicKey)) // true
console.log(b4a.equals(info.publicKey, auxillaryDevice.publicKey)) // true
}
mnemonic = IdentityKey.generateMnemonic()Generate a new mnemonic
seed = IdentityKey.generateSeed(mnemonic)Returns a 32-byte buffer with entropy derived from mnemonic
const identity = new IdentityKeyPair(keyChain)Instantiate a new IdentityKey
identity.identityPublicKey32-byte public key for the root identity
identity.profileDiscoveryKeyPairKey pair to be used for the profile discovery core
identity.profileDiscoveryPublicKey32-byte public key for the profile discovery core
identity.profileDiscoveryKeyPairKey pair to be used for the profile discovery core
const encryptionKey = identity.getProfileDiscoveryEncryptionKey()Encryption key to be used for the profile discovery core
const encryptionKey = identity.getEncryptionKey(profileKey)Derive an encrypton key for a given profile
identity.clear()Clear all private data from the key
identity = IdentityKey.from({ mnemonic, seed })Convenience method for deriving an IdentityKey from a mnemonic or seed
proof = identity.bootstrap(deviceKey)Bootstrap an intitial deviceKey
proof = IdentityKey.bootstrap({ seed, mnemonic }, deviceKey)Bootstrap an intitial deviceKey using a mnemonic
proof = IdentityKey.attestDevice(device, parent, [proof])Use an existing parent key pair to attest to another device key.
If provided with a proof linking parent to a given root key, then the returned proof will link key back to the same root key.
proof = IdentityKey.attestData(data, keyPair, [proof])Create an attestation of arbitrary data using keyPair.
If a proof is provided, the attestation will be appended to the proof and verified as part of it.
keyPair should correspond to the last public key in the proof's chain.
info = IdentityKey.verify(proof, attestedData, opts ={ receipt, expectedIndentity, expectedDevice })Verify a proof.
Returns null if verification fails, otherwise an object with:
receipt: an opaque object that future proofs may be verified againstidentityPublicKey: the root public key the proof links todevicePublicKey: the public key the proof attests toIf no data is attested to, ie. we are just verifying a device key, then attestedData should be passed as null.
Optionally pass any of receipt, expectedIndentity or expectedDevice. Verification will fail if:
receiptexpectedIndentity providedexpectedDevice providedApache-2.0
FAQs
Hierarchical Deterministic Keys for Keet Identities
The npm package keet-identity-key receives a total of 797 weekly downloads. As such, keet-identity-key popularity was classified as not popular.
We found that keet-identity-key demonstrated a healthy version release cadence and project activity because the last version was released less than a year ago. It has 1 open source maintainer collaborating on the project.
Did you know?

Socket for GitHub automatically highlights issues in each pull request and monitors the health of all your open source dependencies. Discover the contents of your packages and block harmful activity before you install or update your dependencies.

Security News
A surge of AI-generated vulnerability reports has pushed open source maintainers to rethink bug bounties and tighten security disclosure processes.
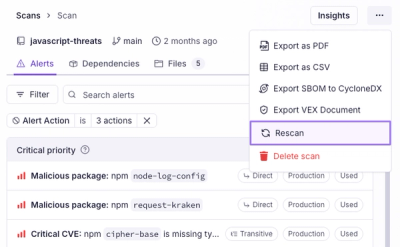
Product
Scan results now load faster and remain consistent over time, with stable URLs and on-demand rescans for fresh security data.
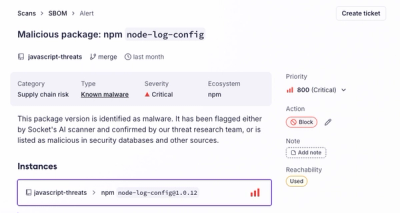
Product
Socket's new Alert Details page is designed to surface more context, with a clearer layout, reachability dependency chains, and structured review.