
Research
/Security News
9 Malicious NuGet Packages Deliver Time-Delayed Destructive Payloads
Socket researchers discovered nine malicious NuGet packages that use time-delayed payloads to crash applications and corrupt industrial control systems.
path-intersection
Advanced tools
Computes the intersection between two SVG paths.
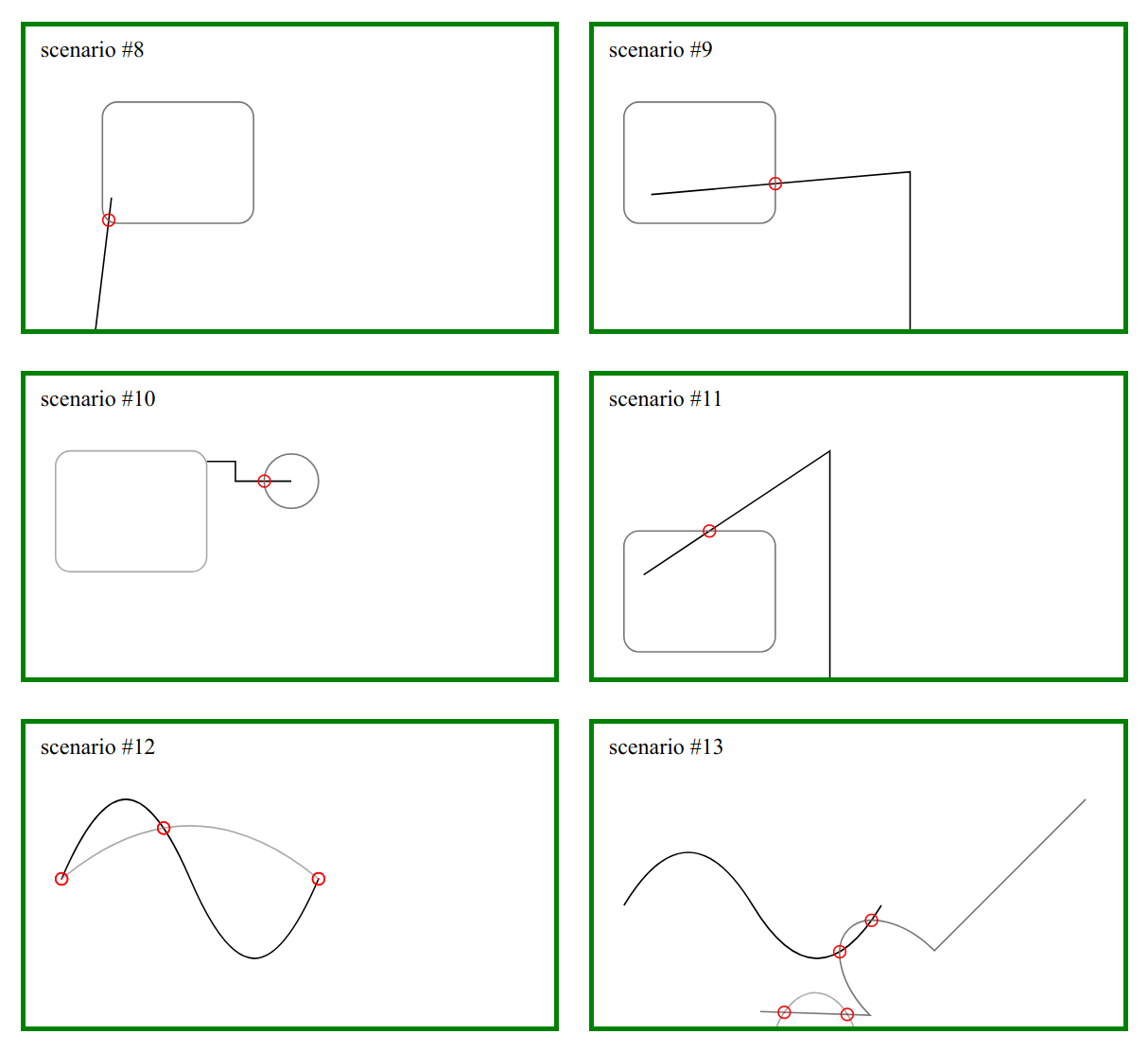
Execute npm run dev and navigate to http://localhost:9876/debug.html to see more examples.
import intersect from 'path-intersection';
const path0 = 'M30,100L270,20';
const path1 = 'M150,150m0,-18a18,18,0,1,1,0,36a18,18,0,1,1,0,-36z';
const intersection = intersect(path0, path1);
// [ { x: ..., y: ..., segment1: ..., segment2: ... }, ... ]
Results are approximate, as we use bezier clipping to find intersections.
# install dependencies
npm install
# build and test the library
npm run all
The intersection logic provided by this library is derived from path.js, a part of Snap.svg.
Use under the terms of the MIT license.
3.1.0
FIX: correct type declaration (#23)CHORE: add exports fieldFAQs
Computes the intersection between two SVG paths
The npm package path-intersection receives a total of 151,486 weekly downloads. As such, path-intersection popularity was classified as popular.
We found that path-intersection demonstrated a not healthy version release cadence and project activity because the last version was released a year ago. It has 8 open source maintainers collaborating on the project.
Did you know?

Socket for GitHub automatically highlights issues in each pull request and monitors the health of all your open source dependencies. Discover the contents of your packages and block harmful activity before you install or update your dependencies.

Research
/Security News
Socket researchers discovered nine malicious NuGet packages that use time-delayed payloads to crash applications and corrupt industrial control systems.

Security News
Socket CTO Ahmad Nassri discusses why supply chain attacks now target developer machines and what AI means for the future of enterprise security.

Security News
Learn the essential steps every developer should take to stay secure on npm and reduce exposure to supply chain attacks.