
Security News
npm Adopts OIDC for Trusted Publishing in CI/CD Workflows
npm now supports Trusted Publishing with OIDC, enabling secure package publishing directly from CI/CD workflows without relying on long-lived tokens.
This is a C# library designed for effectively handling tree structures. Emphasizing flexibility and extensibility, the library allows easy manipulation of various tree structures. Features: A rich set of extension methods for `ITreeNode<TNode>` Mutual referencing between parent and child nodes A collection of tree-structured classes with high extensibility Conversion between different data structures and tree structures Generic utility classes needed for implementing the above features
This is a C# library designed to effectively handle tree structures.
The library focuses on flexibility and extensibility, making it easy to manipulate various tree structures.
Key features:
ITreeNode<TNode>Refer to the wiki
This library is not intended to be a complete solution on its own.
It aims to provide tree structure functionality while maintaining compatibility with other libraries.
Below is a detailed explanation of the key features.
Over 60 extension methods are defined for ITreeNode<TNode>, including overloads.
For example:
Enumeration: PreOrder, LevelOrder, all traversal methods, Leafs, Ancestors, DescendArrivals, DescendTraces, etc.
Navigation: Root, NextSibling, LastSibling, etc.
Editing: TryAddChild, Try○○Child, Disassemble, RemoveAllDescendant, etc.
Retrieving parameters: TreeIndex, NodePath, Height, Depth, etc.
Validation methods: IsDescendantOf, IsAncestorOf, IsRoot, etc.
Conversion: ToNodeMap, ToSerializableNodeMap, ToTreeDiagram, Convert, AsValuedTreeNode
Tree construction: AssembleTree, AssembleAsNAryTree, AssembleForestByPath
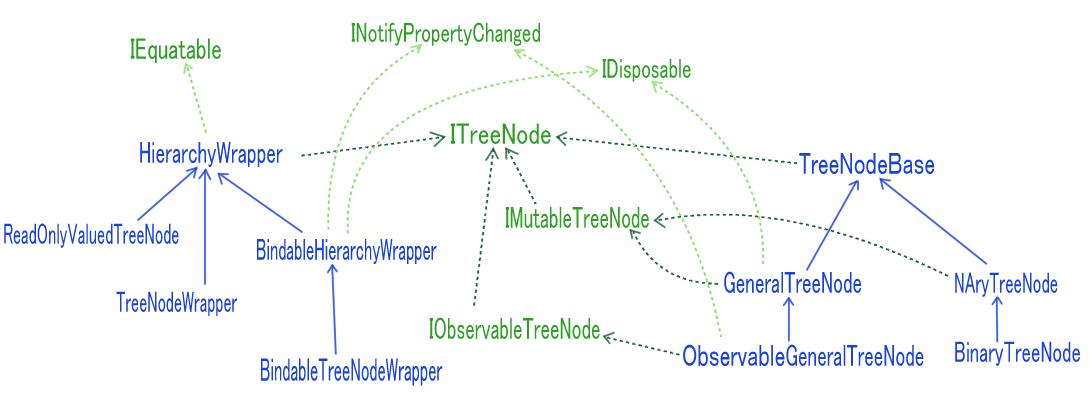
Mutual references between parent and child nodes are handled in the base classes (TreeNodeBase or HierarchyWrapper).
In TreeNodeBase derivatives, behavior can be customized by overriding protected virtual methods such as RemoveChildProcess and InsertChildProcess.
Depending on the use case, the following classes can be inherited and used:
TreeNodeBase:
When fine-tuning method definitions is necessary
GeneralTreeNode / ObservableTreeNode:
For use as a data structure or container
NAryTreeNode:
For an N-ary tree where empty nodes are represented as null
HierarchyWrapper / TreeNodeWrapper:
For wrapping an existing hierarchical structure.
When the child node collection of the wrapped node is modified, the Wrapper.Children property will be refreshed the next time it is accessed.
To reflect changes in the child collection automatically, inherit from Bindable(Hierarchy|TreeNode)Wrapper.
BindableHierarchyWrapper / BindableTreeNodeWrapper:
Automatically receives change notifications from the child node collection of the wrapped node and updates accordingly.
These classes also implement IDisposable, which disposes of the target node and all its descendants.
Intended for scenarios such as MVVM ViewModels, where observability and disposal are required.
In TreeNodeBase and its derivatives, the internal collection used and the collection exposed externally can be customized by overriding Setup(Inner | Public)ChildCollection methods.
For HierarchyWrapper and its derivatives, only the externally exposed collection can be customized.
Even objects that do not implement ITreeNode<TNode> can still utilize the extension methods of ITreeNode<TNode>.
By wrapping them with HierarchyWrapper<TSrc, TWrpr> or BindableHierarchyWrapper<TSrc, TWrpr>, or by calling the AsValuedTreeNode method, you can access the extension methods of ITreeNode<TNode>.
Additionally, several other conversion methods are available, such as the extension methods AssembleTree, AssembleTryByPath, and ToNodeMap.
Some classes used for internal implementation are also exposed.
ListAligner<T,TList>ImitableCollection<TSrc,TDst>ReadOnlyObservableTrackingCollection<T>ObservableCombinableCollection<T>ReadOnlyObservableFilterSortCollection<T>ListScroller<T>UniqueOperationExecutorPropertyChangeProxyINotifyPropertyChanged.ResultWithValue<TValue>, ResultWith<TValue>And more.
Namespaces are categorized by purpose and use case.
Only TreeStructures.Tree is grouped based on implementation rather than purpose, containing classes that form tree structures according to specific rules.
Defines abstract generic tree nodes, related objects, and event arguments.
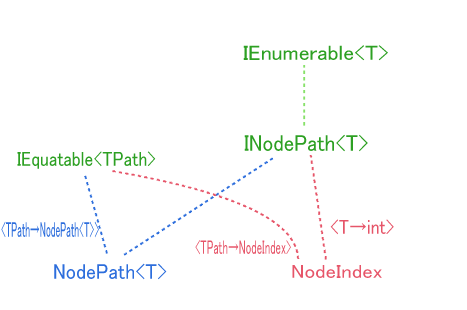
Extension methods for ITreeNode<TNode>, IMutableTreeNode<TNode>, and IEnumerable<T>.
Collections used in internal implementation and extension methods.
Event-related classes that support listener and notification implementation.
Defines ResultWithValue<T> used as the return value for Try○○ methods.
General-purpose classes that do not fit into the above categories.
Dictionaries and other structures used for serialization and deserialization.
Classes used internally in the library but with limited general applicability.
Classes that form tree structures based on specific purposes and use cases.
FAQs
This is a C# library designed for effectively handling tree structures. Emphasizing flexibility and extensibility, the library allows easy manipulation of various tree structures. Features: A rich set of extension methods for `ITreeNode<TNode>` Mutual referencing between parent and child nodes A collection of tree-structured classes with high extensibility Conversion between different data structures and tree structures Generic utility classes needed for implementing the above features
We found that treestructures demonstrated a healthy version release cadence and project activity because the last version was released less than a year ago. It has 1 open source maintainer collaborating on the project.
Did you know?

Socket for GitHub automatically highlights issues in each pull request and monitors the health of all your open source dependencies. Discover the contents of your packages and block harmful activity before you install or update your dependencies.

Security News
npm now supports Trusted Publishing with OIDC, enabling secure package publishing directly from CI/CD workflows without relying on long-lived tokens.

Research
/Security News
A RubyGems malware campaign used 60 malicious packages posing as automation tools to steal credentials from social media and marketing tool users.

Security News
The CNA Scorecard ranks CVE issuers by data completeness, revealing major gaps in patch info and software identifiers across thousands of vulnerabilities.