
Research
Security News
The Growing Risk of Malicious Browser Extensions
Socket researchers uncover how browser extensions in trusted stores are used to hijack sessions, redirect traffic, and manipulate user behavior.
boto3-refresh-session
Advanced tools
A simple Python package for refreshing the temporary security credentials in a boto3.session.Session object automatically.

boto3.session.Session object automatically.
boto3.session.Sessionassume_role configuration, custom STS clients, and profile / region configuration, as well as all other parameters supported by boto3.session.SessionRecognized during AWS Community Day Midwest on June 5th, 2025.
A testimonial from a Cyber Security Engineer at a FAANG company:
Most of my work is on tooling related to AWS security, so I'm pretty choosy about boto3 credentials-adjacent code. I often opt to just write this sort of thing myself so I at least know that I can reason about it. But I found boto3-refresh-session to be very clean and intuitive [...] We're using the RefreshableSession class as part of a client cache construct [...] We're using AWS Lambda to perform lots of operations across several regions in hundreds of accounts, over and over again, all day every day. And it turns out that there's a surprising amount of overhead to creating boto3 clients (mostly deserializing service definition json), so we can run MUCH more efficiently if we keep a cache of clients, all equipped with automatically refreshing sessions.
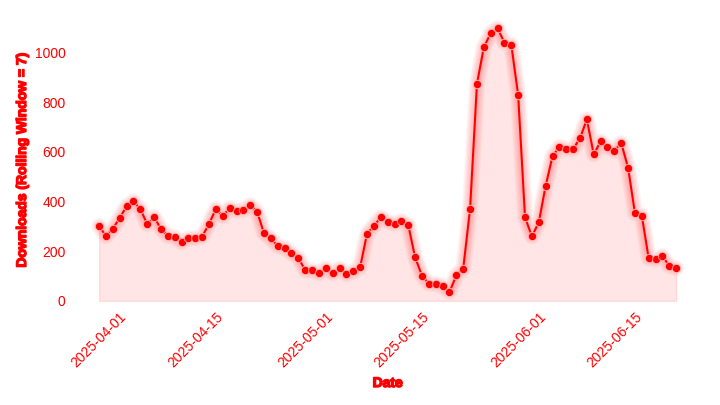
The following line plot illustrates the adoption of BRS over the last three months in terms of average daily downloads over a rolling seven day window.
pip install boto3-refresh-session
import boto3_refresh_session as brs
# you can pass all of the params associated with boto3.session.Session
profile_name = '<your-profile-name>'
region_name = 'us-east-1'
...
# as well as all of the params associated with STS.Client.assume_role
assume_role_kwargs = {
'RoleArn': '<your-role-arn>',
'RoleSessionName': '<your-role-session-name>',
'DurationSeconds': '<your-selection>',
...
}
# as well as all of the params associated with STS.Client, except for 'service_name'
sts_client_kwargs = {
'region_name': region_name,
...
}
# basic initialization of boto3.session.Session
session = brs.RefreshableSession(
assume_role_kwargs=assume_role_kwargs, # required
sts_client_kwargs=sts_client_kwargs,
region_name=region_name,
profile_name=profile_name,
...
)
# now you can create clients, resources, etc. without worrying about expired temporary
# security credentials
s3 = session.client(service_name='s3')
buckets = s3.list_buckets()
Long-running data pipelines, security tooling, ETL jobs, and cloud automation scripts frequently interact with the AWS API using boto3 — and often run into the same problem:
Temporary credentials expire.
When that happens, engineers typically fall back on one of two strategies:
Both approaches are fragile, tedious to maintain, and error-prone at scale.
Over the years, I noticed that every company I worked for — whether a scrappy startup or FAANG — ended up with some variation of the same pattern:
a small in-house module to manage credential refresh, written in haste, duplicated across services, and riddled with edge cases. Things only
got more strange and difficult when I needed to run things in parallel.
Eventually, I decided to build boto3-refresh-session as a proper open-source Python package:
The goal: to solve a real, recurring problem once — cleanly, consistently, and for everyone - with multiple refresh strategies.
If you've ever written the same AWS credential-refresh boilerplate more than once, this library is for you.
FAQs
A simple Python package for refreshing the temporary security credentials in a boto3.session.Session object automatically.
We found that boto3-refresh-session demonstrated a healthy version release cadence and project activity because the last version was released less than a year ago. It has 1 open source maintainer collaborating on the project.
Did you know?

Socket for GitHub automatically highlights issues in each pull request and monitors the health of all your open source dependencies. Discover the contents of your packages and block harmful activity before you install or update your dependencies.

Research
Security News
Socket researchers uncover how browser extensions in trusted stores are used to hijack sessions, redirect traffic, and manipulate user behavior.

Research
Security News
An in-depth analysis of credential stealers, crypto drainers, cryptojackers, and clipboard hijackers abusing open source package registries to compromise Web3 development environments.

Security News
pnpm 10.12.1 introduces a global virtual store for faster installs and new options for managing dependencies with version catalogs.