
Security News
Software Engineering Daily Podcast: Feross on AI, Open Source, and Supply Chain Risk
Socket CEO Feross Aboukhadijeh joins Software Engineering Daily to discuss modern software supply chain attacks and rising AI-driven security risks.
fire-eye-BCS
Advanced tools

A next-generation Firewall, CDN & WAF Fingerprinting Framework for Security Researchers, Bug Hunters, and Penetration Testers.
Built with ❤️ by BLACK ZERO
🚀 Powered by BANGLADESH CYBER SQUAD and TEAM SHADOW STRIKER
📆 Year: 2025
FIRE-EYE (fire-eye.py) is a Python3-based advanced security analysis framework that detects and fingerprints Web Application Firewalls (WAFs), CDNs, Load Balancers, and related security layers.
It provides flexible control through user-supplied signatures, regex header matching, and custom request headers — making it suitable for professional pentesters, SOC analysts, and researchers.
--user-list, --user-vendors-list)--header-search)--headers)--no-rotate-ua)python3 fire-eye.py <target> [options]
| Option | Description |
|---|---|
target | Target domain or URL (e.g., https://example.com) |
--headers "Key:Val;Key2:Val2" | Send custom request headers |
--header-search "<regex>" | Search for evidence in headers, cookies, or body |
--user-list <file> | Custom WAF/CDN/token signature list (JSON/simple format) |
--user-vendors-list <file> | Custom vendor list to merge with default |
--proxy <file> | File containing proxies (HTTP/SOCKS) |
--show-headers | Displays raw HTTP headers via curl |
--no-rotate-ua | Disable User-Agent rotation |
--report <path> | Save the output report to a custom file |
--json | Output in JSON format |
--debug | Enable debug logging |
pkg update && pkg install python3 git curl -y
git clone https://github.com/TEAMBCS/Fire-Eye.git
cd Fire-Eye
chmod +x *
pip3 install -r requirements.txt
python3 fire-eye.py -h
After installation, simply run:
python3 fire-eye.py --help
{
"MyCustomWAF": {
"manufacturer": "MyCompany",
"type": "WAF",
"headers": ["x-mycompany-id", "mycompany-waf"],
"cookies": ["MYCOMP_SESSION"],
"body": ["Access denied by MyCompany WAF"],
"server": ["mycompany"]
}
}
{
"vendors": [
"Cloudflare",
"Akamai",
"Fastly",
"AWS CloudFront",
"Imperva"
]
}
--headers and --header-search Work--headers
Format: "Key:Val;Key2:Val2"
Example:
--headers "User-Agent:Mozilla/5.0;Referer:https://google.com;Accept:*/*"
➤ The tool parses and attaches these headers to all requests.
--header-search
Searches inside headers, cookies, and response body for specific patterns using regex.
Example:
--header-search "(?i)cf-ray|x-amz-cf-id|incap_ses"
➤ Matches are displayed and logged in the report.
python3 fire-eye.py https://example.com
python3 fire-eye.py https://example.com \
--headers "User-Agent:MyCustomAgent;Referer:https://google.com" \
--header-search "(?i)cf-ray|x-amz-cf-id|fastly"
python3 fire-eye.py https://target.com \
--user-list user-list.json \
--user-vendors-list user-vendors-list.json
python3 fire-eye.py https://example.com --proxy proxy.txt --debug
python3 fire-eye.py https://example.com --json > result.json
python3 fire-eye.py https://example.com --report fire-eye.txt
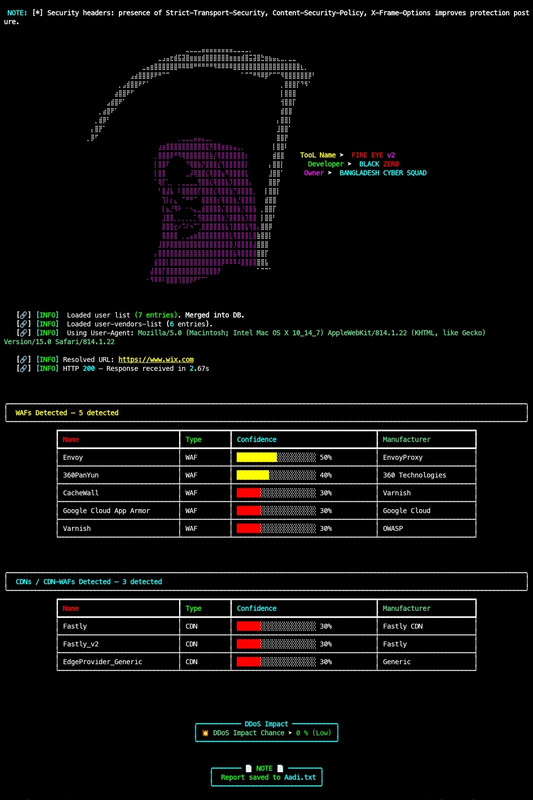
example_com_fireeye_<timestamp>.txt
| Library | Purpose |
|---|---|
requests | HTTP requests |
rich | Console styling |
pyfiglet | ASCII banners |
colorama | Terminal color support |
Install manually:
pip install requests rich pyfiglet colorama
This tool is for educational and authorized security testing only. Do not use it against any system or domain without proper permission.
Unauthorized scanning may violate laws or regulations.
MIT License Use responsibly and only for ethical security research.
FAQs
A powerful tool by BANGLADESH CYBER SQUAD
We found that fire-eye-BCS demonstrated a healthy version release cadence and project activity because the last version was released less than a year ago. It has 0 open source maintainers collaborating on the project.
Did you know?

Socket for GitHub automatically highlights issues in each pull request and monitors the health of all your open source dependencies. Discover the contents of your packages and block harmful activity before you install or update your dependencies.

Security News
Socket CEO Feross Aboukhadijeh joins Software Engineering Daily to discuss modern software supply chain attacks and rising AI-driven security risks.

Security News
GitHub has revoked npm classic tokens for publishing; maintainers must migrate, but OpenJS warns OIDC trusted publishing still has risky gaps for critical projects.

Security News
Rust’s crates.io team is advancing an RFC to add a Security tab that surfaces RustSec vulnerability and unsoundness advisories directly on crate pages.