
Security Fundamentals
Turtles, Clams, and Cyber Threat Actors: Shell Usage
The Socket Threat Research Team uncovers how threat actors weaponize shell techniques across npm, PyPI, and Go ecosystems to maintain persistence and exfiltrate data.
GraKeL is a library compatible with the project of scikit-learn
The GraKeL library requires:
You can install the dependencies as follows:
$ pip install extension>=extension_version
or
$ pip install -r requirements.txt
To install the development-version using pip execute:
$ pip install grakel-dev
Two pointers to get you started:
You first need to build the package's c++ extensions locally by executing:
$ python setup.py build_ext -i
To test the package, execute:
$ nosetests
For executing unit_tests or use a testing-interface for testing the kernel module:
$ python grakel/tests/test_kernels.py --help
usage: test_kernels.py [-h] [--verbose] [--problematic] [--slow]
[--ignore_warnings] [--dataset DATASET] [--normalize]
[--develop | --all | --main]
A test file for all kernels
optional arguments:
-h, --help show this help message and exit
--verbose print kernels with their outputs on stdout
--problematic allow execution of problematic test cases in development
--slow allow execution of slow test cases in development
--ignore_warnings ignore warnings produced by kernel executions
--dataset DATASET chose the datset you want the tests to be executed
--normalize normalize the kernel output
--develop execute only tests connected with current development
--all execute all tests
--main execute the main tests [default]
For testing graph_kernels:
$ python grakel/tests/test_graph_kernel.py --help
usage: test_graph_kernels.py [-h] [--verbose] [--problematic] [--slow]
[--normalize] [--ignore_warnings]
[--dataset DATASET] [--develop | --all | --main]
A test file for all kernels
optional arguments:
-h, --help show this help message and exit
--verbose print kernels with their outputs on stdout
--problematic allow execution of problematic test cases in development
--slow allow execution of slow test cases in development
--normalize normalize the kernel output
--ignore_warnings ignore warnings produced by kernel executions
--dataset DATASET chose the datset you want the tests to be executed
--develop execute only tests connected with current development
--all execute all tests
--main execute the main tests [default]
And for testing the Graph class:
$ python grakel/tests/test_graph.py --help
usage: test_graph.py [-h] [--verbose] [--ignore_warnings]
A test file for all `Graph` type objects
optional arguments:
-h, --help show this help message and exit
--verbose verbose outputs on stdout
--ignore_warnings ignore warnings produced by kernel executions
You can also execute the kernel test locally through a test-main-function as
$ python -m grakel.tests
To learn how to integrate your own kernel and how to contribute to the GraKeL project, please read the sections Write your own kernel and Contributing in the Documentation, respectively.
GraKeL comes with a BSD 3-clause license (as with scikit-learn). It contains the C++ source code of BLISS (a library for graph isomorphism) which is LGPL licensed. Futhermore its optional dependency in the package of cvxopt (a tool for solving convex-optimization problems) comes with a GPL license.
If you use GraKeL in a scientific publication, please cite our paper:
@article{siglidis2018grakel,
title={GraKeL: A Graph Kernel Library in Python},
author={Siglidis, Giannis and Nikolentzos, Giannis and Limnios, Stratis and Giatsidis, Christos and Skianis, Konstantinos and Vazirgiannis, Michalis},
journal={arXiv preprint arXiv:1806.02193},
year={2018}
}
FAQs
A scikit-learn compatible library for graph kernels
We found that grakel-dev demonstrated a healthy version release cadence and project activity because the last version was released less than a year ago. It has 1 open source maintainer collaborating on the project.
Did you know?

Socket for GitHub automatically highlights issues in each pull request and monitors the health of all your open source dependencies. Discover the contents of your packages and block harmful activity before you install or update your dependencies.

Security Fundamentals
The Socket Threat Research Team uncovers how threat actors weaponize shell techniques across npm, PyPI, and Go ecosystems to maintain persistence and exfiltrate data.

Security News
At VulnCon 2025, NIST scrapped its NVD consortium plans, admitted it can't keep up with CVEs, and outlined automation efforts amid a mounting backlog.
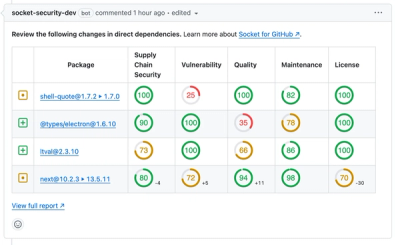
Product
We redesigned our GitHub PR comments to deliver clear, actionable security insights without adding noise to your workflow.