
Security Fundamentals
Turtles, Clams, and Cyber Threat Actors: Shell Usage
The Socket Threat Research Team uncovers how threat actors weaponize shell techniques across npm, PyPI, and Go ecosystems to maintain persistence and exfiltrate data.
NAPALM (Network Automation and Programmability Abstraction Layer with Multivendor support) is a Python library that implements a set of functions to interact with different router vendor devices using a unified API.

NAPALM supports several methods to connect to the devices, to manipulate configurations or to retrieve data.
Please check the following link to see which devices are supported. Make sure you understand the caveats.
Before using the library, please read the documentation at: Read the Docs
You can also watch a live demo of NAPALM to see what it is and what it can do for you.
pip install napalm
Note: Beginning with release 5.0.0 and later, NAPALM offers support for Python 3.8+ only.
Note: Beginning with release 4.0.0 and later, NAPALM offers support for Python 3.7+ only.
Note: Beginning with release 3.0.0 and later, NAPALM offers support for Python 3.6+ only.
We plan to upgrade napalm as fast as possible. Adding new methods and bugfixes. To upgrade napalm it's a simple as repeating the steps you performed while installing but adding the -U flag. For example:
pip install napalm -U
We will be posting news on our slack channel and on Twitter.
Due to its flexibility, NAPALM can be integrated in widely used automation frameworks.
Please check napalm-ansible for existing Ansible modules leveraging the NAPALM API. Make sure you read the documentation and you understand how it works before trying to use it.
Beginning with release code named Carbon (2016.11), NAPALM is fully integrated in SaltStack - no additional modules required. For setup recommendations, please see napalm-salt. For documentation and usage examples, you can check the modules documentation, starting from the release notes and this blog post.
NAPALM is usable from StackStorm using the NAPALM integration pack. See that repository for instructions on installing and configuring the pack to work with StackStorm. General StackStorm documentation can be found at https://docs.stackstorm.com/, and StackStorm can be easily spun up for testing using Vagrant or Docker.
Slack is probably the easiest way to get help with NAPALM. You can find us in the channel napalm on the network.toCode() team.
If you have any issues using NAPALM or encounter any errors, before submitting any questions (directly by email or on Slack), please go through the following checklist:
$ napalm --vendor VENDOR --user USERNAME --password PASSWORD --optional_args OPTIONAL_ARGS HOSTNAME call get_facts
Where vendor, username, password and hostname are mandatory. Optional arguments are specified as comma separated values.
Example:
$ napalm --vendor junos --user napalm --password dbejmujz --optional_args 'port=12202, config_lock=False' edge01.bjm01 call get_facts
In case you have any errors, please review the steps above - this looks like a problem with your environment setup.
In order to get help faster, when submitting a bug/error make sure to include all the details requested.
This project is maintained by David Barroso, Mircea Ulinic, and Kirk Byers and a set of other contributors.
Originally it was hosted by the Spotify organization but due to the many contributions received by third parties we agreed creating a dedicated organization for NAPALM and give a big thanks to Spotify for the support.
FAQs
Network Automation and Programmability Abstraction Layer with Multivendor support
We found that napalm demonstrated a healthy version release cadence and project activity because the last version was released less than a year ago. It has 3 open source maintainers collaborating on the project.
Did you know?

Socket for GitHub automatically highlights issues in each pull request and monitors the health of all your open source dependencies. Discover the contents of your packages and block harmful activity before you install or update your dependencies.

Security Fundamentals
The Socket Threat Research Team uncovers how threat actors weaponize shell techniques across npm, PyPI, and Go ecosystems to maintain persistence and exfiltrate data.

Security News
At VulnCon 2025, NIST scrapped its NVD consortium plans, admitted it can't keep up with CVEs, and outlined automation efforts amid a mounting backlog.
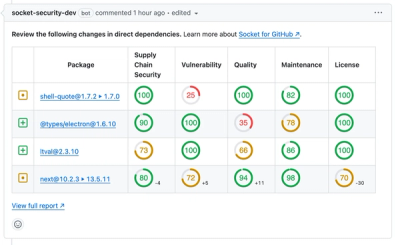
Product
We redesigned our GitHub PR comments to deliver clear, actionable security insights without adding noise to your workflow.