
Product
Rust Support Now in Beta
Socket's Rust support is moving to Beta: all users can scan Cargo projects and generate SBOMs, including Cargo.toml-only crates, with Rust-aware supply chain checks.
A very small library that parses a yaml configuration file and it resolves the environment variables, so that no secrets are kept in text.
pip install pyaml-env
This yaml file:
database:
name: test_db
username: !ENV ${DB_USER}
password: !ENV ${DB_PASS}
url: !ENV 'http://${DB_BASE_URL}:${DB_PORT}'
given that we've set these:
export $DB_USER=super_secret_user
export $DB_PASS=extra_super_secret_password
export $DB_BASE_URL=localhost
export $DB_PORT=5432
becomes this:
from pyaml_env import parse_config
config = parse_config('path/to/config.yaml')
print(config)
# outputs the following, with the environment variables resolved
{
'database': {
'name': 'test_db',
'username': 'super_secret_user',
'password': 'extra_super_secret_password',
'url': 'http://localhost:5432',
}
}
BaseConfigWhich can also become this:
from pyaml_env import parse_config, BaseConfig
config = BaseConfig(parse_config('path/to/config.yaml'))
# you can then access the config properties as atrributes
# I'll explain why this might be useful in a bit.
print(config.database.url)
:You can also set default values for when the environment variables are not set for some reason,
using the default_sep kwarg (which is : by default) like this:
databse:
name: test_db
username: !ENV ${DB_USER:paws}
password: !ENV ${DB_PASS:meaw2}
url: !ENV 'http://${DB_BASE_URL:straight_to_production}:${DB_PORT}'
And if no environment variables are found then we get:
from pyaml_env import parse_config
config = parse_config('path/to/config.yaml')
print(config)
{
'database': {
'name': 'test_db',
'username': 'paws',
'password': 'meaw2',
'url': 'http://straight_to_production:N/A',
}
}
NOTE 0: Special characters like *, { etc. are not currently supported as separators. Let me know if you'd like them handled also.
NOTE 1: If you set tag to None, then, the current behavior is that environment variables in all places in the yaml will be resolved (if set).
# because this is not allowed:
# data1: !TAG !!float ${ENV_TAG2:27017}
# use tag:yaml.org,2002:datatype to convert value:
test_data = '''
data0: !TAG ${ENV_TAG1}
data1: !TAG tag:yaml.org,2002:float ${ENV_TAG2:27017}
data2: !!float 1024
data3: !TAG ${ENV_TAG2:some_value}
data4: !TAG tag:yaml.org,2002:bool ${ENV_TAG2:false}
'''
Will become:
os.environ['ENV_TAG1'] = "1024"
config = parse_config(data=test_data, tag='!TAG')
print(config)
{
'data0': '1024',
'data1': 27017.0,
'data2': 1024.0,
'data3': 'some_value',
'data4': False
}
N/A as default_value:If no defaults are found and no environment variables, the default_value (which is N/A by default) is used:
{
'database': {
'name': 'test_db',
'username': 'N/A',
'password': 'N/A',
'url': 'http://N/A:N/A',
}
}
Which, of course, means something went wrong and we need to set the correct environment variables.
If you want this process to fail if a default value is not found, you can set the raise_if_na flag to True.
For example:
test1:
data0: !TEST ${ENV_TAG1:has_default}/somethingelse/${ENV_TAG2:also_has_default}
data1: !TEST ${ENV_TAG2}
will raise a ValueError because data1: !TEST ${ENV_TAG2} there is no default value for ENV_TAG2 in this line.
The default yaml loader is yaml.SafeLoader. If you need to work with serialized Python objects,
you can specify a different loader.
So given a class:
class OtherLoadTest:
def __init__(self):
self.data0 = 'it works!'
self.data1 = 'this works too!'
Which has become a yaml output like the following using yaml.dump(OtherLoadTest()):
!!python/object:__main__.OtherLoadTest
data0: it works!
data1: this works too!
You can use parse_config to load the object like this:
import yaml
from pyaml_env import parse_config
other_load_test = parse_config(path='path/to/config.yaml', loader=yaml.UnsafeLoader)
print(other_load_test)
<__main__.OtherLoadTest object at 0x7fc38ccd5470>
If you’ve worked with Python projects, you’ve probably have stumbled across the many ways to provide configuration. I am not going to go through all the ways here, but a few of them are:
using .ini files
using a python class
using .env files
using JSON or XML files
using a yaml file
And so on. I’ve put some useful links about the different ways below, in case you are interested in digging deeper.
My preference is working with yaml configuration because I usually find very handy and easy to use and I really like that yaml files are also used in e.g. docker-compose configuration so it is something most are familiar with.
For yaml parsing I use the PyYAML Python library.
In this article we’ll talk about the yaml file case and more specifically what you can do to avoid keeping your secrets, e.g. passwords, hosts, usernames etc, directly on it.
Let’s say we have a very simple example of a yaml file configuration:
database:
name: database_name
user: me
password: very_secret_and_complex
host: localhost
port: 5432
ws:
user: username
password: very_secret_and_complex_too
host: localhost
When you come to a point where you need to deploy your project, it is not really safe to have passwords and sensitive data in a plain text configuration file lying around on your production server. That’s where **environment variables **come in handy. So the goal here is to be able to easily replace the very_secret_and_complex password with input from an environment variable, e.g. DB_PASS, so that this variable only exists when you set it and run your program instead of it being hardcoded somewhere.
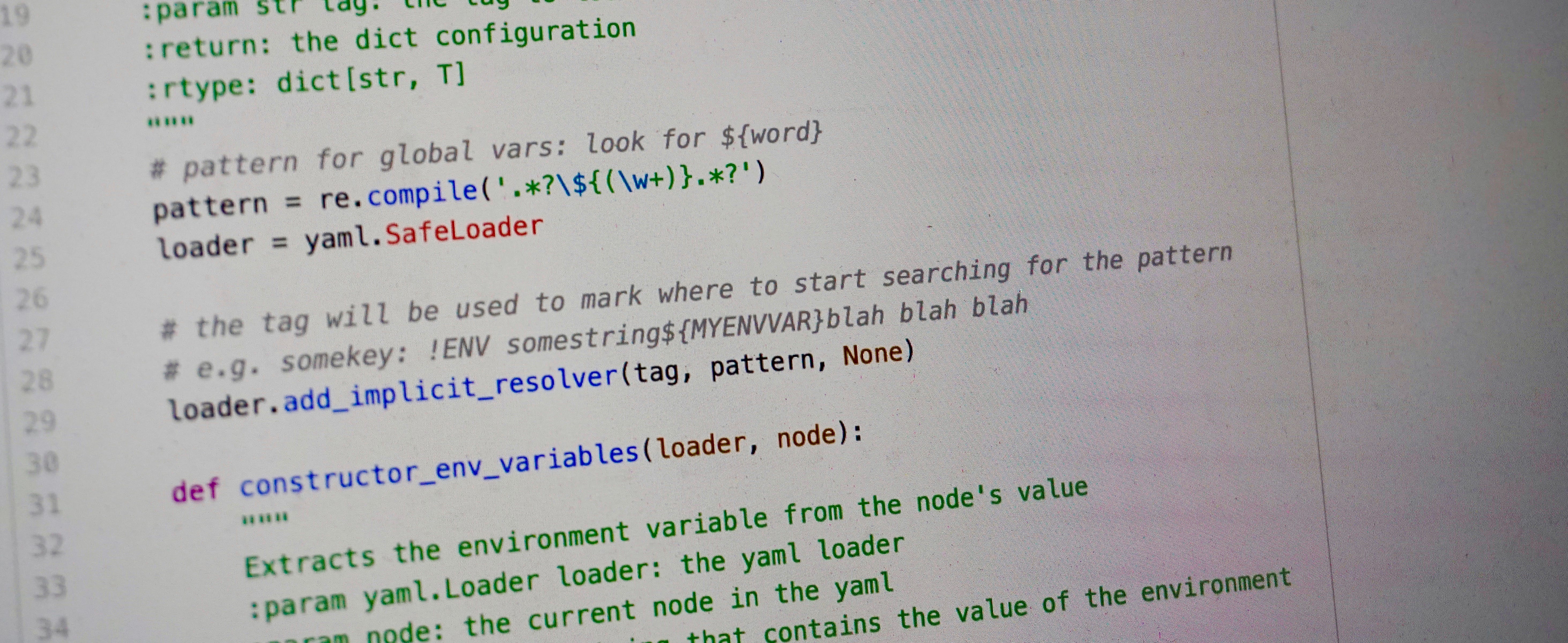
For PyYAML to be able to resolve environment variables, we need three main things:
A regex pattern for the environment variable identification e.g. pattern = re.compile(‘.?${(\w+)}.?’)
A tag that will signify that there’s an environment variable (or more) to be parsed, e.g. !ENV.
And a function that the loader will use to resolve the environment variables
def constructor_env_variables(loader, node):
"""
Extracts the environment variable from the node's value
:param yaml.Loader loader: the yaml loader
:param node: the current node in the yaml
:return: the parsed string that contains the value of the environment
variable
"""
value = loader.construct_scalar(node)
match = pattern.findall(value)
if match:
full_value = value
for g in match:
full_value = full_value.replace(
f'${{{g}}}', os.environ.get(g, g)
)
return full_value
return value
Example of a YAML configuration with environment variables:
database:
name: database_name
user: !ENV ${DB_USER}
password: !ENV ${DB_PASS}
host: !ENV ${DB_HOST}
port: 5432
ws:
user: !ENV ${WS_USER}
password: !ENV ${WS_PASS}
host: !ENV ‘[https://${CURR_ENV}.ws.com.local'](https://${CURR_ENV}.ws.com.local')
This can also work with more than one environment variables declared in the same line for the same configuration parameter like this:
ws:
user: !ENV ${WS_USER}
password: !ENV ${WS_PASS}
host: !ENV '[https://${CURR_ENV}.ws.com.](https://${CURR_ENV}.ws.com.local')[${MODE}](https://${CURR_ENV}.ws.com.local')' # multiple env var
And how to use this:
First set the environment variables. For example, for the DB_PASS :
export DB_PASS=very_secret_and_complex
Or even better, so that the password is not echoed in the terminal:
read -s ‘Database password: ‘ db_pass
export DB_PASS=$db_pass
# To run this:
# export DB_PASS=very_secret_and_complex
# python use_env_variables_in_config_example.py -c /path/to/yaml
# do stuff with conf, e.g. access the database password like this: conf['database']['DB_PASS']
if __name__ == '__main__':
parser = argparse.ArgumentParser(description='My awesome script')
parser.add_argument(
"-c", "--conf", action="store", dest="conf_file",
help="Path to config file"
)
args = parser.parse_args()
conf = parse_config(path=args.conf_file)
Then you can run the above script:
python use_env_variables_in_config_example.py -c /path/to/yaml
And in your code, do stuff with conf, e.g. access the database password like this: conf['database']['DB_PASS']
I hope this was helpful. Any thoughts, questions, corrections and suggestions are very welcome :)
The Many Faces and Files of Python Configs *As we cling harder and harder to Dockerfiles, Kubernetes, or any modern preconfigured app environment, our dependency…*hackersandslackers.com 4 Ways to manage the configuration in Python *I’m not a native speaker. Sorry for my english. Please understand.*hackernoon.com Python configuration files *A common need when writing an application is loading and saving configuration values in a human-readable text format…*www.devdungeon.com Configuration files in Python *Most interesting programs need some kind of configuration: Content Management Systems like WordPress blogs, WikiMedia…*martin-thoma.com
FAQs
Provides yaml file parsing with environment variable resolution
We found that pyaml-env demonstrated a healthy version release cadence and project activity because the last version was released less than a year ago. It has 1 open source maintainer collaborating on the project.
Did you know?

Socket for GitHub automatically highlights issues in each pull request and monitors the health of all your open source dependencies. Discover the contents of your packages and block harmful activity before you install or update your dependencies.

Product
Socket's Rust support is moving to Beta: all users can scan Cargo projects and generate SBOMs, including Cargo.toml-only crates, with Rust-aware supply chain checks.

Product
Socket Fix 2.0 brings targeted CVE remediation, smarter upgrade planning, and broader ecosystem support to help developers get to zero alerts.

Security News
Socket CEO Feross Aboukhadijeh joins Risky Business Weekly to unpack recent npm phishing attacks, their limited impact, and the risks if attackers get smarter.