
Security Fundamentals
Turtles, Clams, and Cyber Threat Actors: Shell Usage
The Socket Threat Research Team uncovers how threat actors weaponize shell techniques across npm, PyPI, and Go ecosystems to maintain persistence and exfiltrate data.
With zero configuration, vula automatically encrypts IP communication between hosts on a local area network in a forward-secret and transitionally post-quantum manner to protect against passive eavesdropping.
With manual key verification and/or automatic key pinning and manual resolution of IP or hostname conflicts, vula will additionally protect against interception by active adversaries.
When the local gateway to the internet is also vula peer, internet-destined traffic will also be encrypted on the LAN.
Automatically.
Vula combines WireGuard for forward-secret point-to-point tunnels with mDNS and DNS-SD for local service announcements, and enhances the confidentiality of WireGuard tunnels by using CTIDH implemented by highctidh, a post-quantum non-interactive key exchange primitive, to generate a peer-wise pre-shared key for each tunnel configuration.
Vula's advantages over some other solutions include:
See NOTES.md for
some discussion of the threat model and other technical details, and
COMPARISON.md
for a comparison of Vula to some related projects.
Vula is functional today, although it has some known issues documented in
STATUS.md. It is
ready for daily use by people who are proficient with Linux networking and the
command line, but we do not yet recommend it for people who are not.
See INSTALL.md for
installation and usage instructions.
See HACKING.md for
some tips on opening the hood.
See DEPENDENCY.md for diagrams illustrating the different
dependecy relationships between internal and external python modules.
We consider this project to currently be alpha pre-release, experimental, research quality code. It is not yet suitable for widespread deployment. It has not yet been audited by an independent third party and it should be treated with caution.
If you or someone you know finds a security issue - please open an
issue or feel free to send an email
to security at vula dot link.
Our current bug bounty for security issues is humble. We will treat qualifying reporters to a beverage after the COVID-19 crisis has ended; ojalá. Locations limited to qualifying CCC events such as the yearly Congress.
The authors of vula are anonymous for now, while our paper is undergoing peer review.
OPERATION_VULA.md
has some history about the name Vula.
Vula is not associated with or endorsed by the WireGuard project. WireGuard is a registered trademark of Jason A. Donenfeld.
This project is funded through the NGI Assure Fund, a fund established by NLnet with financial support from the European Commission's Next Generation Internet program. Learn more on the NLnet project page.
FAQs
Automatic local network encryption
We found that vula demonstrated a healthy version release cadence and project activity because the last version was released less than a year ago. It has 1 open source maintainer collaborating on the project.
Did you know?

Socket for GitHub automatically highlights issues in each pull request and monitors the health of all your open source dependencies. Discover the contents of your packages and block harmful activity before you install or update your dependencies.

Security Fundamentals
The Socket Threat Research Team uncovers how threat actors weaponize shell techniques across npm, PyPI, and Go ecosystems to maintain persistence and exfiltrate data.

Security News
At VulnCon 2025, NIST scrapped its NVD consortium plans, admitted it can't keep up with CVEs, and outlined automation efforts amid a mounting backlog.
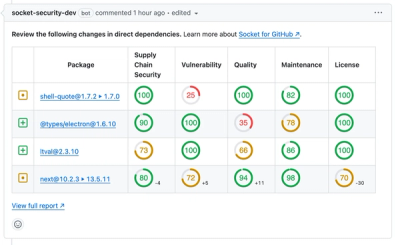
Product
We redesigned our GitHub PR comments to deliver clear, actionable security insights without adding noise to your workflow.