Debug access
Severity
Low
Short Description
Uses debug, reflection and dynamic code execution features.
Suggestion
Removing the use of debug will reduce the risk of any reflection and dynamic code execution.
Information
Debugging and dynamic code execution features, such as eval, Function(), or reflection APIs, can pose potential risks, including:
- Code Injection Vulnerabilities: If inputs are not sanitized, attackers may execute arbitrary code.
- Increased Attack Surface: Dynamic features can make it harder to audit and control the flow of execution.
- Exposure of Sensitive Information: Debugging tools might expose critical information about the application or its environment.
While these tools are useful during development or in specific runtime scenarios, their use in production code should be limited or removed entirely to improve security and maintainability.
Recommended actions
Review the Package Code:
- Inspect the package source code for instances of debugging, reflection, or dynamic code execution (e.g.,
eval,Function(), or similar APIs). - Ensure that the usage of these features is justified and poses no risk to your application.
Contact the Maintainer:
- If debugging or dynamic features appear unnecessary, reach out to the package maintainer for clarification.
- Request removal or replacement of these features in future releases.
Consider Alternatives:
- Evaluate whether the package is essential for your project.
- Search for alternatives that do not use risky debugging or dynamic execution features, or have a better security profile.
Use Secure Build Practices:
- Remove or strip debug-related code during your build process to avoid deploying it to production.
- Use minification or tree-shaking techniques to remove unused or unsafe debugging features from the package.
Validate Inputs:
- If dynamic execution features (like
eval) cannot be removed, ensure all inputs are sanitized and validated to mitigate risks of code injection.
Document Usage:
- Clearly document why this package is being used despite its use of debug features.
- Outline the specific mitigation steps you've implemented to reduce associated risks.
Remove if Necessary:
- If the package's use of debug or dynamic execution poses significant risks and cannot be mitigated, consider removing it from your dependency tree.
Examples
Here is an example of a package flagged for Debug Access due to the use of the vm module. While the vm module offers some isolation, it does not fully protect against malicious code or side-channel attacks. It could potentially allow dynamic code execution increases the attack surface, especially if user-provided scripts are not properly validated or sanitized.
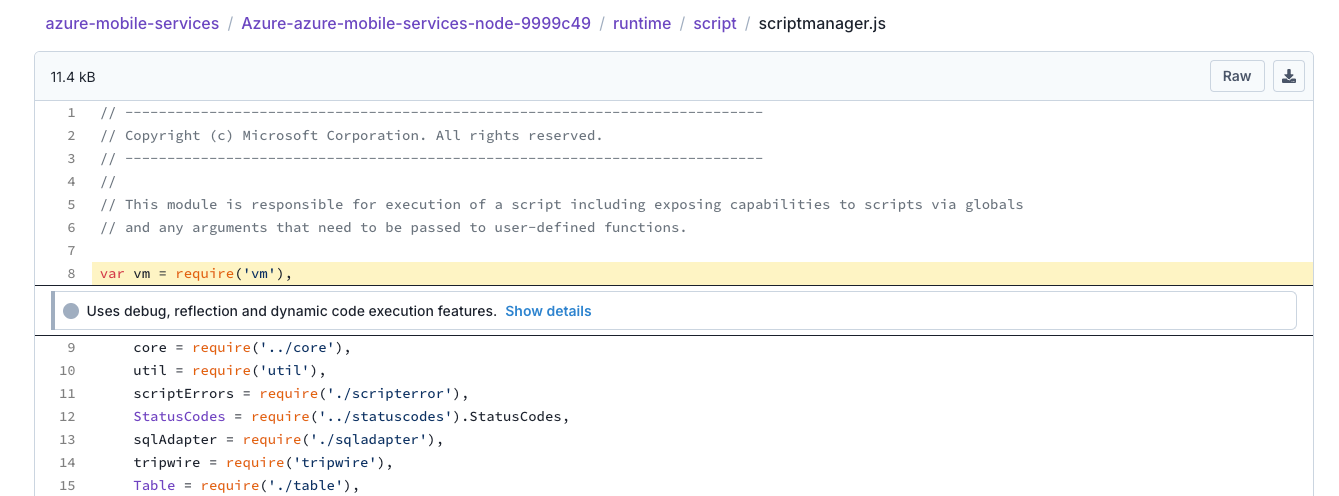
Detection Method
Packages are flagged with the Debug Access alert when they use debug, reflection, and dynamic code execution features.