
Product
Introducing Socket Firewall Enterprise: Flexible, Configurable Protection for Modern Package Ecosystems
Socket Firewall Enterprise is now available with flexible deployment, configurable policies, and expanded language support.


Martin Torp
September 9, 2025
Security teams today face an overwhelming flood of newly disclosed CVEs. Most organizations don’t have the time, resources, or appetite for risk to patch every single one. Fixing CVEs often means upgrading dependencies and exposing applications to breaking changes. The reality is that not every vulnerability actually matters to your application.
That’s why we’re excited to announce Tier 1 Reachability (Full Application Reachability), now available for enterprise teams using Socket. This new capability provides unmatched precision in filtering out irrelevant CVEs, giving teams the context they need to focus on the vulnerabilities that matter most.
Reachability analysis dramatically reduces noise by identifying which CVEs are actually exploitable in your application. Instead of being buried under thousands of alerts, teams can prioritize only the vulnerabilities proven to be reachable.
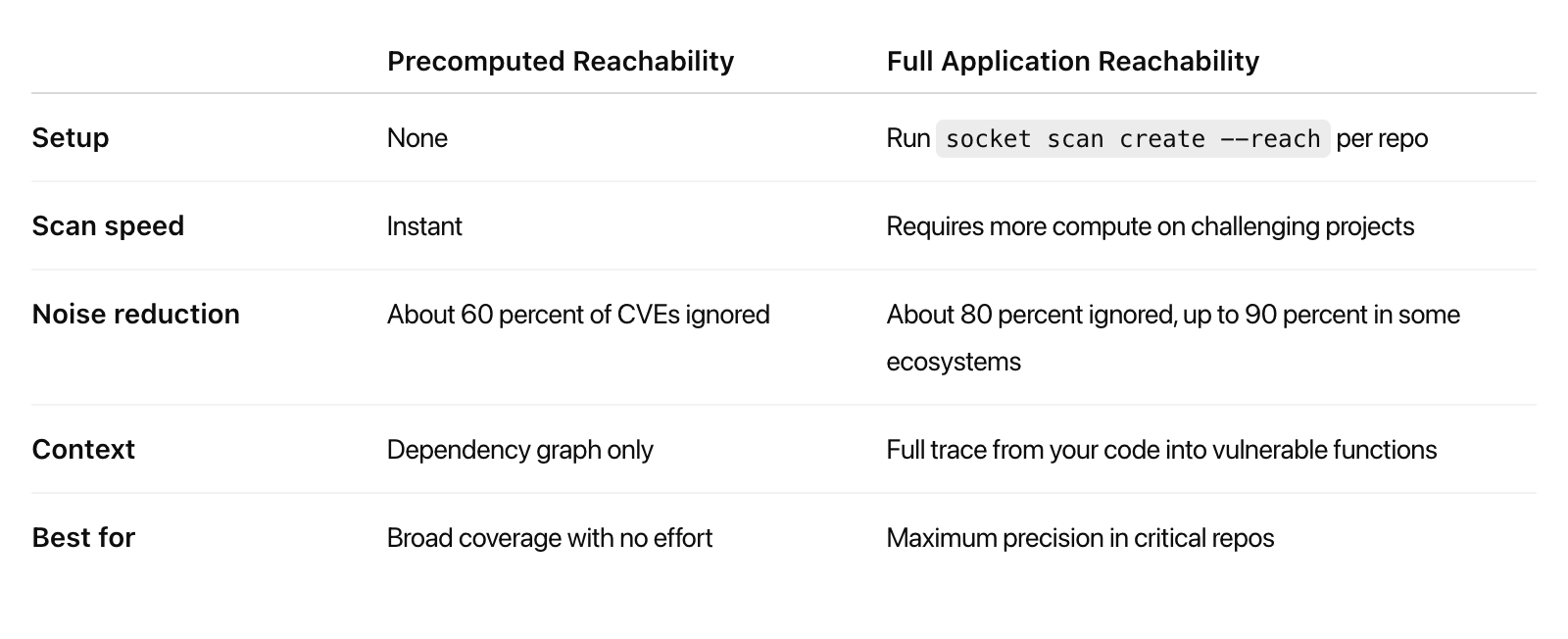
With Socket’s precomputed reachability, we’ve already been able to eliminate around 60% of vulnerability noise across codebases. Tier 1 Reachability takes this a step further, typically filtering out about 80% of vulnerabilities as irrelevant, with some ecosystems seeing noise reduction rates above 90%.
When we introduced precomputed reachability in July, it was a breakthrough. Precomputed analysis requires no setup, runs instantly, and never touches your source code. By analyzing only your dependency graph, it can usually mark about 60% of CVEs as unreachable. This makes it the ideal option for teams that want meaningful noise reduction with zero effort.
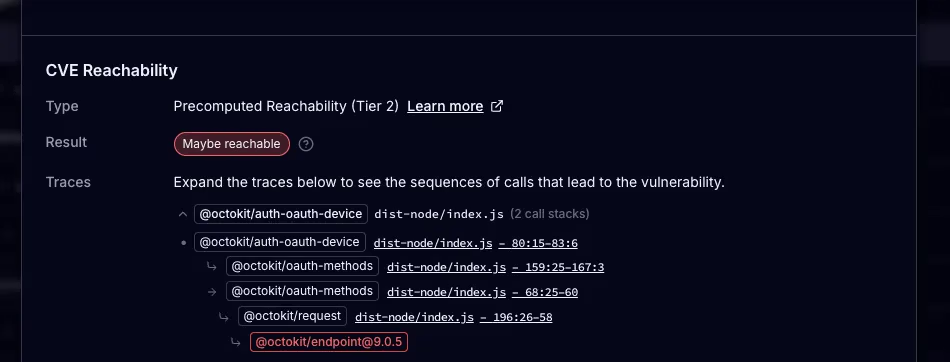
Full application reachability goes deeper for teams that need maximum precision. It scans both your application code and your dependencies to deliver stronger noise reduction, typically around 80 percent and in some ecosystems more than 90 percent. It also shows you the exact location in your source code where a vulnerability can be reached, providing a clear trace from your application into the vulnerable function.
The trade-off is that full application reachability requires a little setup and more compute. You need to run socket scan create --reach in each repository, and scans may take several minutes on large projects.
For many organizations the best approach is to combine the two. Use precomputed reachability everywhere by default, and run full application reachability in your most critical or sensitive repositories.
Tier 1 Reachability is built on based on state-of-the-art analysis technology developed at Aarhus University and validated with large enterprise customers for years. Here is how it works:
The analysis is intentionally over-approximating. When in doubt, it marks a CVE as reachable or unknown rather than risk missing an exploitable path.
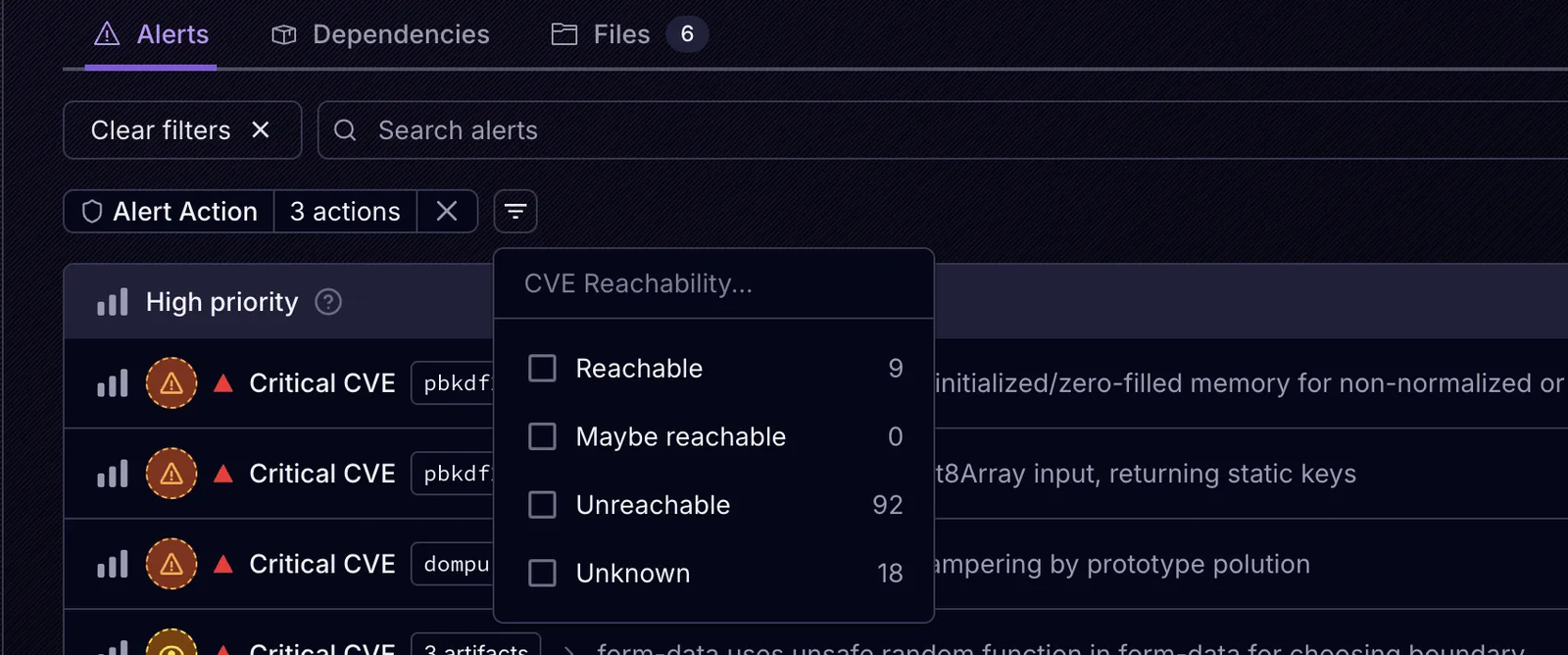
In the Socket UI you can filter vulnerability results by reachability, instantly surfacing only the issues that require attention.
The CVE Reachability Filter lets you toggle between reachable and unreachable vulnerabilities.
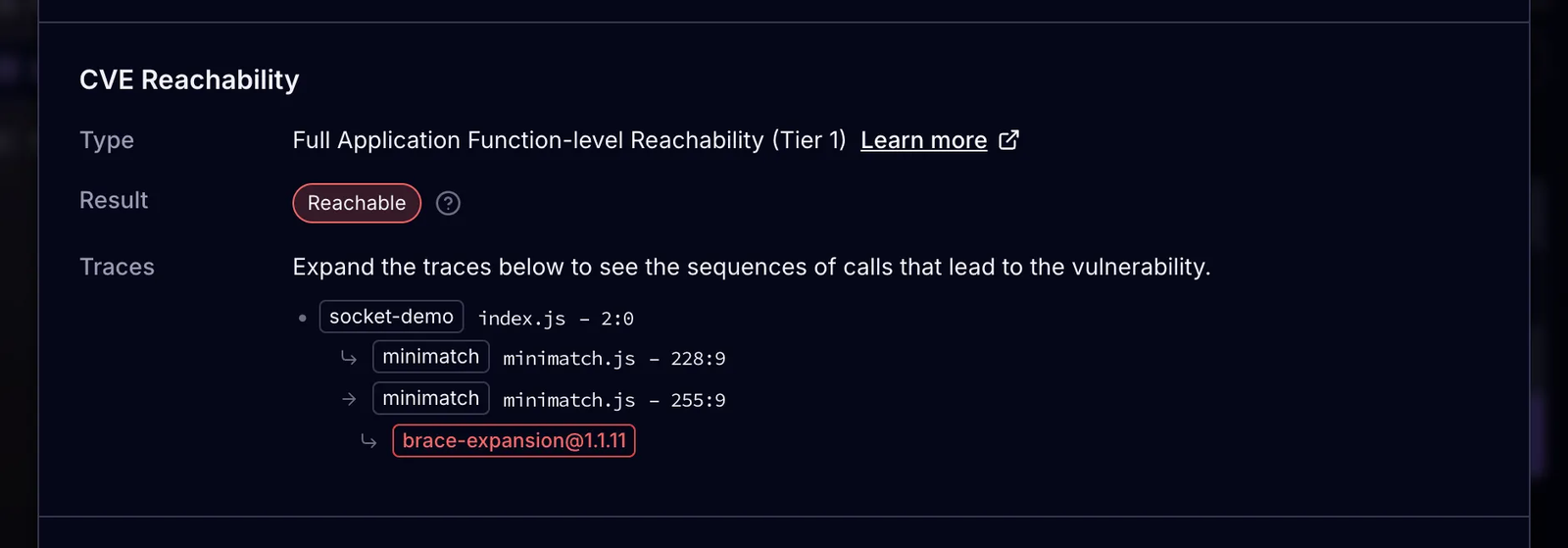
Trace View shows the exact function call path from your application into the vulnerable dependency.
The alert modal displays the trace of function calls from the index.ts file in the socket-demo project through a couple of functions in the minimatch package and then finally to the vulnerable function in the brace-expansion package.
This level of visibility turns triage into a straightforward and evidence-based process.
Tier 1 Reachability launches with support for JavaScript and TypeScript, Python, Go, Java, and .NET. Support for Rust, Ruby, Scala, and Kotlin will arrive later this quarter.
Our JVM and .NET engines can analyze both source and bytecode. This makes it possible to scan applications without building them, something no other vendor currently offers.
Socket's reachability technology has already been deployed successfully by many organizations, including a Fortune 50 customer now rolling it out across their enterprise. Today, we're making Tier 1 Reachability available to all enterprise plan customers.
If your organization is already on our enterprise plan, you can start using it right away:
socket scan create --reach
For setup details, see the documentation.
With Tier 1 Reachability, security teams can move past the flood of CVEs and focus on the vulnerabilities that pose real risks to their applications. By combining advanced static analysis with practical triage tools, Socket is setting a new standard for precision vulnerability management.
If you are interested in bringing Tier 1 Reachability to your team, book a demo with us to see it in action and learn more about upgrading to an enterprise plan.
Subscribe to our newsletter
Get notified when we publish new security blog posts!
Try it now

Product
Socket Firewall Enterprise is now available with flexible deployment, configurable policies, and expanded language support.

Product
Detect malware, unsafe data flows, and license issues in GitHub Actions with Socket’s new workflow scanning support.

Product
Add real-time Socket webhook events to your workflows to automatically receive pull request scan results and security alerts in real time.