
Security News
curl Shuts Down Bug Bounty Program After Flood of AI Slop Reports
A surge of AI-generated vulnerability reports has pushed open source maintainers to rethink bug bounties and tighten security disclosure processes.
Introduction | Installation | Quick start


The KPM CLI will be deprecated after v0.8.0, and the KPM CLI will be replaced by the KCL CLI - https://github.com/kcl-lang/cli.
The affected parts are shown below:
kpm
├── pkg
│ ├── api
│ ├── client
│ ├── cmd # The KPM CLI will deprecated after v0.8.0.
│ ├── constants
│ ├── env
│ ├── errors
│ ├── git
│ ├── oci
│ ├── opt
│ ├── package
│ ├── reporter
│ ├── runner
│ ├── semver
│ ├── settings
│ ├── utils
│ └── version
├── scripts
├── test
│ └── e2e # The e2e test for KPM CLI will deprecated after v0.8.0.
├── ......
kpm is the KCL package manager. kpm downloads your KCL package's dependencies, compiles your KCL packages, makes packages, and uploads them to the kcl package registry.
kpm will call KCL compiler to compile the kcl program. Before using kpm, you need to ensure that KCL compiler is installed successfully.
For more information about how to install KCL.
Use the following command to ensure that you install KCL compiler successfully.
kcl -v
kpmYou can download kpm via go install.
go install kcl-lang.io/kpm@latest
If the command kpm can not be found after executing the above command, please refer to:
You can also get kpm from the github release and set the kpm binary path to the environment variable PATH.
# KPM_INSTALLATION_PATH is the path of the `kpm` binary.
export PATH=$KPM_INSTALLATION_PATH:$PATH
Use the following command to ensure that you install kpm successfully.
kpm --help
If you get the following output, you have successfully installed kpm and you can proceed to the following steps.

Create a new kcl package named my_package. And after we have created the package my_package, we need to go inside the package by cd my_package to complete the following operations.
kpm init my_package

kpm will create two kcl package configuration files: kcl.mod and kcl.mod.lock in the directory where you executed the command.
- my_package
|- kcl.mod
|- kcl.mod.lock
|- # You can write your kcl program directly in this directory.
kcl.mod.lock is the file generated by kpm to fix the dependency version. Do not modify this file manually.
kpm initializes kcl.mod for an empty project as shown below:
[package]
name = "my_package"
edition = "0.0.1"
version = "0.0.1"
You can then add a dependency to the current kcl package using the kpm add command
As shown below, taking the example of adding a package dependency named k8s, the version of the package is 1.27.
kpm add k8s:1.27

You can see that kpm adds the dependency you just added to kcl.mod.
[package]
name = "my_package"
edition = "0.0.1"
version = "0.0.1"
[dependencies]
k8s = "1.27" # The dependency 'k8s' with version '1.27'
k8sCreate the main.k file in the current package.
- my_package
|- kcl.mod
|- kcl.mod.lock
|- main.k # Your KCL program.
And write the following into the main.k file.
# Import and use the contents of the external dependency 'k8s'.
import k8s.api.core.v1 as k8core
k8core.Pod {
metadata.name = "web-app"
spec.containers = [{
name = "main-container"
image = "nginx"
ports = [{containerPort = 80}]
}]
}
kpm compile the kcl packageIn the my_package directory, you can use kpm to compile the main.k file you just wrote.
kpm run

Beginning in kpm v0.2.0, you can use container registries with OCI support to store and share kcl packages.
For more information about OCI registry support.
go install to install kpm, but I get the error command not found.go install will install the binary file to $GOPATH/bin by default. You need to add $GOPATH/bin to the environment variable PATH.FAQs
Unknown package
Did you know?

Socket for GitHub automatically highlights issues in each pull request and monitors the health of all your open source dependencies. Discover the contents of your packages and block harmful activity before you install or update your dependencies.

Security News
A surge of AI-generated vulnerability reports has pushed open source maintainers to rethink bug bounties and tighten security disclosure processes.
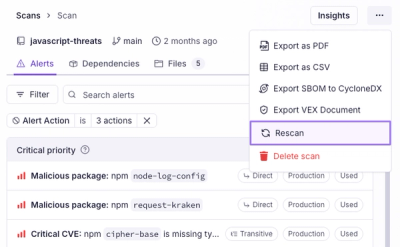
Product
Scan results now load faster and remain consistent over time, with stable URLs and on-demand rescans for fresh security data.
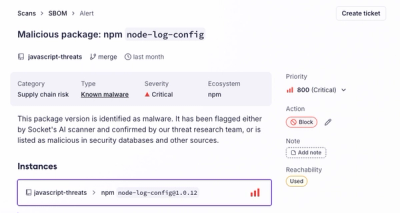
Product
Socket's new Alert Details page is designed to surface more context, with a clearer layout, reachability dependency chains, and structured review.