Security News
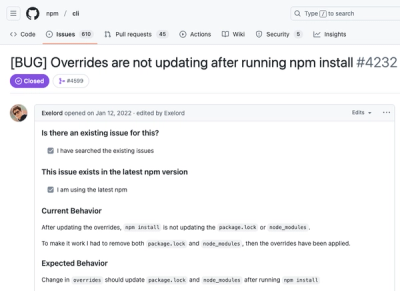
Socket and Seal Security Collaborate to Fix Critical npm Overrides Bug
Socket and Seal Security collaborate to fix a critical npm overrides bug, resolving a three-year security issue in the JavaScript ecosystem's most popular package manager.









