
Security News
Rust RFC Proposes a Security Tab on crates.io for RustSec Advisories
Rust’s crates.io team is advancing an RFC to add a Security tab that surfaces RustSec vulnerability and unsoundness advisories directly on crate pages.
@ibm/itest
Advanced tools
The IBM i Testing CLI (itest) is a companion to the IBM i Testing VS Code extension, which allows you to run unit tests and generate code coverage results for RPG and COBOL programs on IBM i. With this CLI, you can run tests in your terminal on your local PC or in PASE on IBM i. This enables you to even script the execution of tests in a CI/CD pipeline.
This CLI can be used on your local PC or directly on IBM i. In either case, it can be installed globally via NPM:
npm i -g itest
Once installed, you can run the itest command in your terminal along with various options which configure what tests are run, the environment they are run in, how to run them, and what logs to generate. At a minimum, there are a few options that must be specified based on where you are running the command from and where your tests are located:
--ld, --local-directory [path] option to point to a local directory containing your test files and the --id, --ifs-directory [path] option to point to the IFS directory on your IBM i where the project will be deployed.--l, --library <library> option to point to a library on your IBM i containing your test members.--id, --ifs-directory [path] option to point to an IFS directory on your IBM i containing your test files.--l, --library <library> option to point to a library on your IBM i containing your test members.Check out the examples section below for more details.
[!NOTE] If you are running the command on your local PC, you will be prompted to enter your IBM i connection details. Alternatively, you can set the following environment variables:
IBMI_HOST,IBMI_USER, andIBMI_PASSWORD(orIBMI_PRIVATE_KEYif using private key authentication).
Listed below are all the available options for the itest command. For convenience, use the itest --help command to see all these options and their descriptions directly in your terminal.
| Flag | Description |
|---|---|
--v, --version | Display the version number |
--ld, --local-directory [path] | Local directory containing tests (preset: ".") |
--id, --ifs-directory [path] | IFS directory containing containing tests or deploy directory (preset: ".") |
--l, --library <library> | Library containing tests. |
--sf, --source-files <sourceFiles...> | Source files to search for tests. (default: ["QTESTSRC"]) |
--ll, --library-list <libraries...> | Libraries to add to the library list. |
--cl, --current-library <library> | The current library to use for the test run. |
--cc, --code-coverage [ccLvl] | Run with code coverage (choices: "*LINE", "*PROC", preset: "*LINE") |
--ct, --coverage-thresholds <threshholds...> | Set the code coverage thresholds (yellow and green). (default: ["60","90"]) |
--sc, --skip-compilation | Skip compilation |
--sr, --summary-report [path] | Save summary report (preset: "./.itest/summary-report.md") |
--tr, --test-result [path] | Save test result logs (preset: "./.itest/test-result.log") |
--to, --test-output [path] | Save test output logs (preset: "./.itest/test-output.log") |
--co, --command-output [path] | Save command output logs (preset: "./.itest/command-output.log") |
--h, --help | Display help for command |
[!CAUTION] If you are using Git Bash on Windows, POSIX-style paths are automatically converted to Windows paths. This conversion can break the path > passed to the
--ifs-directoryoption. To prevent this, you have two options:
- Add an additional
/to the start of any relative or absolute POSIX path:itest --ld . --id //home/USER/builds/ibmi-company_system --ll RPGUNIT QDEVTOOLS --cl MYLIB --cc- Set the environment variable
MSYS_NO_PATHCONVto1:# Option A: Set the variable for your shell session export MSYS_NO_PATHCONV=1 itest --ld . --id /home/USER/builds/ibmi-company_system --ll RPGUNIT QDEVTOOLS --cl MYLIB --cc # Option B: Set the variable only for this command MSYS_NO_PATHCONV=1 itest --ld . --id /home/USER/builds/ibmi-company_system --ll RPGUNIT QDEVTOOLS --cl MYLIB --cc
Run tests in local directory:
itest --ld . --id /home/USER/builds/ibmi-company_system --ll RPGUNIT QDEVTOOLS --cl MYLIB --cc
This first example command will deploy the contents of the current directory on your PC to the specified IFS directory, setup both the library list and current library, and finally run all tests with code coverage.*
Run tests in IFS directory:
itest --id /home/USER/builds/ibmi-company_system --ll RPGUNIT QDEVTOOLS --cl MYLIB --cc
This second example is the exact same as the first one except it is run on your on IBM i because no local directory option is specified.
Run tests in library:
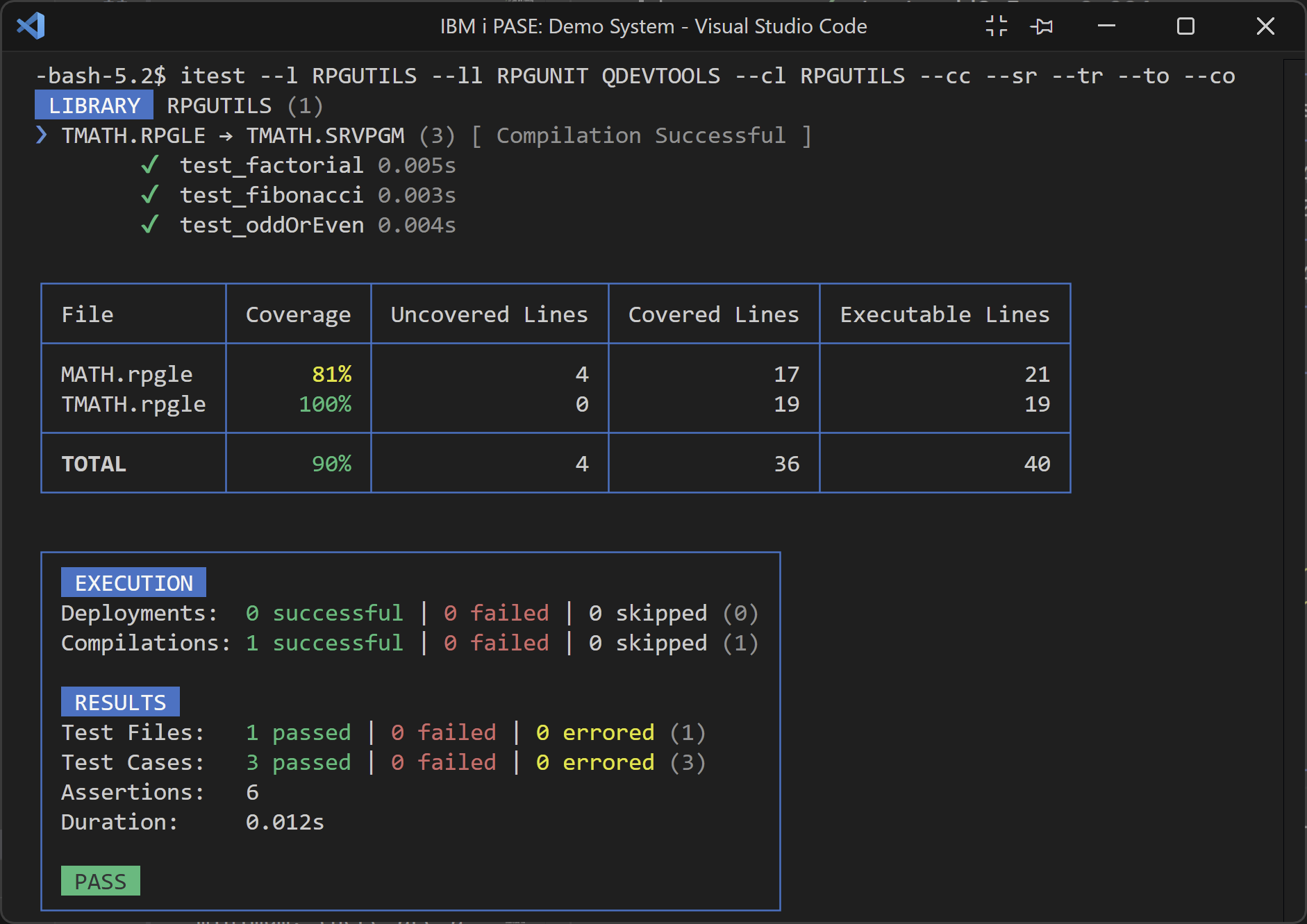
itest --l RPGUTILS --ll RPGUNIT QDEVTOOLS --cl RPGUTILS --cc
This third example is similar to the second except it will run tests in the specified library. This command can be run both on your local PC or IBM i.
Run tests in library (more customized):
itest --l RPGUTILS --ll RPGUNIT QDEVTOOLS --cl RPGUTILS --cc *PROC --ct 70 95 --sr --tr --to --co
This fourth example is similar to the third one except it generates procedure coverage, customizes the yellow and green coverage thresholds, and saves all logs to the default log directory (.itest).
There are various logs that can be generated by the CLI to help you understand the results of your tests and diagnose any failures or issues. By default, all logs are saved to the .itest in the current working directory, but you can customize the path for each log via the corresponding option. The following logs can be generated:
Code for IBM i output channel when running tests in VS Code.FAQs
IBM i Testing CLI
The npm package @ibm/itest receives a total of 0 weekly downloads. As such, @ibm/itest popularity was classified as not popular.
We found that @ibm/itest demonstrated a healthy version release cadence and project activity because the last version was released less than a year ago. It has 20 open source maintainers collaborating on the project.
Did you know?

Socket for GitHub automatically highlights issues in each pull request and monitors the health of all your open source dependencies. Discover the contents of your packages and block harmful activity before you install or update your dependencies.

Security News
Rust’s crates.io team is advancing an RFC to add a Security tab that surfaces RustSec vulnerability and unsoundness advisories directly on crate pages.

Security News
/Research
Socket found a Rust typosquat (finch-rust) that loads sha-rust to steal credentials, using impersonation and an unpinned dependency to auto-deliver updates.

Research
/Security Fundamentals
A pair of typosquatted Go packages posing as Google’s UUID library quietly turn helper functions into encrypted exfiltration channels to a paste site, putting developer and CI data at risk.