Security News
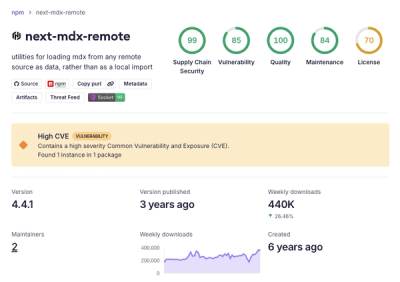
High-Severity RCE Vulnerability Disclosed in next-mdx-remote
HashiCorp disclosed a high-severity RCE in next-mdx-remote affecting versions 4.3.0 to 5.x when compiling untrusted MDX on the server.
@upstash/redis
Advanced tools
@upstash/redis is an HTTP/REST based Redis client for typescript, built on top
of Upstash REST API.
[!NOTE]
This project is in GA Stage.The Upstash Professional Support fully covers this project. It receives regular updates, and bug fixes. The Upstash team is committed to maintaining and improving its functionality.
It is the only connectionless (HTTP based) Redis client and designed for:
See the list of APIs supported.
npm install @upstash/redis
import { Redis } from "https://esm.sh/@upstash/redis";
Create a new redis database on upstash
import { Redis } from "@upstash/redis"
const redis = new Redis({
url: <UPSTASH_REDIS_REST_URL>,
token: <UPSTASH_REDIS_REST_TOKEN>,
})
// string
await redis.set('key', 'value');
let data = await redis.get('key');
console.log(data)
await redis.set('key3', 'value3', {ex: 1});
// sorted set
await redis.zadd('scores', { score: 1, member: 'team1' })
data = await redis.zrange('scores', 0, 100 )
console.log(data)
// list
await redis.lpush('elements', 'magnesium')
data = await redis.lrange('elements', 0, 100 )
console.log(data)
// hash
await redis.hset('people', {name: 'joe'})
data = await redis.hget('people', 'name' )
console.log(data)
// sets
await redis.sadd('animals', 'cat')
data = await redis.spop('animals', 1)
console.log(data)
We have a dedicated page for common problems. If you can't find a solution, please open an issue.
See the documentation for details.
Create a new redis database on upstash and copy the url and token
bun run test
bun run build
This library sends anonymous telemetry data to help us improve your experience. We collect the following:
You can opt out by setting the UPSTASH_DISABLE_TELEMETRY environment variable
to any truthy value.
UPSTASH_DISABLE_TELEMETRY=1
Alternatively, you can pass enableTelemetry: false when initializing the Redis client:
const redis = new Redis({
// ...,
enableTelemetry: false,
});
ioredis is a robust, full-featured Redis client for Node.js. It supports all Redis commands, including Pub/Sub and transactions, and provides high availability and cluster support. Compared to @upstash/redis, ioredis is more suitable for traditional server-based environments rather than serverless architectures.
redis is the official Redis client for Node.js. It provides a straightforward API for interacting with a Redis database and supports all standard Redis commands. While it is highly reliable and widely used, it does not offer the serverless-specific optimizations that @upstash/redis provides.
node-redis is another popular Redis client for Node.js. It offers a simple and efficient API for performing Redis operations and supports features like Pub/Sub and transactions. Similar to the official redis package, it is designed for traditional server environments rather than serverless setups.
FAQs
An HTTP/REST based Redis client built on top of Upstash REST API.
The npm package @upstash/redis receives a total of 1,309,839 weekly downloads. As such, @upstash/redis popularity was classified as popular.
We found that @upstash/redis demonstrated a healthy version release cadence and project activity because the last version was released less than a year ago. It has 8 open source maintainers collaborating on the project.
Did you know?

Socket for GitHub automatically highlights issues in each pull request and monitors the health of all your open source dependencies. Discover the contents of your packages and block harmful activity before you install or update your dependencies.

Security News
HashiCorp disclosed a high-severity RCE in next-mdx-remote affecting versions 4.3.0 to 5.x when compiling untrusted MDX on the server.

Security News
Security researchers report widespread abuse of OpenClaw skills to deliver info-stealing malware, exposing a new supply chain risk as agent ecosystems scale.

Security News
Claude Opus 4.6 has uncovered more than 500 open source vulnerabilities, raising new considerations for disclosure, triage, and patching at scale.