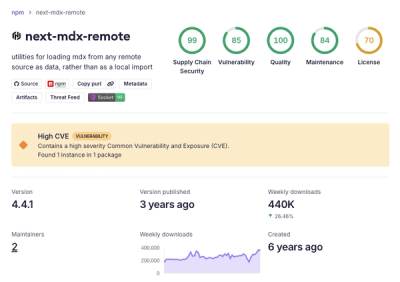
Security News
High-Severity RCE Vulnerability Disclosed in next-mdx-remote
HashiCorp disclosed a high-severity RCE in next-mdx-remote affecting versions 4.3.0 to 5.x when compiling untrusted MDX on the server.
incrementer
Advanced tools
This plugin extends an html input field which serves a number to be given. Handling validation and easy incrementing or decrementing of given value is provided.
[TOC]
You can simply download the compiled version as zip file here and inject it after needed dependencies:
#!HTML
<script src="https://code.jquery.com/jquery-3.1.0.js" integrity="sha256-slogkvB1K3VOkzAI8QITxV3VzpOnkeNVsKvtkYLMjfk=" crossorigin="anonymous"></script>
<script src="http://torben.website/clientNode/data/distributionBundle/index.compiled.js"></script>
<!--Inject downloaded file:-->
<script src="index.compiled.js"></script>
<!--Or integrate via cdn:
<script src="http://torben.website/incrementer/data/distributionBundle/index.compiled.js"></script>
-->
The compiled bundle supports AMD, commonjs, commonjs2 and variable injection into given context (UMD) as export format: You can use a module bundler if you want.
If you are using npm as package manager you can simply add this tool to your package.json as dependency:
#!JSON
...
"dependencies": {
...
"incrementer": "latest",
...
},
...
After updating your packages you can simply depend on this script and let a module bundler do the hard stuff or access it via an exported variable name in given context.
#!JavaScript
...
import Incrementer from 'incrementer'
class SpecialIncrementer extends Incrementer...
// or
import {$} from 'incrementer'
$('input').Incrementer()
class SpecialIncrementer extends $.Incrementer.class ...
// or
Incrementer = require('incrementer').default
value instanceof Incrementer
// or
$ = require('incrementer').$
$('input').Incrementer()
...
#!JavaScript
const dependenciesLoadPromise = $documentationWebsite.getScript(
'https://code.jquery.com/jquery-3.1.0.js'
).then(() => $.getScript(
'http://torben.website/clientNode/data/distributionBundle/' +
'index.compiled.js'
)).then(() => $.getScript(
'http://torben.website/incrementer/data/distributionBundle/' +
'index.compiled.js'))
#!CSS
body form div.incrementer > input.form-control {
width: 61px;
float: left;
}
body form div.incrementer > a.plus,
body form div.incrementer > a.minus {
font-size: 24px;
font-weight: bold;
margin: 10px;
}
#!JavaScript
dependenciesLoadPromise.then(() => $(
'body form.first input'
).Incrementer())
#!HTML
<form class="first" action="#">
<input name="test" value="4" class="form-control" />
</form>
#!HTML
<script>
dependenciesLoadPromise.then(() => {
$('body form.second input.first').Incrementer({
step: 2, minimum: 10, maximum: 20, logging: true
})
$('body form.second input.second').Incrementer({
step: 3, minimum: 5, maximum: 30, logging: true
})
})
</script>
<form class="second" action="#">
<input name="test" value="10" class="form-control first" />
<input name="test" value="12" class="form-control second" />
</form>
#!HTML
<script>
dependenciesLoadPromise.then(() => $(
'body form.third input'
).Incrementer({
onInvalidNumber: $.noop(),
onTypeInvalidLetter: $.noop(),
step: 1,
minimum: 0,
maximum: 9999,
domNode: {
plus: '> a.plus',
minus: '> a.minus'
},
neededMarkup: `
<a href="#" class="plus">+</a>
<a href="#" class="minus">-</a>
`
}))
</script>
<form class="third" action="#">
<input name="test" value="50" class="form-control" />
</form>
FAQs
> 指定开始值/结束值, 在指定时间内, 进行累加
The npm package incrementer receives a total of 0 weekly downloads. As such, incrementer popularity was classified as not popular.
We found that incrementer demonstrated a not healthy version release cadence and project activity because the last version was released a year ago. It has 1 open source maintainer collaborating on the project.
Did you know?

Socket for GitHub automatically highlights issues in each pull request and monitors the health of all your open source dependencies. Discover the contents of your packages and block harmful activity before you install or update your dependencies.

Security News
HashiCorp disclosed a high-severity RCE in next-mdx-remote affecting versions 4.3.0 to 5.x when compiling untrusted MDX on the server.

Security News
Security researchers report widespread abuse of OpenClaw skills to deliver info-stealing malware, exposing a new supply chain risk as agent ecosystems scale.

Security News
Claude Opus 4.6 has uncovered more than 500 open source vulnerabilities, raising new considerations for disclosure, triage, and patching at scale.